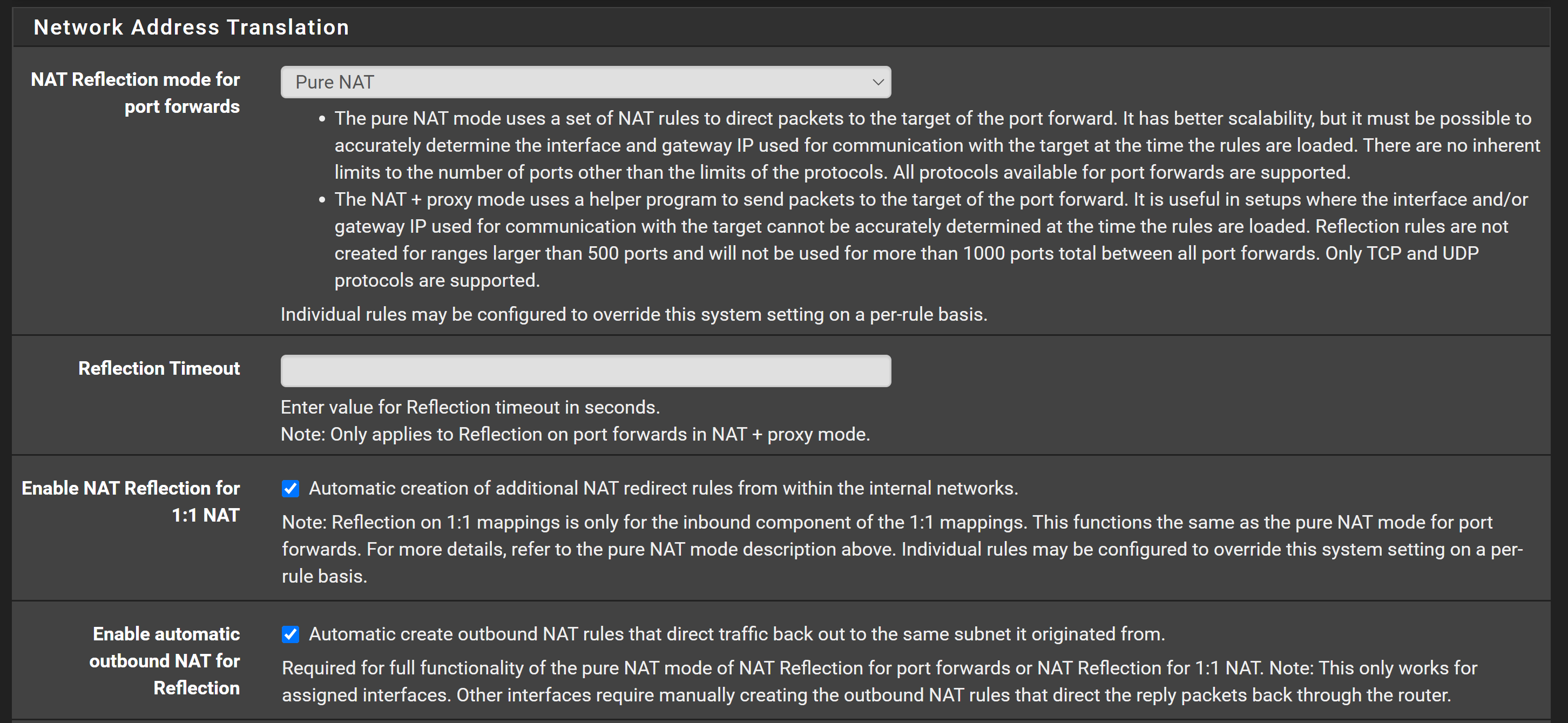
(SOLVED) NAT rule for WAN port from Firewall A w/ openvpn server to device behind Firewall B w/ openvpn client
-
Hello,
I am trying to setup a NAT rule for a WAN port from Firewall A to a device behind a Firewall B, where both Firewalls are connected with a site-to-site openvpn connection, being Firewall A the server, and Firewall B the client, but not sure why am not being able to do it till know, like I have been doing for local networks of Firewall A.
