DNS Resolver Over IPSec Connection
-
Original Post, for reference:
https://forum.netgate.com/topic/176292/ios-ipsec-connection-error
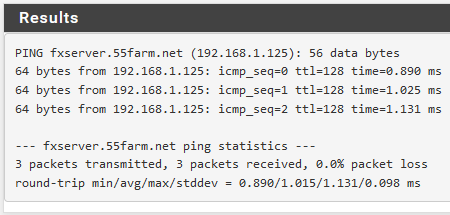
I seem to be having an issue getting any clients connected via IPSec to use the pfsense device to resolve host names defined in the DNS Resolver - Host Overrides list. For reference, the device itself is able to resolve all entries via the ping test without a problem. I've attached screenshots of my config for reference here too.
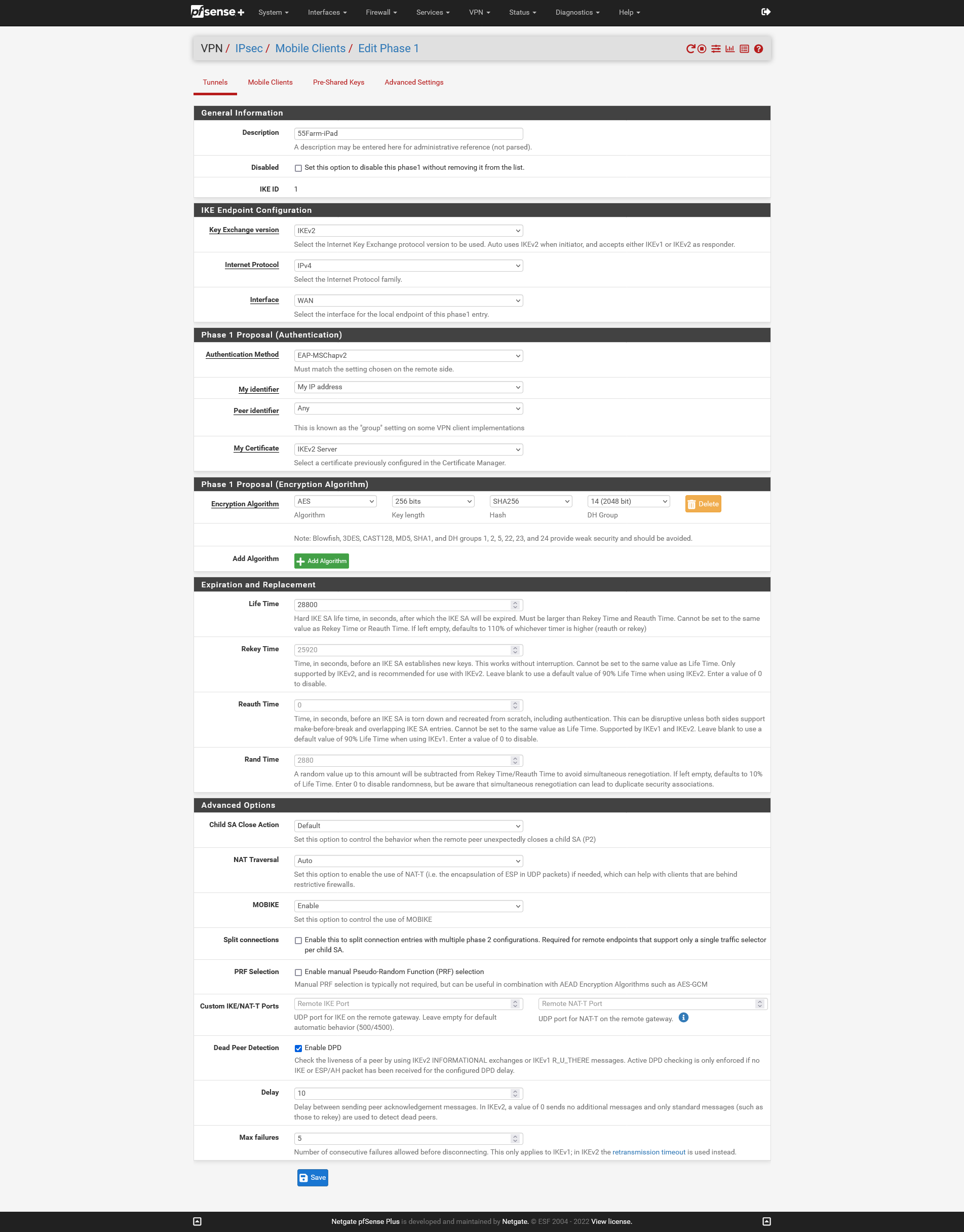
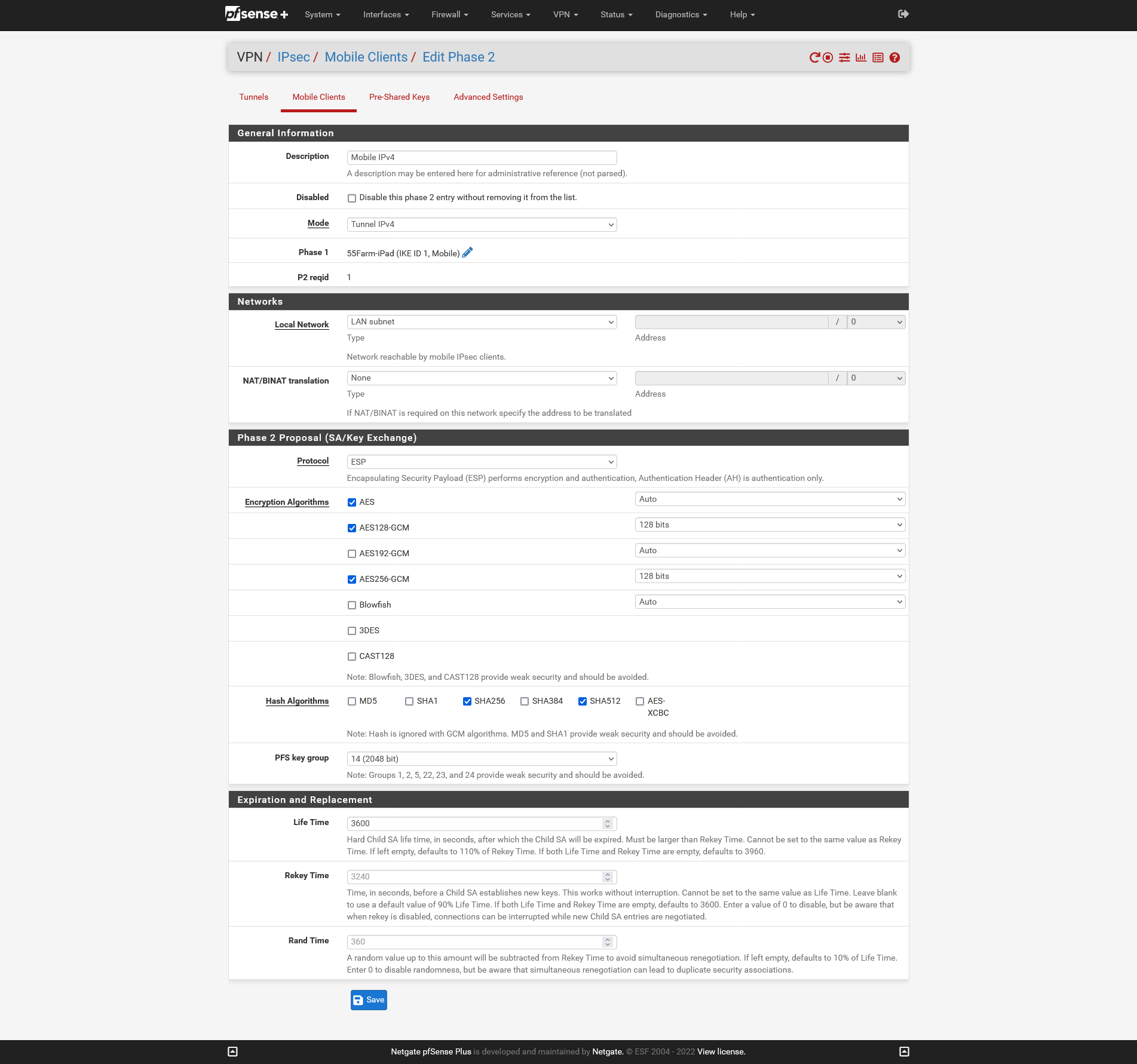
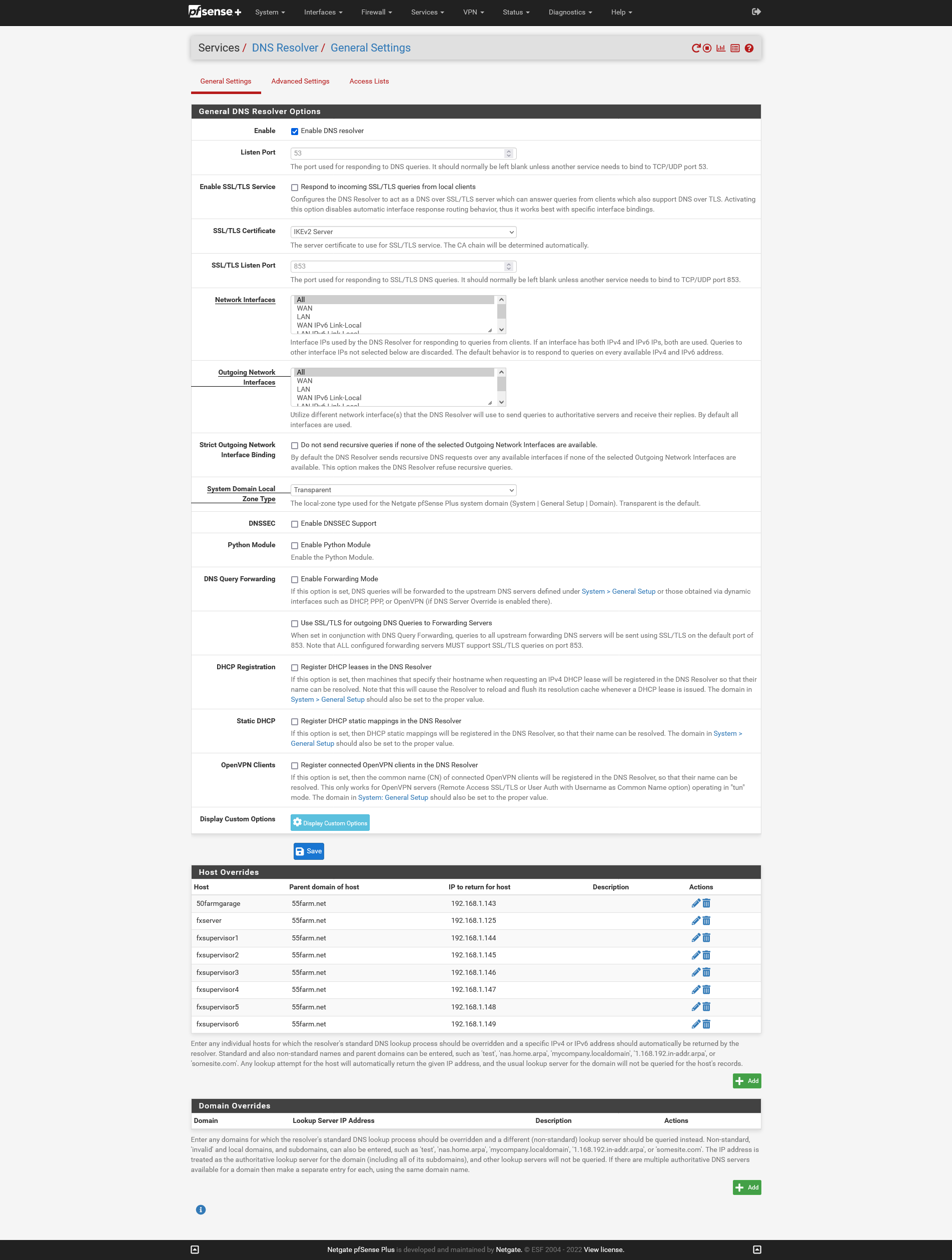
In the previous thread someone had mentioned that I'm only giving the VPN clients access to the LAN, but the pfsense is on the same