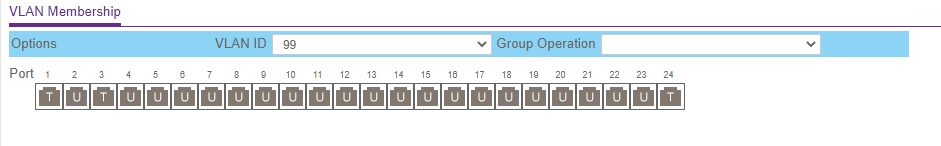
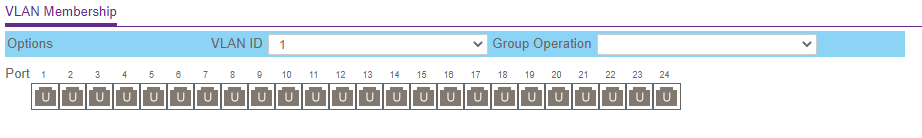
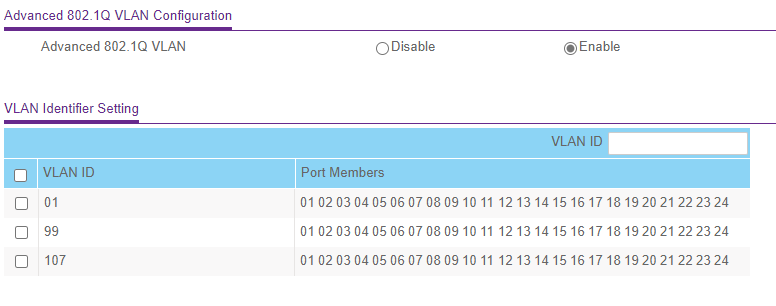
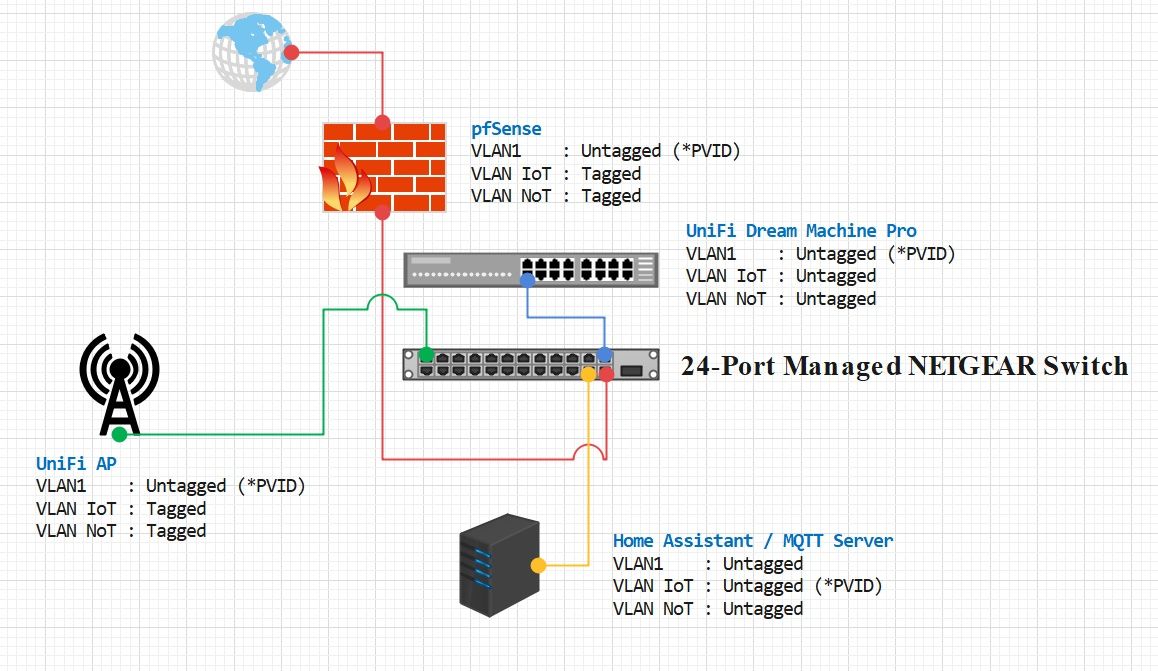
VLAN Routing with UniFi APs
-
This post is deleted! -
This post is deleted! -
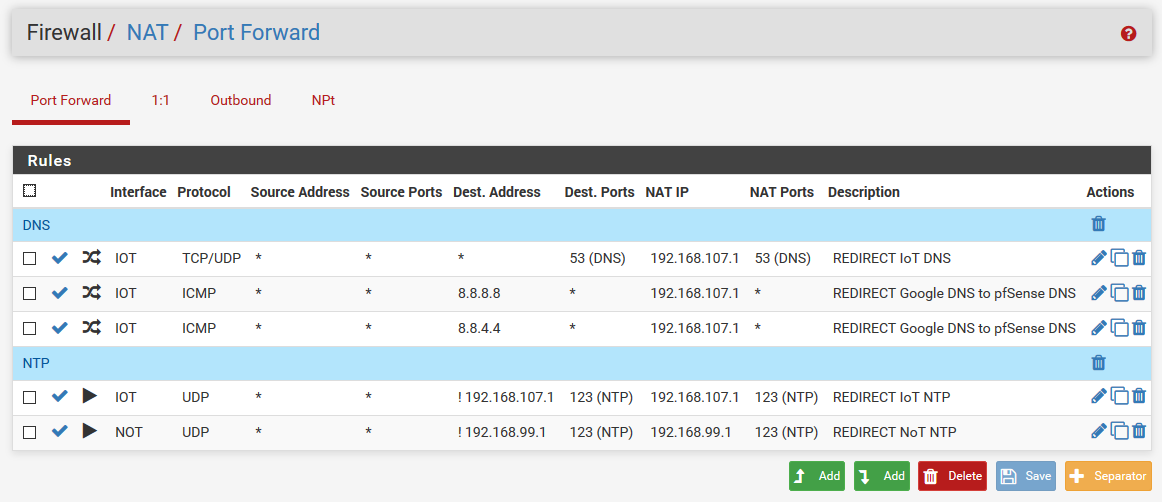
Quite often an issue with traffic to device on another vlan, is firewall on that dest device. Or that device not using pfsense as its gateway.
