IPSEC Routing & NAT - Unable to get it right
-
Hi all,
First of all I would like to mention that I am not a network expert. I work for a startup and as resources are still limited, I volunteered to give it a go, so apologies upfront if I say something stupid.
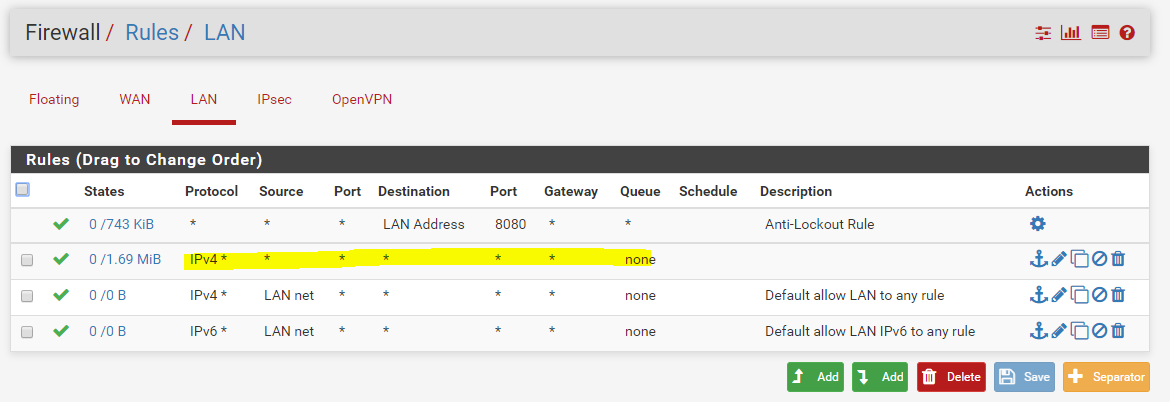
So how does our setup look like at this moment:
- Site A is our side
- Site B is customer side (that we don't control)
- An OpenVPN server is configured to have access to our LAN in Site A
- This is in place & working as I access the pfsense webgui from there
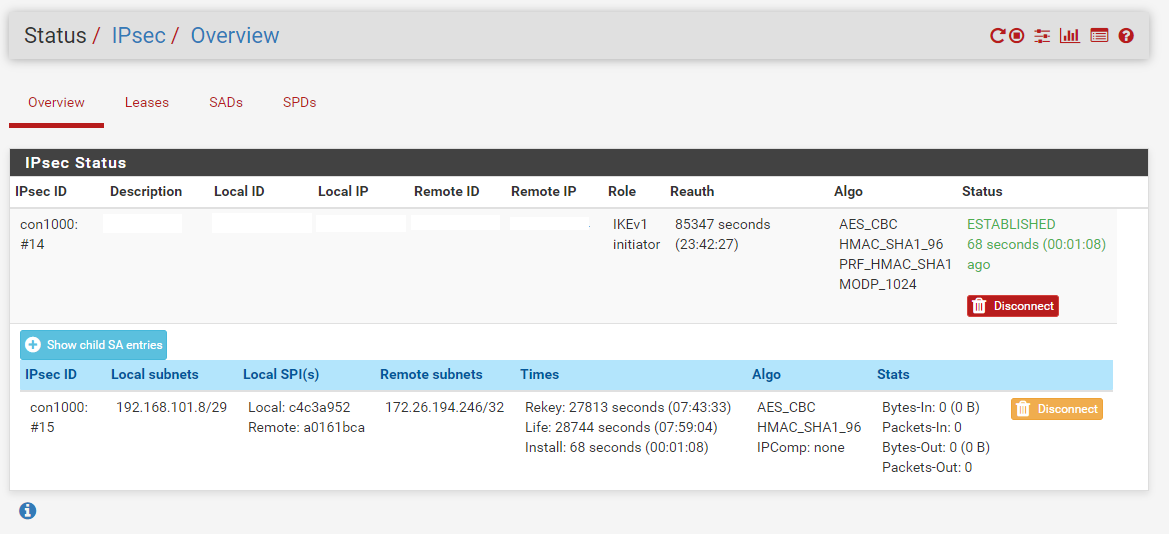
- An IPSEC tunnel between us & the customer is established
- So we have a connected status, but are unable to get traffic through the tunnel
What do we try to accomplish in this phase?
- We try to RDP from our OpenVPN client (eg: 10.0.8.2/24) to the remote customer 172.26.194.246/24
- Once this works, we need to work the other way around. Where the 172.26.194.246/24 host should be able to access the server at 192.168.0.x/24.
What have we configured?
