Port Forward in LAN / access from another LAN
-
Hello everyone,
Target & Issue.
..........................
Accessing FTP Server on DMZ LAN 18 from App server on another LAN 8. with these settings below, while clients coming from different public IP's can. Diagram below.Status
Pure NAT enabled and NAT Reflection. Added WAN ip to FTP_Allow Alias for port 21. Also tried to add allow rule alone without success. Any comments or suggestions appreciated for this.
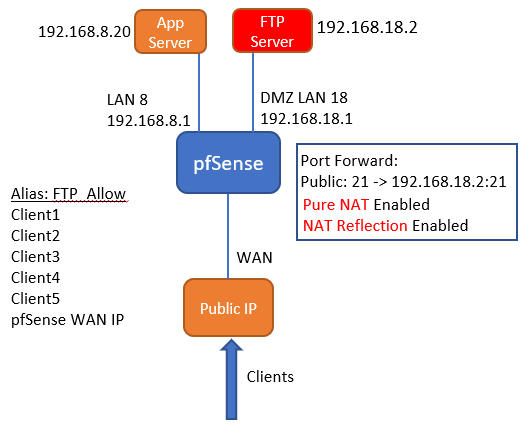
-
@bambos said in Port Forward in LAN / access from another LAN:
Added WAN ip to FTP_Allow Alias for port 21.
Why WAN IP? The source IP is the App servers.
-
Yeah the wan IP doesn't belong at all.
Why would your app server not just hit the 192.168.18.2 directly or via a fqdn that points to 192.168.18.2 host override if your wanting to use some public fqdn. Why would you want to bounce it of your nat reflection.. All that is going to do is slow down the connection.
-
@viragomann when app server doing FTP connection to publicIP:21, doesn't this makes NAT translation going out to the internet ?
So i thought going to internet and coming from internet, the IP is the public IP of WAN. At least when the clients FTP stor files, i see their public IP. -
@bambos said in Port Forward in LAN / access from another LAN:
when app server doing FTP connection to publicIP:21, doesn't this makes NAT translation going out to the internet ?
No, nothing reaches the WAN interface indeed.
NAT reflection virtually reproduces the NAT rule you've added to WAN to the other interfaces. So it behaves as if you have the same NAT rule on LAN as well.
So if you add firewall rule for that you need to allow the App server to access the FTP. -
@viragomann ok Sir, now i got it (i think)
all my configuration is having the exposed FTP network isolated because of the unsecured port 21 operation their. I guess that's why App server cannot go to FTP Lan, same goes for FTP Lan.So should i add a rule on the FTP Lan to allow source the app server ?
Also add a rule on LAN 8 to allow destination to FTP Lan ?how this seem to you ? or maybe you suggest something else?
-
@bambos
For allowing the app server to access the FTP you only need a rule on LAN 8 for source 192.168.8.20 and destination 192.168.18.2. -
@bambos said in Port Forward in LAN / access from another LAN:
So should i add a rule on the FTP Lan to allow source the app server ?
Also add a rule on LAN 8 to allow destination to FTP Lan ?Depends, what you going to do active or passive? Which depends if the server makes the data connection or the client makes the data connection.
-
@johnpoz i use 21+passive ports, i have notice more performance and faster transfers on the small files (much faster actually). i have those ports on alias. As Viragomann stated, i think i will go with the inside routing way.
-
Well in passive the client makes connection to the server. So you would not need any rules on the interface server is on to allow the creation of the data port.
As to faster speed be it active or passive.. That make no difference. Its just who opens the connection.
Normally no firewall rules are needed on the client side for passive, since quite often the client side outbound rule is any, that is default of pfsense. If you are limiting the destination ports device can create outbound. Then yes you would need a rule on the clients interface to allow whatever ports your server is going to offer up for the passive data connection.