[solved] HAproxy ssl offloading only for internal Lan
-
EDIT: no you do not need it !
after fixed your DNS Resolver pointin to the client and not to the pfS box
Do I really have to set up a virtual ip with
My Lan IP from pfS and tell HAproxy to listen on that ip. With a specified port eg 80 or 443Webgui redirect and port of pfS gui allready changed
BrNp
-
@noplan
Should not be needed.. -
huh?? What are you trying to accomplish exactly? Why would you be using HA proxy to access something internally?
-
used for
ssl offloading
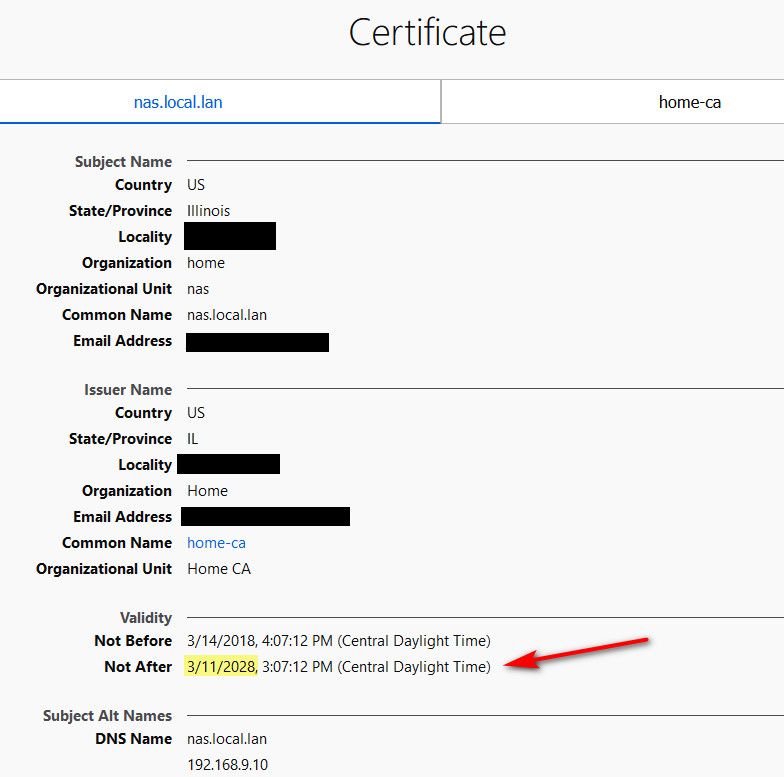
to get rid of that self signed cert error
i solved the issue (after pointing the hostname to the pfS IP and not the client IP in DNS reslover)
working with LE wildcard / haProxy and a pretty mean pfBlockerN conf on the box ;)
-
@noplan said in [solved] HAproxy ssl offloading only for internal Lan:
to get rid of that self signed cert error
Just install a non self signed on the actual server..
-
..... Hmmm Yeahhhhhhh..... Hmmmm
NoTooooo much fun doin it this way
And more money to spend for other fun things ;) -
What does money have to do with.. Just create whatever certs you want on pfsense. Can be any domain, any san (rf1918 addresses even) etc..
For that matter its local network - just use http ;)
-
Point taken, wasn't thinking about us in pfS for the certs...
Some stuff usese self signed per default
And Browser warning is annoying
U know there is something called
woman acceptance factor
On the frontend ;) -
So example - here my cisco switch.. Can use IP or Name and secure with no warning.
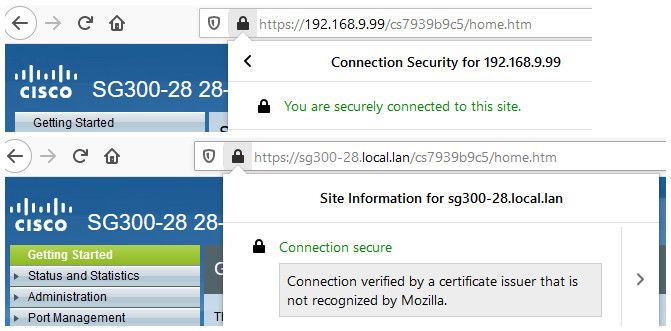
Until these browsers starting complaining about cert lifetime, just set it for 10 years and be done with it...
-
Thanks for the hint / tip
I ve never considered this as an option
-
It was much better before browsers started lowering the life of the cert.. You could set the cert to be good for 10 years or something and never have to worry about it again..
Now they want to have longest life of 398 days - uggghhhh.. Glad all my certs grandfathered in, hehehe And good for the 10 some years ;)