subnet as the devices I'm trying to connect to. I have no problem connecting to the devices on the subnet via ip address.
Thanks!
-
@rchiocchio Check the if the ACL in DNS resolver is allowing it.
You need to add the remote network there.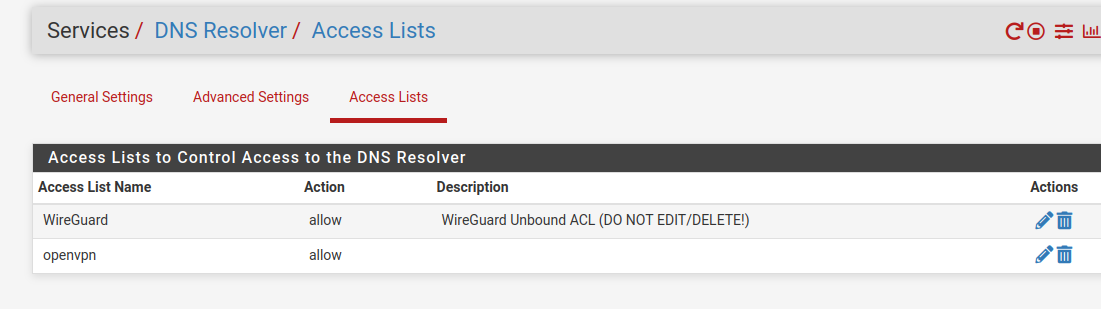
-
@mcury thanks, figured there was one other thing... first time using a pfsense firewall for me.