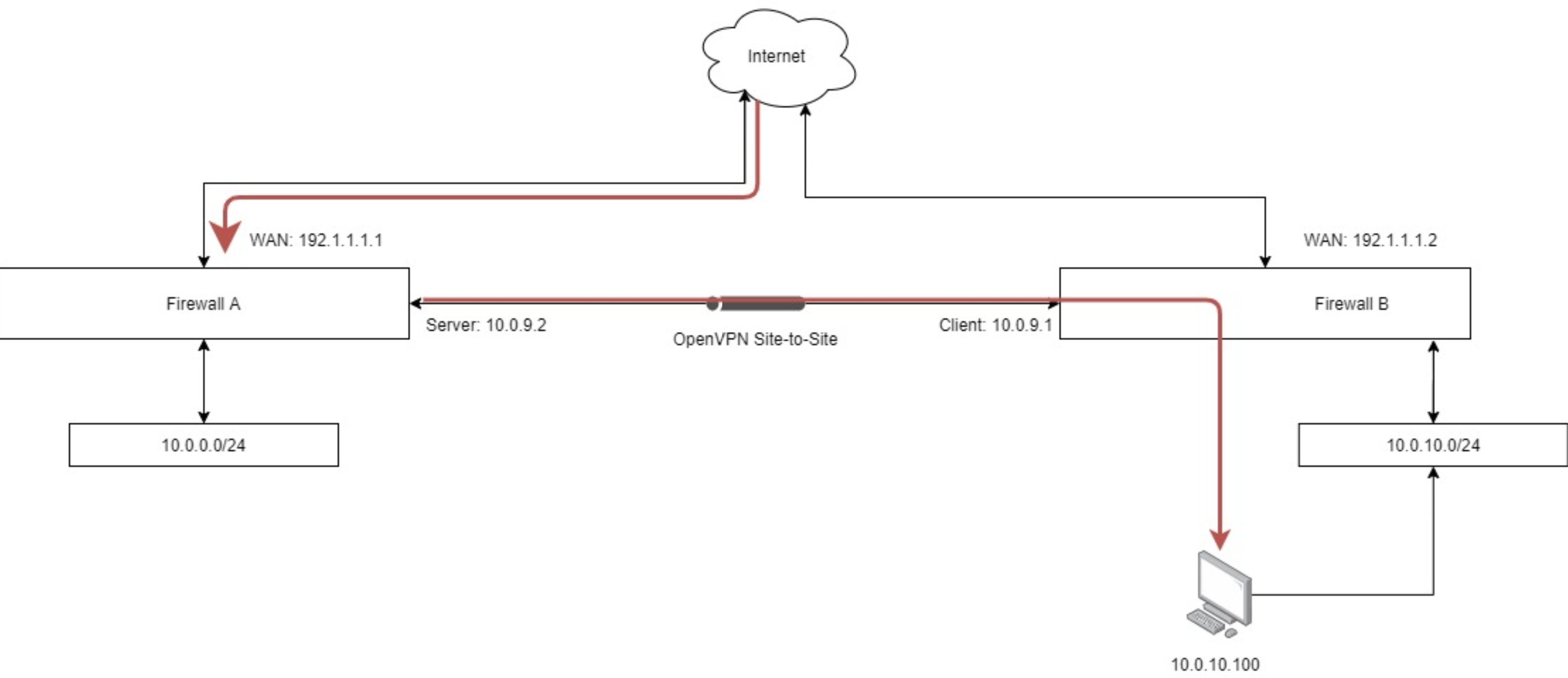
The schematic, where in red is what I am trying to achieve through a NAT rule for a certain port:
From 10.0.0.0/24 network I am able to access 10.0.10.0/24 and vice-versa without issues (including that 10.0.10.100 device and port). I am able to setup NAT rules on WAN address in Firewall A to 10.0.0.0/24 and even to other local networks there that I have not add in the schematic. In Firewall A I use Hybrid Outbound Nat mode. From
From System > Advanced, I have setup the following options:
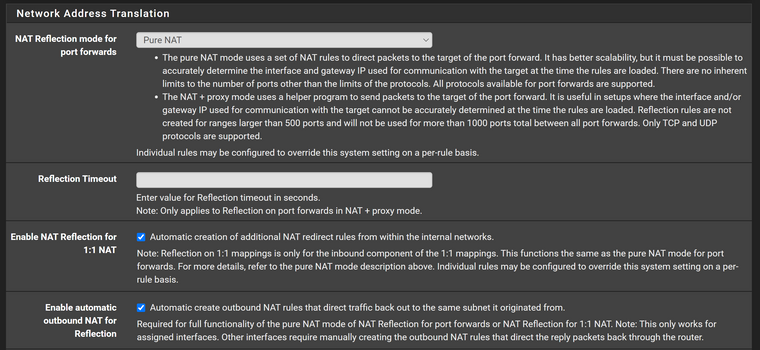
Anyone knows what is missing out of my config?
If you need more info I can provide without problem.
Thanks in advance!