I would suggest you update your drawings to show your current setup - because this was clearly borked.
If would suggest you sniff on your dest vlan interface on pfsense - do you see the traffic being sent. What do you get in response? If anything?
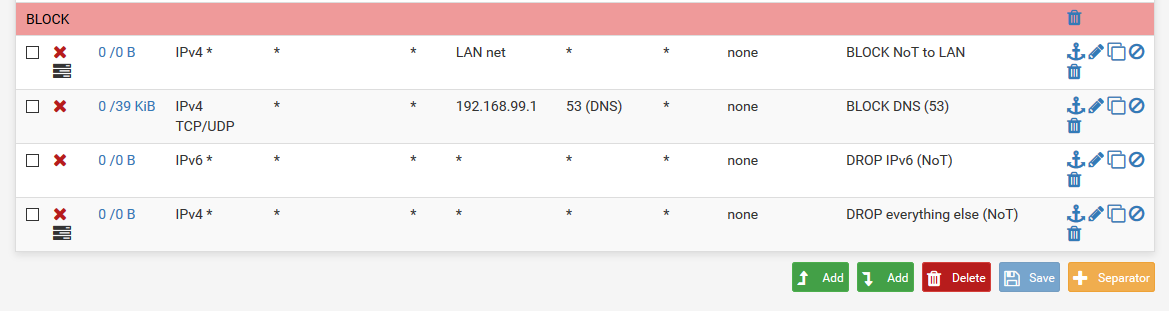
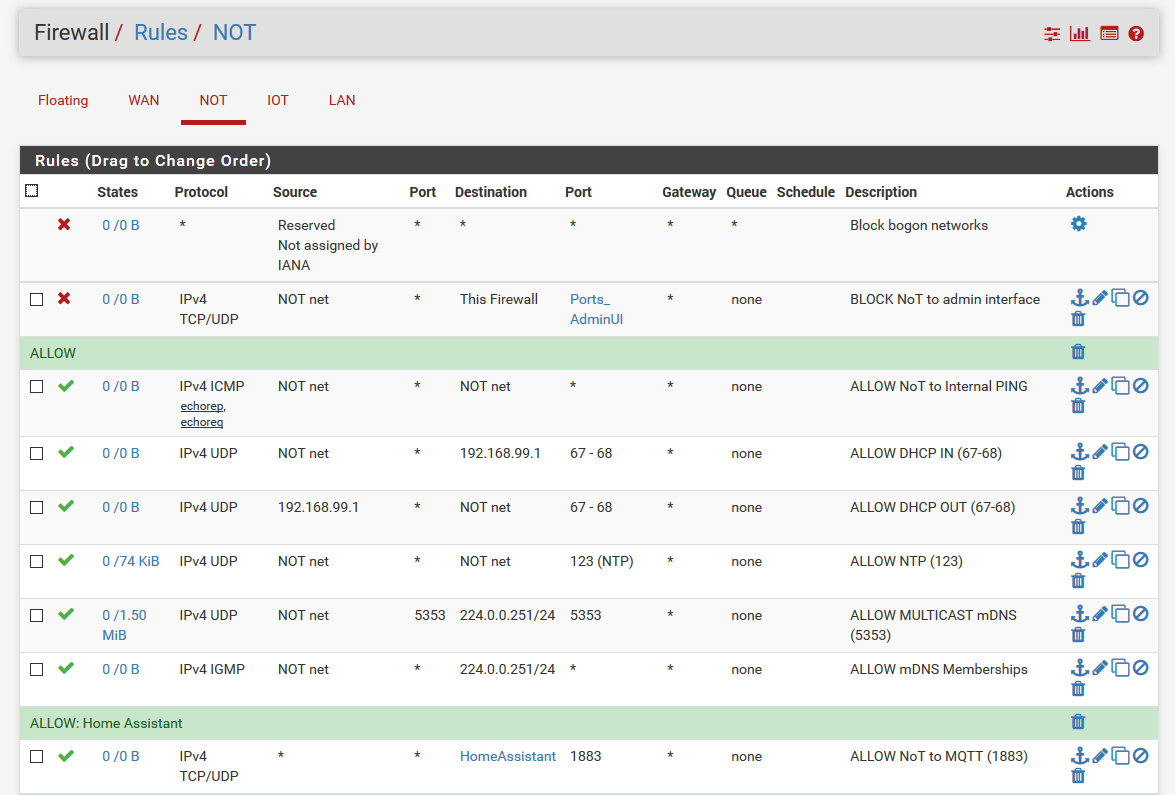
