Cannot reach DMZ servers via external addresses
-
I have NAT port forwards set up for mail, web, etc. It looks like things are mostly working when I send/check mail from outside. But bringing up a website from the DMZ gets me "Potential DNS Rebind attack detected, see http://en.wikipedia.org/wiki/DNS_rebinding
Try accessing the router by IP address instead of by hostname.". I'm not trying to access the router.If I use the external IP address instead of the hostname, I wind up at the pfSense login screen. Not what I expected. I am sure I have something simple wrong here. Hints?
--Richard
-
@rlmalisz said in Cannot reach DMZ servers via external addresses:
If I use the external IP address instead of the hostname, I wind up at the pfSense login screen
Show us (image) a NAT rule that handles port TCP 25,110,143,465,587,993,995 (all the email related ports).
And also an image of the rules that handles port TCP 80 and port TCP 443.The first 7 'mail' rules have exactly the same structure as the last 2. Only the port number changes.
-
@gertjan said in Cannot reach DMZ servers via external addresses:
@rlmalisz said in Cannot reach DMZ servers via external addresses:
If I use the external IP address instead of the hostname, I wind up at the pfSense login screen
Show us (image) a NAT rule that handles port TCP 25,110,143,465,587,993,995 (all the email related ports).
And also an image of the rules that handles port TCP 80 and port TCP 443.The first 7 'mail' rules have exactly the same structure as the last 2. Only the port number changes.
Going for simple here: one of the internal servers that exhibits the problem only does IMAP and IMAPS. Snagged these as exported PDFs, as there was no way to get the entire rule pages on one screen on the laptop, hence the horizontal lines through parts of the images:
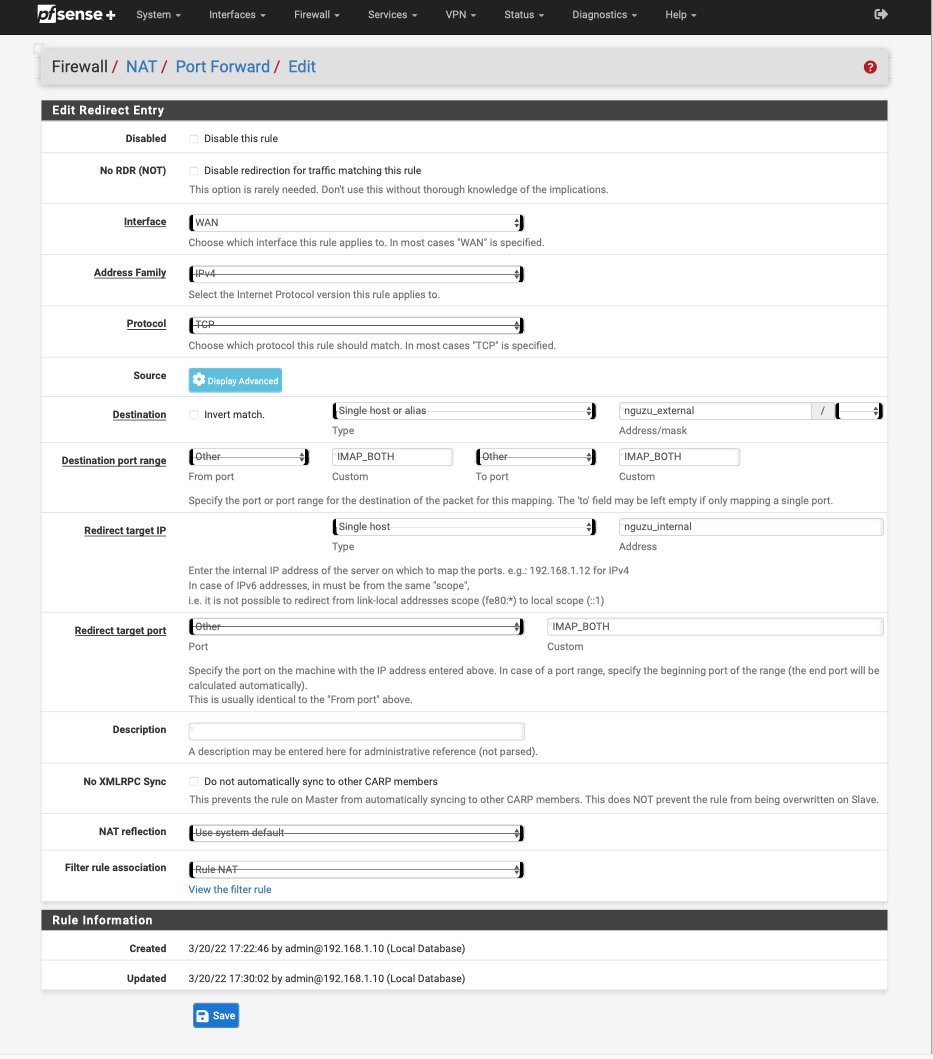
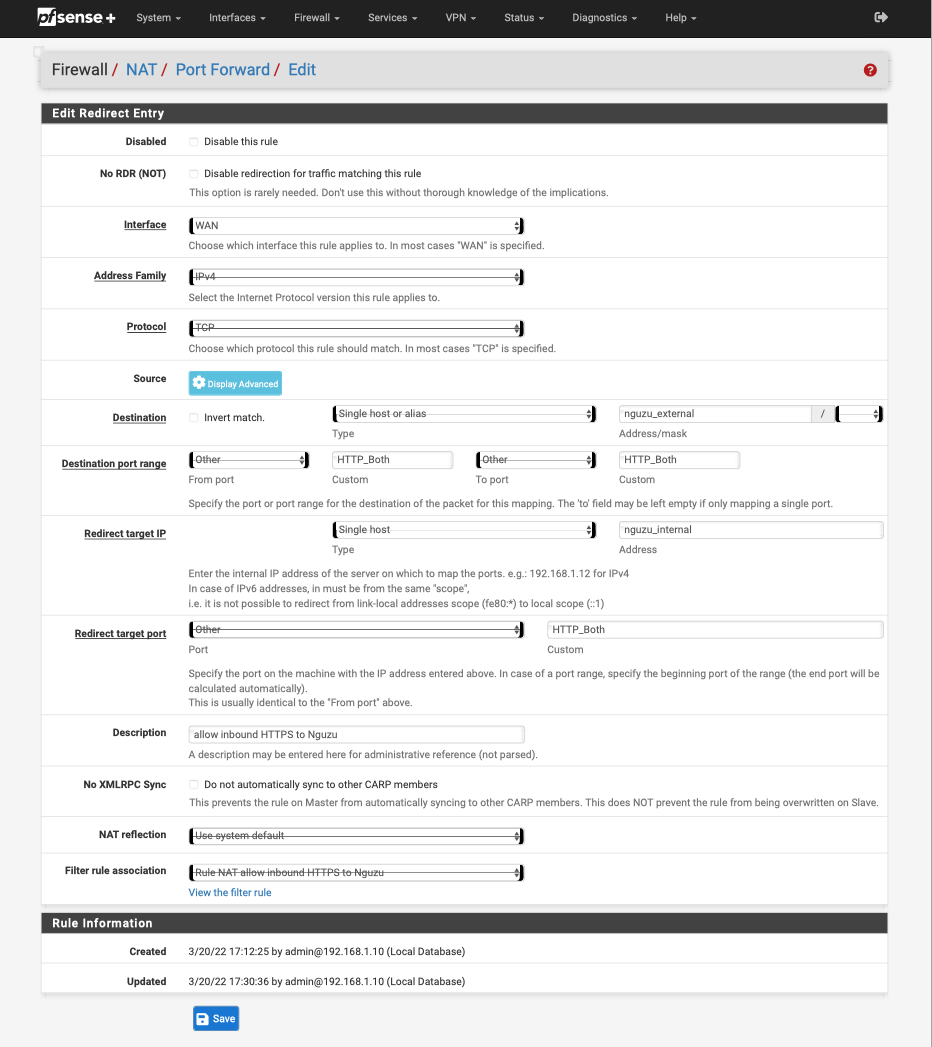
-
The alias HTTP_both does contain port 443 and 80 ?
Both NAT rules look identical, and wrong.
This :
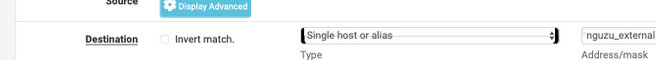
should be :
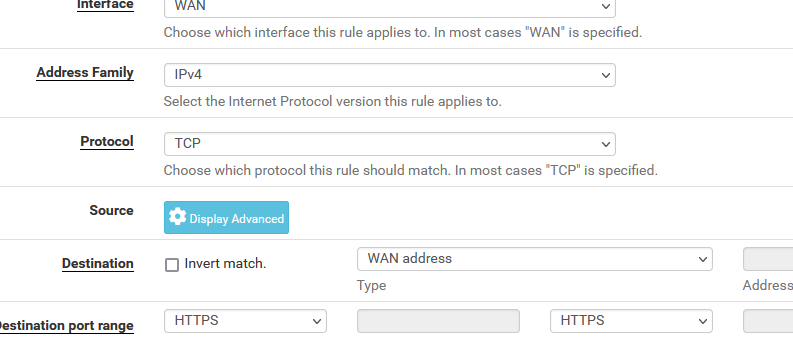
( my example just NATs port 443, as port 80 is pretty dead these days. )
The 'destination' is "WAN address" which will include your WAN IP address. That where your traffic coming from the Internet winds up.
The the NAT rule will translate traffic from that IP and correct port to an internal LAN IP, and port.The "destination" can't be a host like "nguzu_extrenal" as this is probably some RFC1918 IP == non routable over the Internet.
edit :
See also the documentation Port Forward Settings and see what they tell us about destination.
-
@gertjan "nguzu_external" is an alias for a WAN address. I set up a virtual IP for that address, and use a descriptive alias for it to help me keep things straight. As I said in my original question, external traffic to the servers from WAN works fine. It's the internal clients attempting to access those servers that is busted. Since we serve our own email, this is problematic.
So this looks like I can fix this via setting NAT reflection to something other than whatever the pfSense default is. Will look into that. Thanks for your input.
--Richard
-
@rlmalisz said in Cannot reach DMZ servers via external addresses:
setting NAT reflection
There is another solution, no reflection needed.
Use a "host override".On the outside, the Internet, mail.yourserver.tld point to your (a) WAN address.
On the inside, a "host override" like a.spanou@add-assoc = IP address makes all your internal mail clients happy.