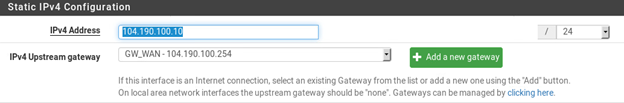
Enable internet access from LAN
-
@maale said in Enable internet access from LAN:
I am using the pfsense DNS resolver and other 2 external DNS servers
Not how it works - you are either resolving, or your using external dns via forwarding..
Your resolver is not working most likely because whatever network pfsense is on is prob blocking direct dns queries - and only allows access to googledns or whatever.
So change to forwarder mode..
-
@johnpoz
Thanks so much, now I can see the available package list -
@johnpoz
Because I am using the same domain name for my internal and external services, I have used the bind9 package to set split DNS as follows and it works fine to resolve inside LAN and outside. All services from outside have pfsense WAN address.
This is first zone file for internal addresses.

This is the second zone for external addresses.

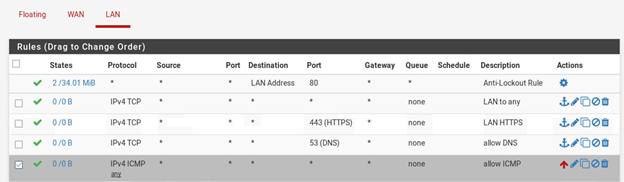
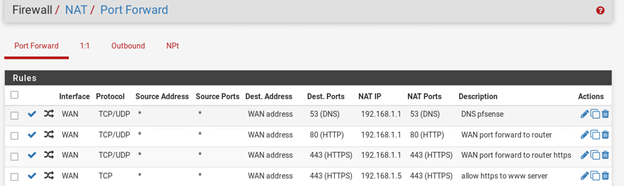
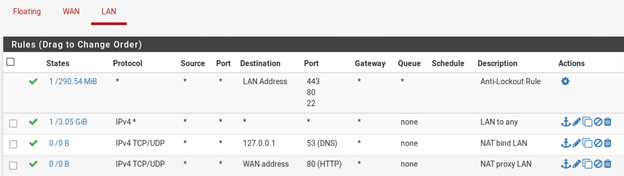
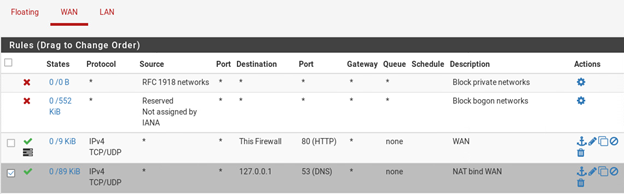
I also have set a NAT rule with destination= 127.0.0.1 port 53 in the LAN and WAN interfaces. So that split DNS works fine.
Because all services have pfsense WAN address I used the squid reverse proxy package with the web and mail servers at 192.168.1.5 and 192.168.1.35. I want www.x.av goes to the internal web server at 192.168.1.5 port 80. And https://mail.x.av goes to the mail server at 192.168.1.35 port 443 and 143.
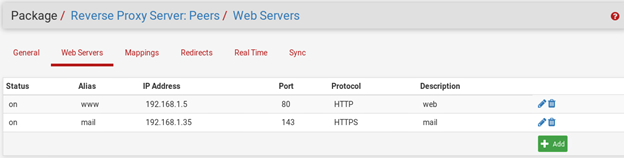
. I set a WAN rule with source any destion :this firewall port 80 so that the traffic goes to the squid reverse proxy. That doesnot work for me, from outside I cannot access any of the two servers! Could you please let me know what is wrong with this setting?
Thanks. -
You don't need bind to do split dns... And its at best problematic use the same domain internally as you do externally..
-
@johnpoz
so I can use the pfsense resolver and add hostoverides e.g www.x.av IP 104.x.x.10 ? or it is better to built an exteral dns for external quiries? -
What boxes exactly are going to be using pfsense as their dns? Your saying your going to make it the authoritative ns for your domain on the public internet? BAD IDEA!!
If your going to do that, then you would for sure have to setup different views..
-
@johnpoz
yes I have set up 2 zones with 2 views. Bind works fine, but my setting for the reverse squid proxy doesnot work. -
Not sure how your going to get port 143 to work... IMAP doesn't send headers that a proxy can look at to see where it should go, etc.. That would be port based normal forward.
You would use reverse proxy or ha proxy (reverse) for stuff that sends headers - http/https
-
Why are you port forwarding DNS to localhost?
Is that service on port 143 really https? Or IMAP which, as Jogn says, should not be proxied like that.
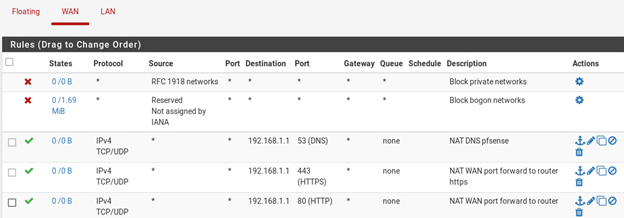
What is that NAT rule on WAN for port 80?
Many questions...still.

Steve
-
@stephenw10 said in Enable internet access from LAN:
What is that NAT rule on WAN for port 80?
That's easy : the GUI-from-WAN access rule.
-
@stephenw10
Why are you port forwarding DNS to localhost?
So that any internal or external DNS query will be directed to the local host since I am using bind.
What is that NAT rule on WAN for port 80?
I am using WAN rule source any destination: This firewall, port 80, so any traffic will be directed to the reverse proxy.
The mail service has many listening ports:25,110,143. I have a self signed certificate for that page HTTPS.
So in the setup for webservers on squid reverse proxy I set the protocol for mail server at 192.168.1.35 as HTTPS and the port is 143. is that wrong?
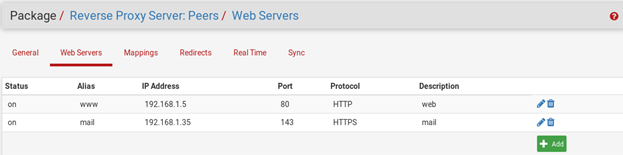
-
a self signed cert on a imap 143 port ?
imap 143 is the 'clear text' version. If you want to use TLS for IMAP you would be suing 993.
pop and TLS : 995
Mail clients that send mail should use 587 (TLS possible but now needed) or even better : 465.Port 25 : should be used only for inter mail server communication. This port was never intend to be used by mail clients. It's so wrong to do so.
Very soon, ports like 80, 110,143 (21) etc will be out of business for good.
Remember : you have a web site on port 80 ? Google won't index you any more.Btw : Modern 'fat' mail clients like Outlook don't even accept self signed certs any more. Maybe, if you imported the CA ans stamped it as 'trusted' you might get away with it.