-
Connections are being received in Firewall A, and seems to point to the right machine and port:
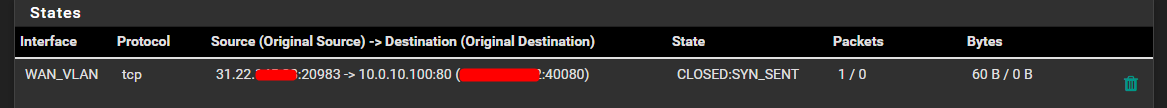
But no output for the device 31.22.x.x.
-
So, after a some CSI I notice that inbound packages where reaching the target machine, the problem was that the Firewall B didnt knew where to sent back the response, so I added a new rule in NAT Outbound for this particular device, and worked like a charm:
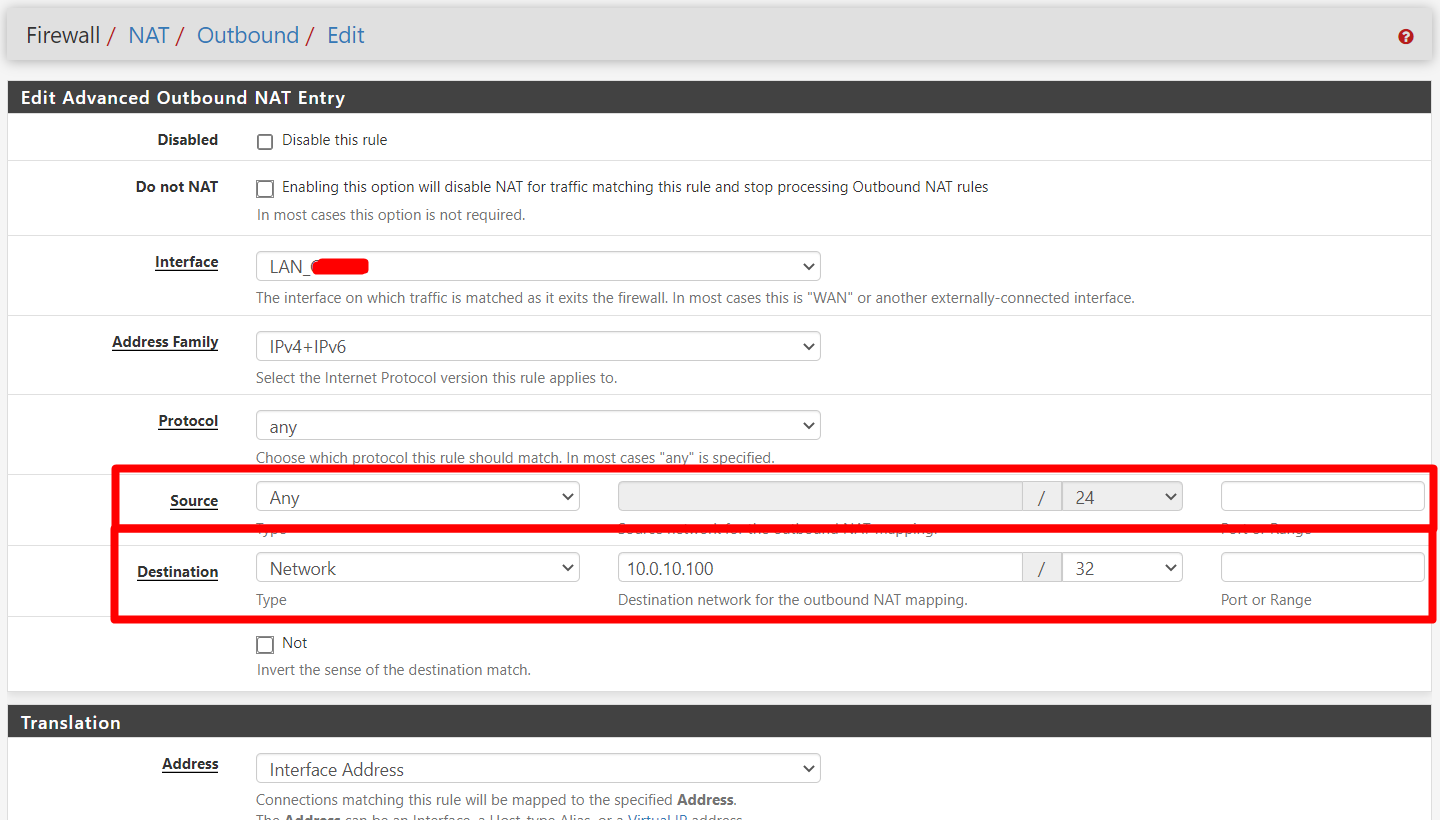
NOTE: Firewall B doesnt use Firewall A gateway, its a "hybrid" VPN.