Unable to configure LDAPS to Samba Active Directory
-
Hi.
I've been trying for hours to configure an external LDAPs server for auth but I cannot make it work.Background: I've upgraded my Windows domain infrastructure to a more recent Samba version (4.11), which now requires secure LDAP connections. In Zimbra I was able to configure AD auth by importing the LDAP SSL certificate.
In pfSense Authentication Servers configuration I see hints suggesting that the server Hostname must match the CN of the destination computer, and down below the Peer Certification Authority must match the one of the server cert.
So I imported in pfSense the Samba AD CA and selected it in the auth server config. As connection hostname I selected dc1.domain.lan and made sure pfSense can reach this hostname (checked with ping and dns lookup).
Unfortunately after this setup the external auth still doesn't work. I haven't found how to debug this, the logs just says
/diag_authentication.php: ERROR! Could not bind to LDAP server AD. Please check the bind credentials.But credentials are correct.
Any hint on the config or on how to debug?
Thanks.
P.S. as a workaround I've set the param below in smb.conf, so I'm able to bind without SSL or TLS.
ldap server require strong auth = no -
Does the hostname match the CN or SAN of the server cert?
Was the server cert issued by that CA?
What do the server logs show?
Can we see a (redacted) screenshot?
Steve
-
Does the hostname match the CN or SAN of the server cert?
Yes, I decoded the cert and used the same hostname, including case (
DC1.whatever.lan)Was the server cert issued by that CA?
Checked as well
What do the server logs show?
Nothing special, I see no connection from the pfSense IP.
Can we see a (redacted) screenshot?
This is the imported CA cert in pfSense
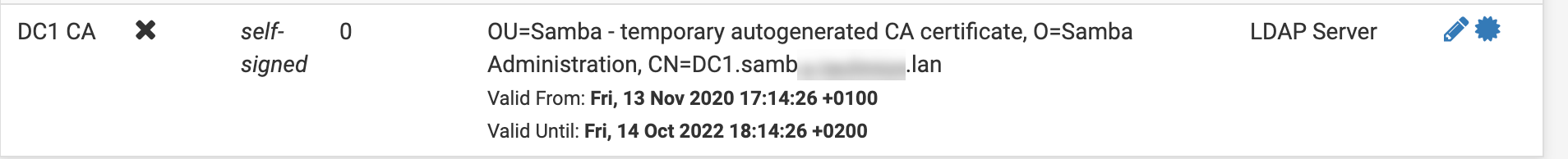
This is the Auth Server config
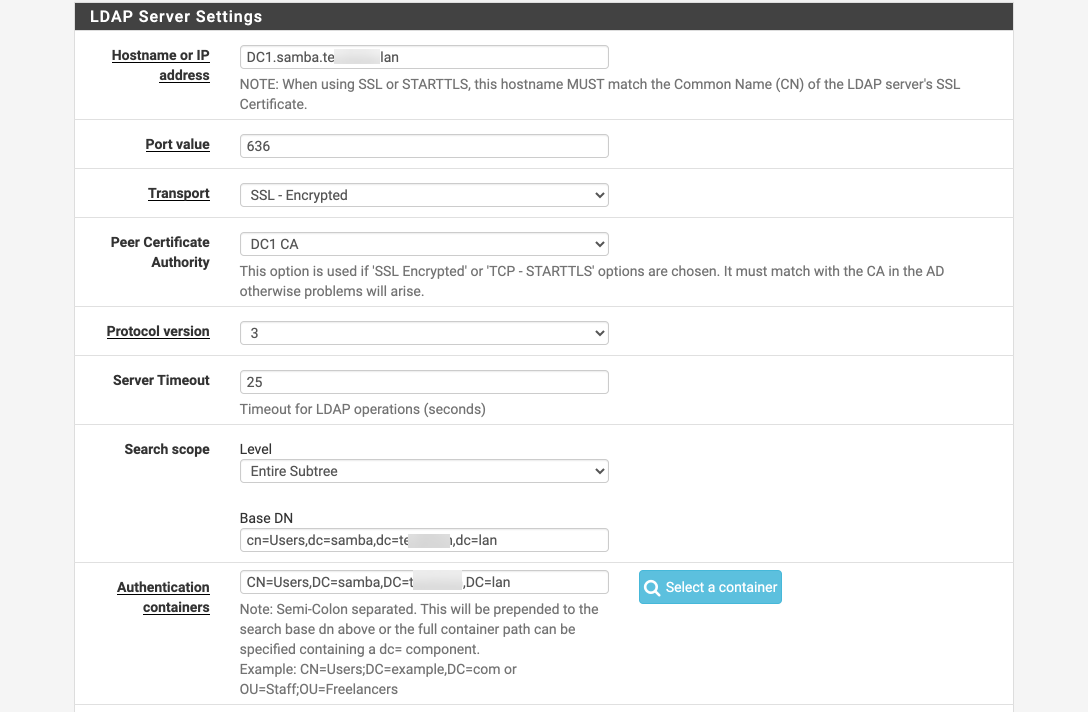
Cert:
# echo -n | openssl s_client -connect dc1.samba.xxx.lan:636 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' | openssl x509 -in - -noo ut -text [...] Certificate: Data: Version: 3 (0x2) Serial Number: -491737505 (-0x1d4f51a1) Signature Algorithm: sha256WithRSAEncryption Issuer: O = Samba Administration, OU = Samba - temporary autogenerated CA certificate, CN = DC1.samba.xxx.lan Validity Not Before: Nov 13 16:14:26 2020 GMT Not After : Oct 14 16:14:26 2022 GMT Subject: O = Samba Administration, OU = Samba - temporary autogenerated HOST certificate, CN = DC1.samba.xxx.lan Subject Public Key Info: Public Key Algorithm: rsaEncryption -
Can pfSense resolve that hostname?
Do you see states opened to the server on port 636 with two way traffic?
Steve
-
@stephenw10 said in Unable to configure LDAPS to Samba Active Directory:
Can pfSense resolve that hostname?
I checked with DNS Resolver and Ping, they can both reach
Do you see states opened to the server on port 636 with two way traffic?
I just tried with tcpdump, I see connections coming from pfSense to the DC1 host and replies going back.
How can I debug the auth on the pfSense side?
thanks
-
Go through what's shown here: https://docs.netgate.com/pfsense/en/latest/troubleshooting/authentication.html
But beyond that the server should log why it's rejecting it. pfSense can probably only see that it has been rejected. For security reasons the server should not tell a failed client why it's failed.
Steve
-
@maxxer Check previous discussion about similar issue and how to troubleshoot here: https://forum.netgate.com/topic/145578/ldaps-ad-bind