Ubiquiti USG-3P to PFSense
-
@macusers USG and controller need to be in the same broadcast domain (same "switch", same VLAN, same IPv4 subnet, eg 192.168.1.2 for USG and 192.168.1.200 for the controller) in order to adopt devices. I am not trying to nag you, but this in particular is a UI community issue...
-
@macusers I edited the posts because I forgot the CPE modem...

-
You can adopt devices between different subnets but you need to use a different method. Like at the CLI of the switch/ap etc.
-
@nightlyshark said in Ubiquiti USG-3P to PFSense:
@macusers USG and controller need to be in the same broadcast domain (same "switch", same VLAN, same IPv4 subnet, eg 192.168.1.2 for USG and 192.168.1.200 for the controller) in order to adopt devices. I am not trying to nag you, but this in particular is a UI community issue...
I'm not sure about if it's the special case for USG only but that's not true for Unifi switchs or APs. My controller is always on a seperate network and 12 other devices are happily adopted. As long long the device in question can ping the controller IP, it can be adopted. I think my issue is: USG doesn't know how to get to the 10.0.20.1/28 subnet from it's 192.168.10.1 address.
-
Hmm, the routing table implies it does.
Can it not ping to it?
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
You can adopt devices between different subnets but you need to use a different method. Like at the CLI of the switch/ap etc.
yeah, I tried from the CLI, but main issue is USG cannot reach to controller to send the adoption request - that was my 2nd issue in my original post. form
CKtoUSGping is fine but not the other way around. -
Then check the firewall rules on the pfSense WAN
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
Then check the firewall rules on the pfSense WAN
I have this rule on WAN interface:
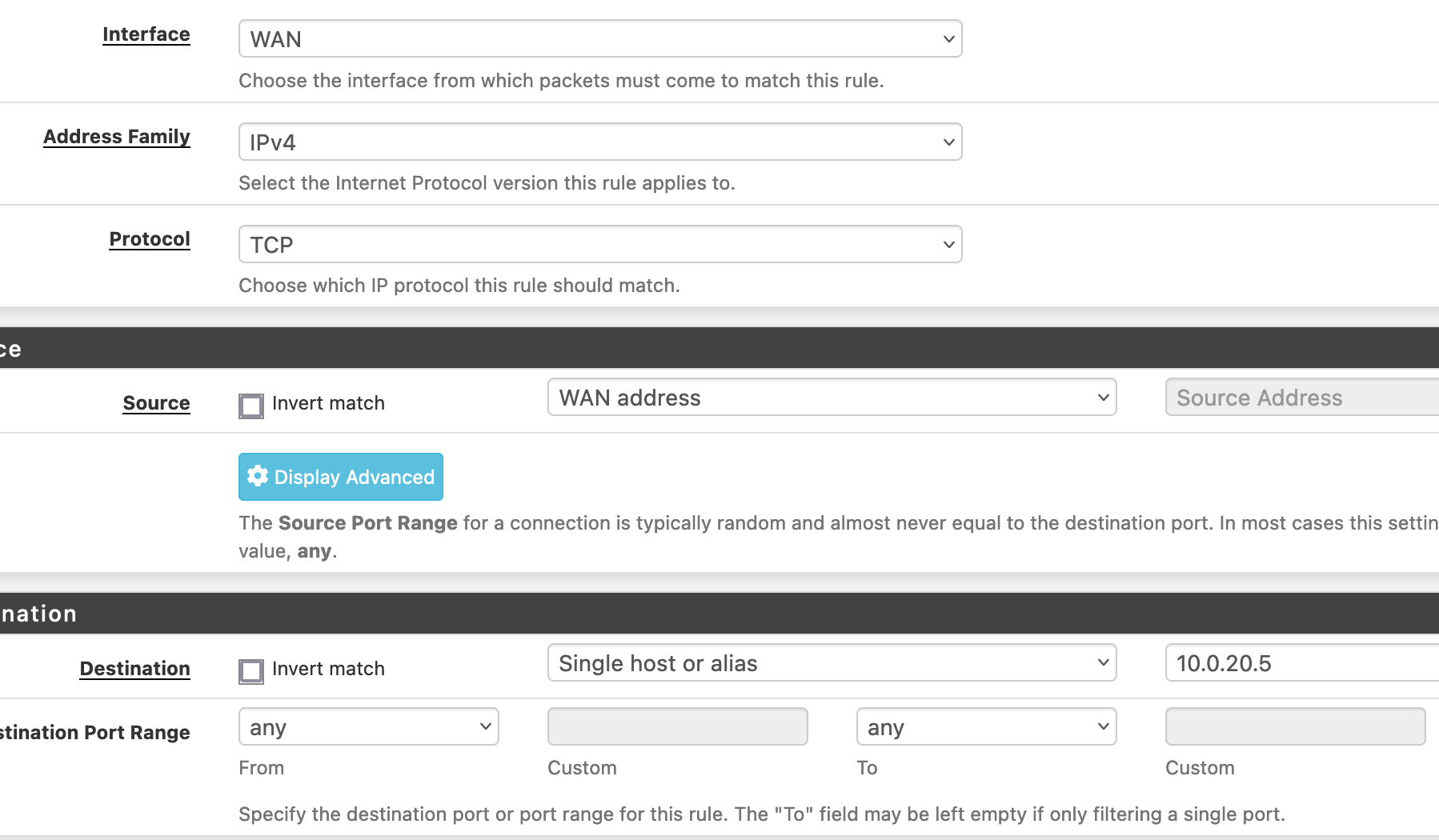
Source is wrong?
-
Should be 'WAN net'. That will include the USG's interfacein the WAN subnet.
And you might want to allow icmp also if you're testing with ping.
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
And you might want to allow icmp also if you're testing with ping.
yeeppp!!!!
that was the issue - it needed ICMP enabled. the moment I did that I could adopt the USG in the controller.Now, to fix the first issue - in coming VPN connection