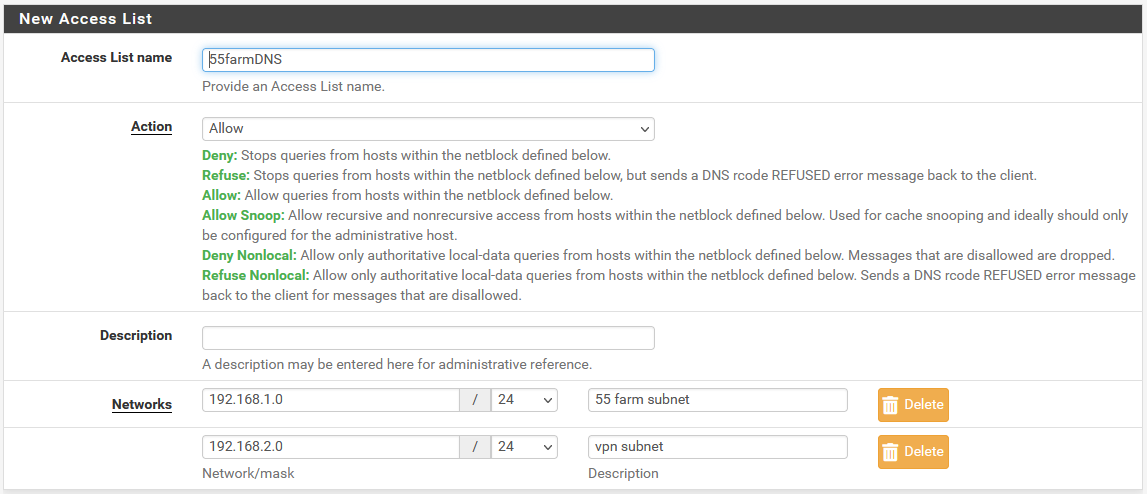
went ahead and added it like this, .1 is the local subnet and .2 is the vpn subnet. Let me restart the dns resolver and see how it goes. Is there anything else I might be missing in here?
-
@rchiocchio said in DNS Resolver Over IPSec Connection:
went ahead and added it like this, .1 is the local subnet and .2 is the vpn subnet. Let me restart the dns resolver and see how it goes.
You usually don't need to add the local subnets there.
This is only required when the subnet is not directly connected to pfsense, behind another router connected to pfsense, or a remote network that is going to use unbound.Is there anything else I might be missing in here?
Make sure that you are forwarding the traffic to the DNS resolver to an interface that is listening on port 53 TCP/UDP, and also that this traffic is allowed to go through the tunnel (phase 2), and firewall rules.
-
@mcury said in DNS Resolver Over IPSec Connection:
Make sure that you are forwarding the traffic to the DNS resolver to an interface that is listening on port 53 TCP/UDP, and also that this traffic is allowed to go through the tunnel (phase 2), and firewall rules.
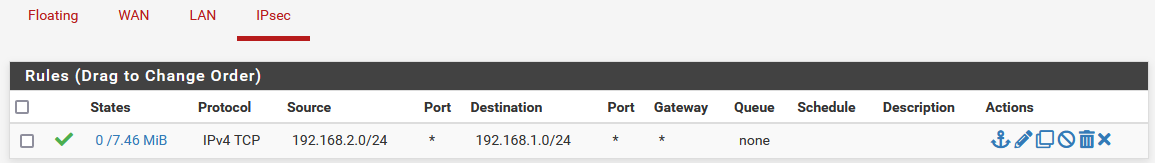
Looks like the forward & rules were already set up by default?
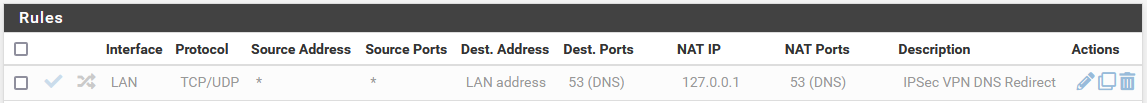
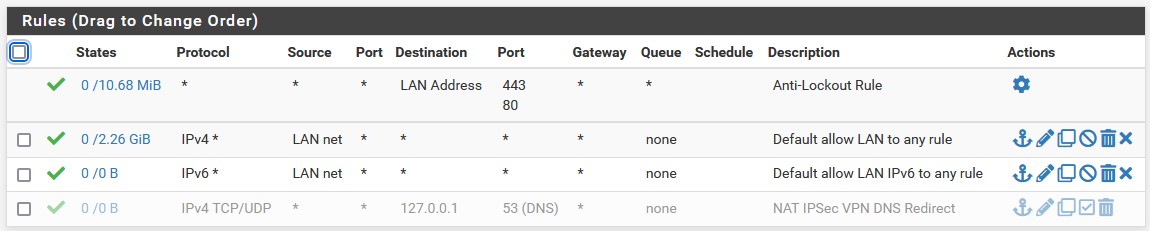
and this rule should allow all traffic...
-
@rchiocchio Keep that NAT disabled, you don't need that.
You are allowing only TCP traffic, DNS most of the times uses UDP, try to change that rule from the IPsec tab to TCP/UDP and test again.