SSH Key
-
Is SSH key stored in the backup config file for restoration from backup? Last night, I tried to SSH in and permission denied although password was correct. System>User Manager>user/Admin SSH key box was empty. I am on pfSense 2.5-dev and had mine set to require both password and public key although I am accessing from LAN.
-
I didn't check, but something lights up in my head that says : " ..... nice catch".
using this :
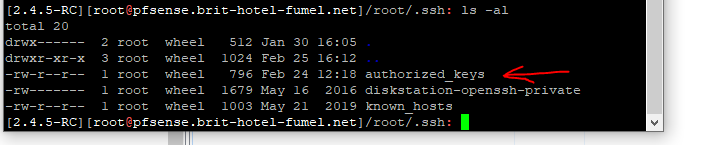
which contains the public key which does not get saved in the config.xml ..... (I'm really hoping I'm producing purely distilled bullshit right now)
Which means you have to fire up your favorite editor, edit saved config.xml to remove the Public key only setting, load the config, to regain access ( another 60 seconds lost ^^ )
Btw : you're using 2.5.0, that's quiet cutting edge .... things could be different.
-
@Gertjan It's saved per here see the image below...should had checked last night but still puzzled as to why I keep getting permission denied. I even tried an older laptop that was used to set up SSH on pfSense 2.4.
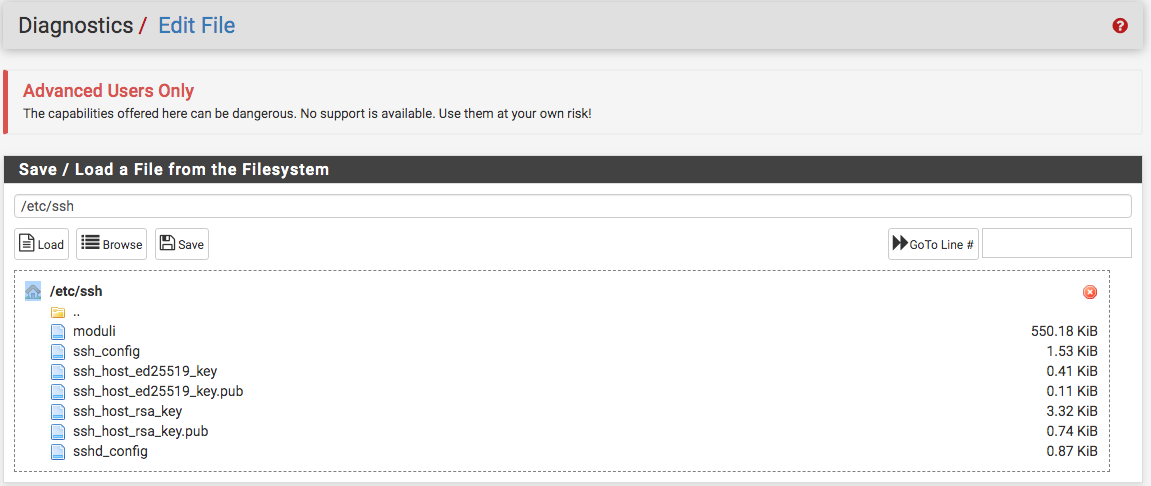
-
Which means you have to fire up your favorite editor, edit saved config.xml to remove the Public key only setting, load the config, to regain access
I should also have stated that if I change the setting to a password or public key, I can log in...no problem. So, do you think the key somehow gets contaminated making and restoring from backup?
-
The SSH keys pfSense uses are not stored in the config, they are regenerated when you restore it.
But any public keys you uploaded to you a user to allow them to connect to the firewall are.
It sounds like you're doing the later so I would expect it to connect.
Steve
-
@stephenw10 said in SSH Key:
The SSH keys pfSense uses are not stored in the config, they are regenerated when you restore it.
But any public keys you uploaded to you a user to allow them to connect to the firewall are.
It sounds like you're doing the later so I would expect it to connect.
Steve
Yes, that's what I expected; however, only using the password worked...the key is the issue.
-
Then the key must have changed somewhere. Can you check the config diff? Upload the key again?
You are testing in 2.5?
-
@stephenw10 said in SSH Key:
Then the key must have changed somewhere. Can you check the config diff? Upload the key again?
You are testing in 2.5?
That seems to be the conclusion...ended up just creating a new key...much easier than fiddling with copying the key from pfSense to Mac, although, I did attempt. Yes, I am testing V2.5 by running in production mode with Suricata on WAN and Snort on LAN both inline mode, Squid's ClamAV, and pfBlockerNG two months now. The stability is impressive!
-
I guess @stephenw10 put me on the right path :
Normally, I was generating the keys outside of pfSense, with tools like PuttyGEN.
Copying the public key into /root/.ssh/authorized_keys - switch "SSHd Key Only" to "Public key only" reboot sshd and Bob's your uncle.
Not the best method. -
You should never alter the user authorized_keys files on the filesystem directly. User keys must be saved in the user account in the GUI/config.xml or they'll get wiped out the next time pfSense syncs the user data to the disk.
-
Just found :
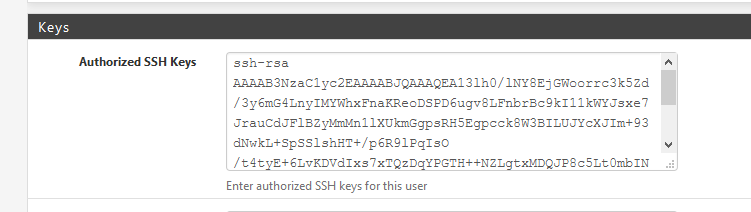
was overlooking this since .... the beginning.
edit : I knew it. It was "to manual". It's a click click thing.
-
Copying the public key into /root/.ssh/authorized_keys - switch "SSHd Key Only" to "Public key only" reboot sshd
Tried that last night but still got permission denied. So ended up just creating new key; however, maybe I would have had success had I paste the key in the user account in the GUI/config.xml as Jimp points out.
-
-
@NollipfSense said in SSH Key:
User keys must be saved in the user account in the GUI/config.xml
Jimp, if I scroll down and add key from another device, will that work to enable that device?
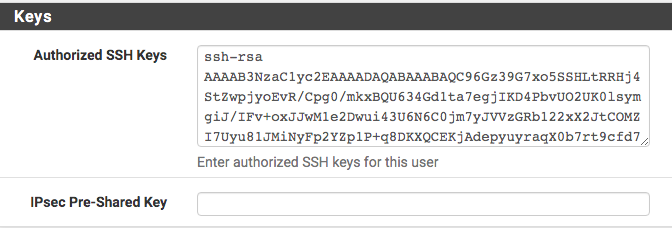
@jimp Never mind...it worked...now have two devices connecting SSH via key and password from LAN.
-
Yeah, as you found you can just add more keys below the first one.