-
@stephenw10, any idea what's might be the issue with VPN connection - double natting? Or need to setup some sort of port forwarding on USG?
-S
-
What sort of VPN is it? How are you testing?
If it's incoming to pfSense then you will need to port forward that traffic in the USG.
-
@stephenw10
it's OpenVPN. port forward teh traffic to VPN subnet or pfSense WAN IP?
Normally I connect though mobile phone (to get out of home network) and VPN back to see if it's connecting. -
Forward the encrypted OpenVPN traffic to the pfSense WAN in the USG. So by default that would be UDP port 1194 but it could be whatever you configured it as.
Steve
-
VPN worked

-
@stephenw10
Is it possible setup a static route (from WAN to LAN) on and disable NAT'ing on USG? IS it better? Or will it even work?-S
-
You must have NAT somewhere between your public IP and the private internal subnets in order for clients to be able to connect out and replies to know where to come back to.
By default both the USG and pfSense will apply outbound NAT only one of them needs to. The USG needs to do it in your setup because it has the public IP to NAT to.
You can disable outbound NAT on the USG as long as it has static routes to the subnets behind pfSense.
Steve
-
@stephenw10 said in Ubiquiti USG-3P to PFSense:
You must have NAT somewhere between your public IP and the private internal subnets in order for clients to be able to connect out and replies to know where to come back to.
yeah, of course!!
I meant to ask: is it better to do the natting on pfSense and disable on USG or otherway round. As thenattingis enabled on USG, is it safe to completely disable on pfSense? do I need to anything else as well, if NAT is disabled on pfSense?-S
-
You have to have NAT enabled on the USG because it has the public IP.
You can disable NAT on pfSense as long as the USG has static routes to the subnets behind pfSense and is setup to NAT those.
-
@macusers For most small scale (under 20 users) intents and purposes, you actually don't need both devices, they complicate setup, add latencies and cause headaches. PfSense can do everything USG does, a lot faster (depending on the hardware) and a lot more reliably.
But, all that is always, just my opinion.