pfBlocker with GEO IP not block IPSEC
-
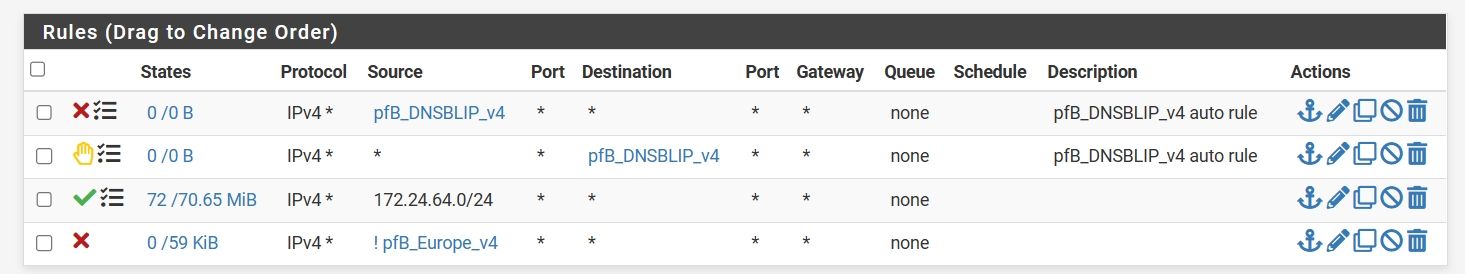
I have configured firewall with GEO block for IPSEC.
After all, in the IPSEC logs I see attempts to connect to addresses outside of geolocation, e.g.:Jan 4 07:18:18 charon 98918 03[NET] received unsupported IKE version 6.15 from 45.33.46.249, sending INVALID_MAJOR_VERSION
Geolocation works properly, because I do not see blocked addresses on the list. The VPN alias ports are 500 and 4500. Where do these entries come from? Shouldn't the firewall cut them out?
-
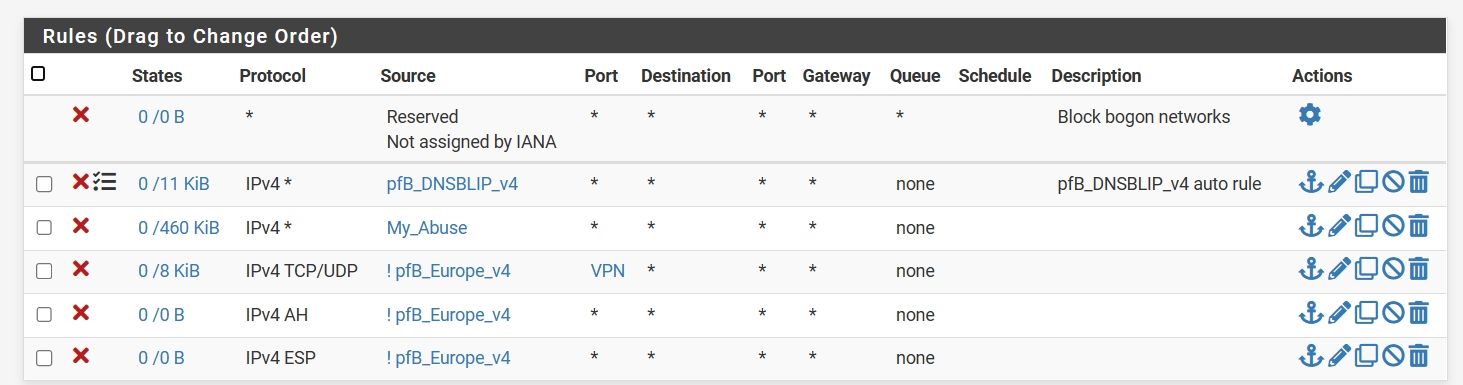
@piter-0 That depends on you having disabled the “built-in” rules that allows VPN Server access.
By default pfSense has built-in rules to allow access to UDP 500, 4500 and ESP - these rules have a higher ppreference than user created rules.
So if you want to GEO block access to your VPN service, you need to disable the built-in rules, and then create som “allow VPN rules” after your block rules.You can disable the built-in rules in SYSTEM->ADVANCED->FIREWALL&NAT
-
@keyser Thanks, sounds reasonable. I'll test it when I have time :)
-
@keyser Works fine, thx :)