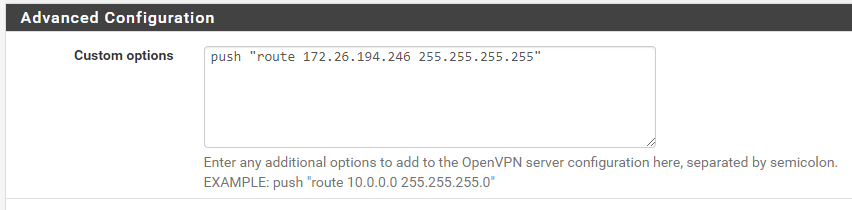
- A route to 172.26.194.246/24 is pushed into the route table of the OpenVPN client
- A firewall rule was added to allow any traffic from 10.0.8.0/24 to any destination
- An outbound NAT rule is created to translate traffic from 10.0.8.0/24 to 172.26.194.246/32 into subnet nat address 192.168.101.8/29 (the remote only allows traffic to/from the 192.168.101.8/29 subnet)
Important note: Our next customer would like to have a similar setup, but requires us to use a public IP in the encryption domain. So I think the setup should be similar for them, just the NAT rules should be different. Would this be a correct assumption?
Any advice/hints on what we should adapt/check to get this up and running?
Issues I could think off (but we are just not experienced enough to get it right):- Missing/wrong routes/firewall rules
- Wrong NAT config (outbound nat rules and/or phase NAT/BINAT)
- Mixed use of 172.26.194.246/24 & 172.26.194.246/32 in config
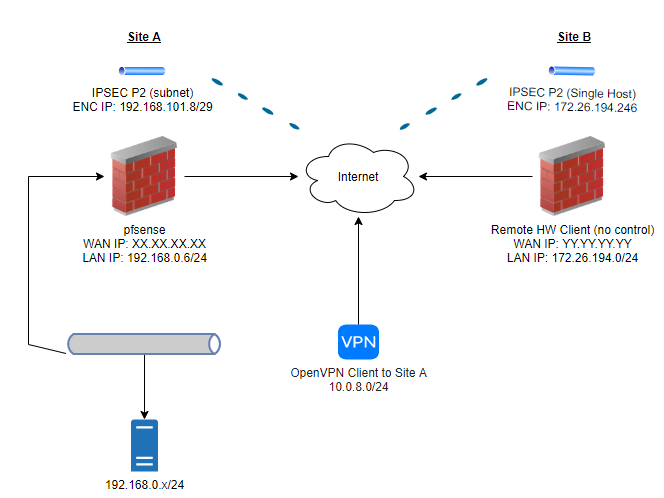
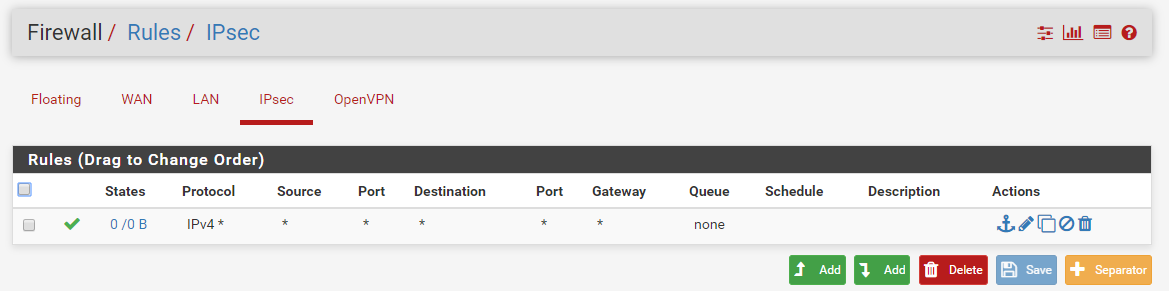
Some relevant (I believe) config screenshots:
Note: No BINAT/NAT configured
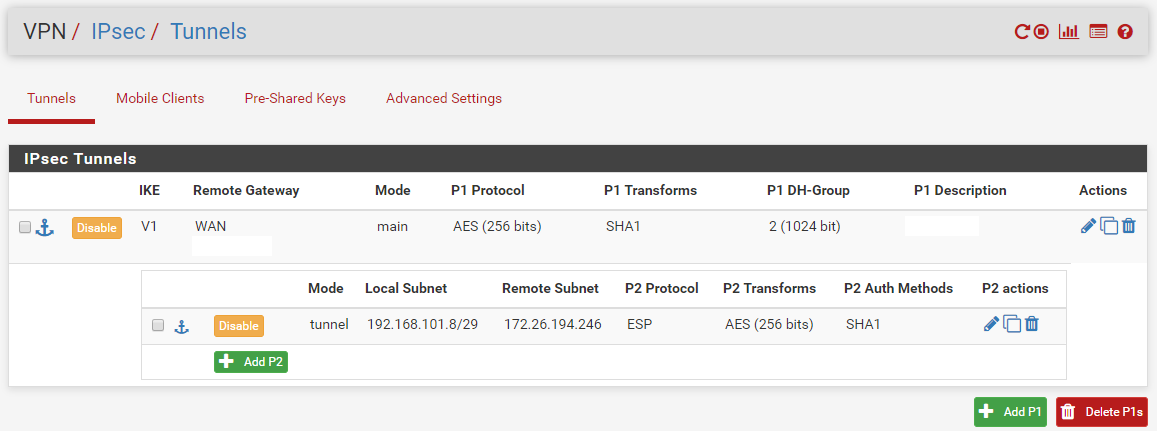
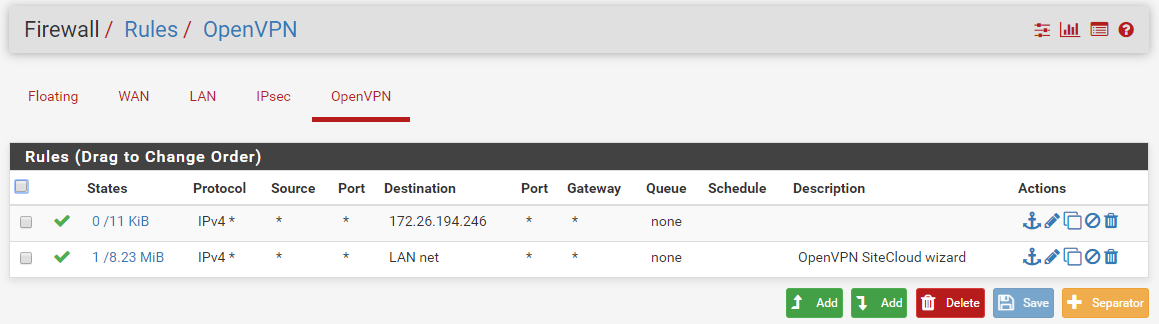
Note: Although disabled, this rule is enabled while testing (config varies while testing off course :)).
Note2: The removed "NAT address" alias is posted below this image. (Round Robin with Sticky address)
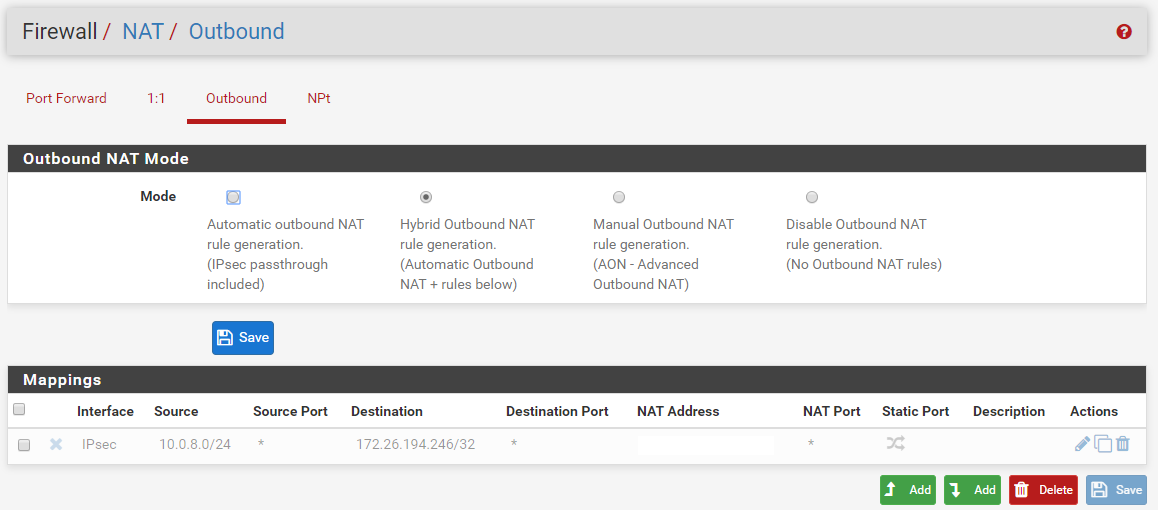
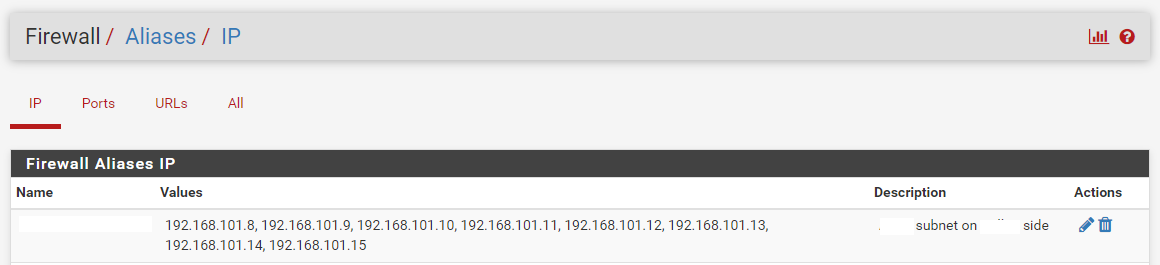
Note: An allow all on lan exists also at the time