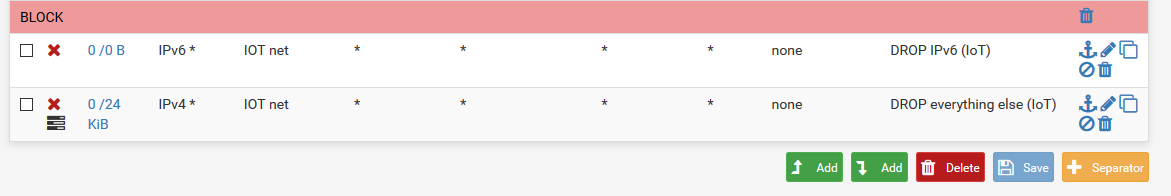
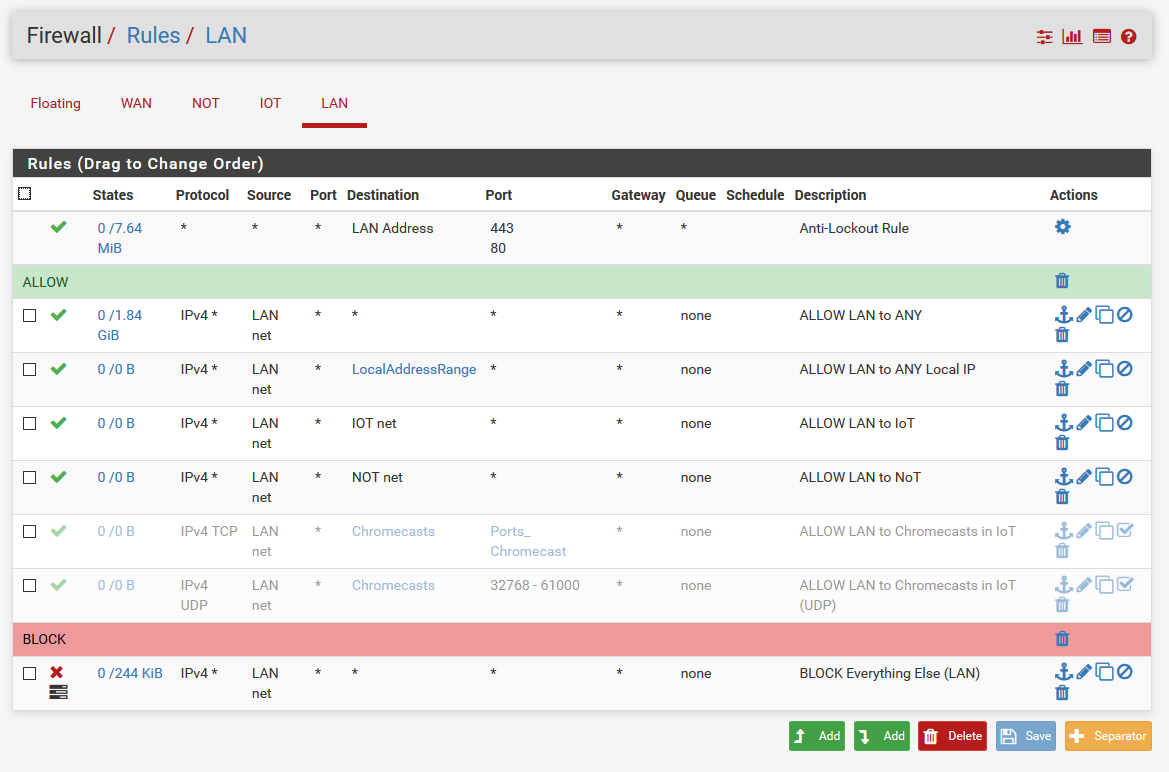
edit: Also why would you be blocking bogon on a lan side interface? How would there ever be bogon on your own network?
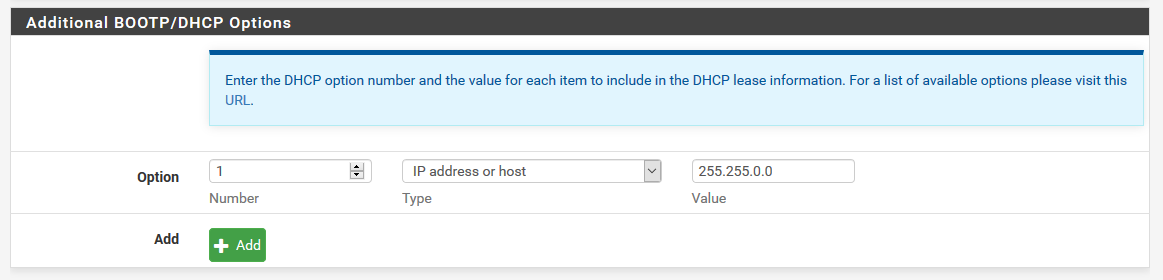
Why are you allowing dhcp? There is no need for that - pfsense auto adds rules for dhcp wheen you enable dhcp or dhcp relay on an interface.. There is no need for such rules.
-
This post is deleted! -
This post is deleted! -
@johnpoz said in VLAN Routing with UniFi APs:
Why are you allowing dhcp? There is no need for that - pfsense auto adds rules for dhcp wheen you enable dhcp or dhcp relay on an interface.. There is no need for such rules.
Hmm ... Didn't know that

I'm using Unifi AP-AC-PRO's wo. any probs.
