Multi WAN Routing
-
Hello, this is my first topic/post on the Netgate forums! I made an attempt to search for my issue beforehand, but I guess I need a little advice than other posts had been given. Apologies in advance if this is a duplicate.
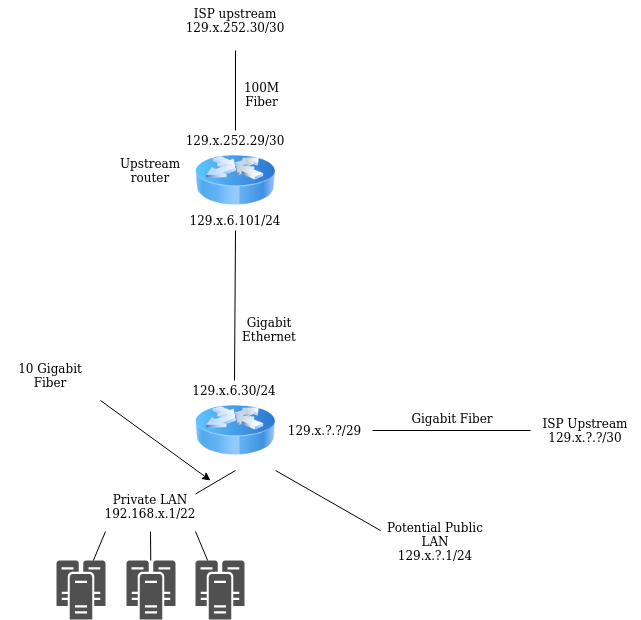
My problem is as follows: I have a physical pfSense system running 2.4.5, with a single WAN interface and a single LAN interface. The LAN is a 192.168.x.x/22 and the WAN has a single static public IP. The system is going to be given a secondary WAN provided via fiber. The new WAN subnet will be a small /29 public transit network that will give our system access to a /24 of public addresses. My issue is whether or not I can continue to run the NAT'd 192.168.x.x LAN network in addition to having a public subnet available on a separate physical LAN all on one system. I would guess this is possible, but I cannot visualize how I might set this up.
I have a fully routed pfSense box upstream (on the current WAN) from the one in question serving a /24 of public IPs provided on a public /30 transit network. However, that one doesn't have any private IP subnets configured. I recall having to disable NAT completely on that system. It works flawlessly.
What I want is a single pfSense system that is multi WAN, that handles a multi LAN containing both a private and a public subnet.
Some of the servers within the 192.168.x.x/22 will need to use the public IPs coming from the /24. I believe I might be able to accomplish this either via VIPs and a 1:1 NAT mapping. That'd be the annoying/easy way. Otherwise, it might make sense to have a VLAN going down the same cable that would be the public subnet. This is where things get a little fuzzy.
I'm not quite sure how to implement this. On the diagram below I detailed how things might look. Keep in mind, in this case the ISP is one entity, simply providing the upstream services. Any suggestions are appreciated.
-
Well, the part with 2 LANs and 2 WANs is quite easy.
- You configure the transit network interface as defined by your second ISP.
- You configure e.g. 129.x.?.1/24 as a static IP on your "Public LAN".
- You either set the NAT mode to "Manual Outbound NAT rule generation." and set all NAT rules manually, or you set it to "Hybrid Outbound NAT rule generation" and manually add a "Do not NAT" rule for the traffic between your new LAN and WAN.
- This should already create the appropriate routing table entries so that incoming traffics finds your 129.x.?.1/24. What's missing to tell the outgoing traffic which gateway to use. This can e.g. be done by specifying the gateway of the second WAN interface in the "allow to any" (or whatever firewall rule you use to allow internet access) firewall rule on your "Public LAN" interface.
Regarding the public IPs for your 192.168.x.1/22: From my perspective, the clean solution would be to give them a second network interface (e.g. using VLANs) in the "Public LAN" network. This also makes it easier to separate the administrative from the public traffic, e.g. only enable SSH on the interface in 192.168.x.0/22 network.