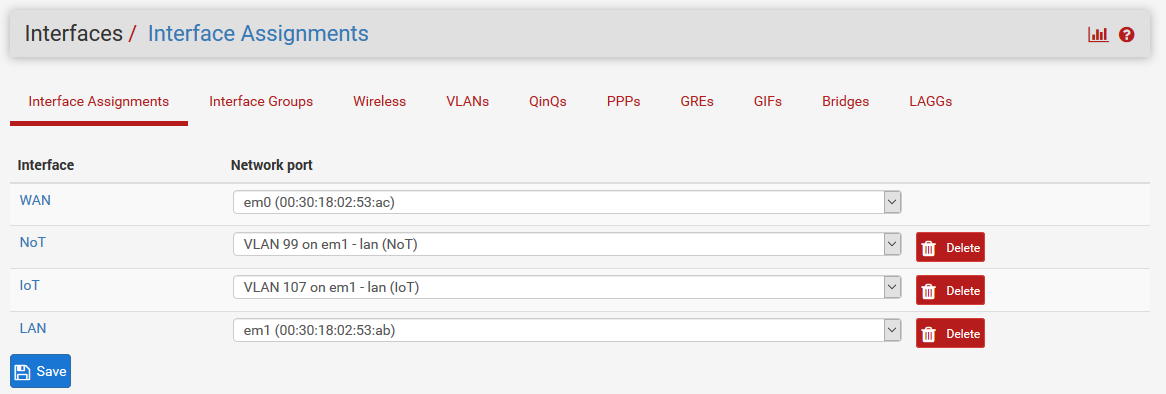
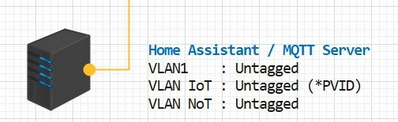
Only trick compared to "Cisco's" , is that the AP mgmt addr. must be on the Native/Untagged lan on the port the AP is connected to. Then just tag the Vlans you want for SSID's.Using UniFi controller on a VMware Deb-10 server
/Bingo
-
@bingo600 said in VLAN Routing with UniFi APs:
AP mgmt addr. must be on the Native/Untagged lan on the port the AP is connected to
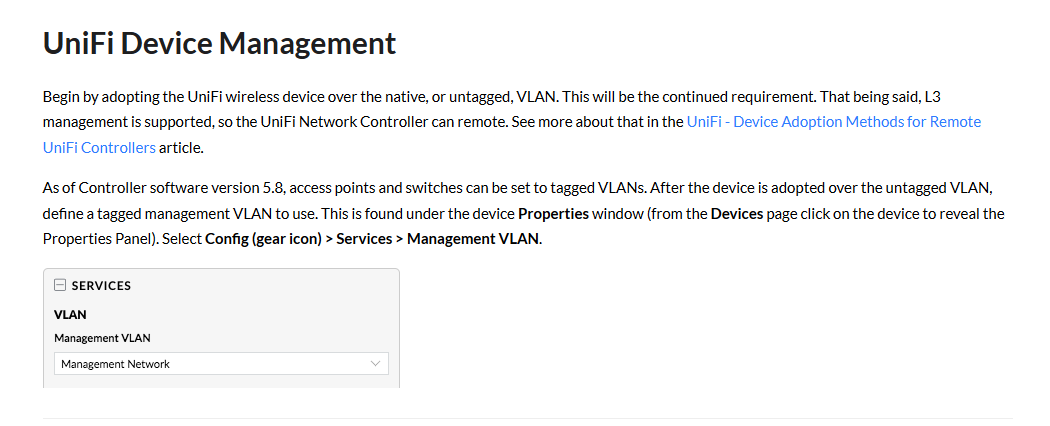
No longer true.. As of controller software 5.8
https://help.ui.com/hc/en-us/articles/360046773733-UniFi-Using-VLANs-with-UniFi-Wireless
-
@johnpoz said in VLAN Routing with UniFi APs:
@bingo600 said in VLAN Routing with UniFi APs:
AP mgmt addr. must be on the Native/Untagged lan on the port the AP is connected to
No longer true.. As of controller software 5.8
@johnpoz

Hmm ... Missed that one.
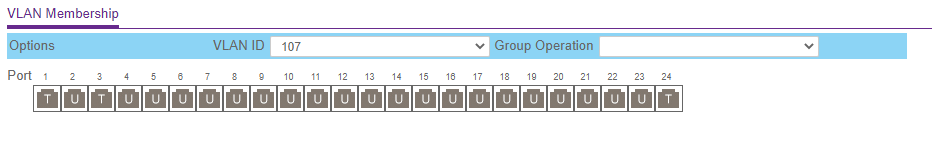
So you can adopt the AP on/via an Untagged "Whatever port that can reach the controller"
Then switch mgmt to vlan xx , and have "just tagged" vlans on the AP production port.
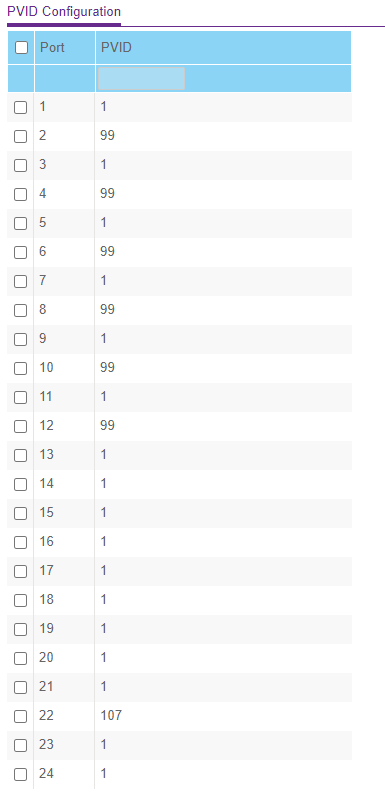
Maybe add a garbage PVID vlan on the AP Port too.Thnx
-
While I get where your coming from any untagged traffic would just go to some dummy vlan and not go anywhere.
But how would untagged traffic get on that port? But setting pvid to dummy or unused vlan on ports that only carry tagged traffic is common. But would depend on your switching os..
In cisco for example, if all you want is tagged traffic you can set the type to general and frame type to tagged only.. Any untagged traffic would just be dropped.
-
@johnpoz
I guess i always direct "Native Vlan" to something known ....
In this instance we're talking D-Link DGS-1100 & DGS-1210 , as AP switches.I do agree that it would "in normal cases" just be the AP (as it is connected to that port) , that can generate untagged frames. But in a new places i'm in an unknown environment (External partners) , and i have seen their engineers being "creative". Their CORP WiFi env. is locked heavily down (no FB etc).
And in an ARP walkthrough i have previously discovered XiaoMi MAC's on my "Lab Lans". The partner immediately took action when i informed them, that i saw what seemed to be "Private Phones" in my ENV.But it made me think ...
I'm now using MAC filtering in the AP's , even though i "hate it" , as they have to contact me to get a new/replaced device whitelisted.I'm using Win-PC's and VoiP phones w. WiFi , and the phones sets some limitations ... I switched from D-Link DGS-1100-08P to 1210-10P in order to get more reatures (.1x & Switch MAC filtering) , but not all of the phones can be configured to .1x ... So i'll have to use MAC filtering for now.
I only have the pfSense on these sites ... So if i ever want to try .1x , it would have to be FreeRad on the pfsense , and some Cert magic.
I'm just wondering if i would be killing my self in Cert mgmt if implementing that. If i do i will certainly have broken the KISS Rule
/Bingo
-
@bingo600 said in VLAN Routing with UniFi APs:
i will certainly have broken the KISS Rule
Ya kind of already did that with mac filtering ;)
While mac filtering is a method of control, which is how you seem to be using it. Mac filtering is fine as a simple method of controlling the ability of users to add different devices to the network that you do not want. For example they using phone X, and you enable mac filtering. They can not bring in phone Y without letting you know - even if they know the psk to auth to the network.
Your involvement is going to get way more problematic as users update their phones and use private macs ;)
If you really want to prevent unknown devices from connecting to your wifi.. You could only allow devices that you control on the network, with use of certs.. It is fairly complex process to export a cert from a company managed device, and try and use that cert on a non company device. If the devices are managed and locked down sufficiently..
-
Luckily i'm in a controlled environment where only PC's and Desktop Phones approved by (me) are allowed to have access via WiFi.
No phones or personal devices are allowed on that segment.
/Bingo