Help on rules
-
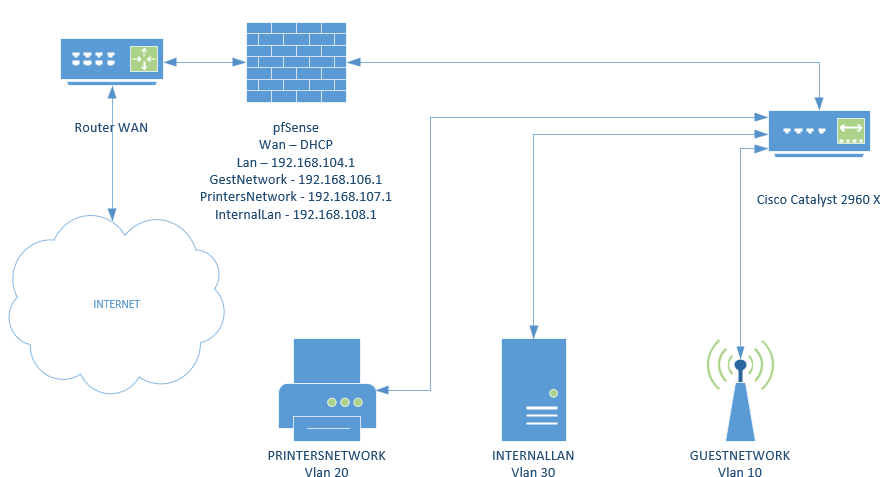
I'm a newbie to networking. How can I make my cisco switch listen to my vlan's?
How do I assign a Cisco port to Vlan'sAny help will be welcome
A -
@afcarvalho well the port connected to your pfsense interface would be what cisco calls a trunk. The vlans would be tagged on this interface. 1 could be untagged, this is native vlan.
The ports connected to your devices would be access ports, and they would be put into what vlan you want the device on and they would be untagged.
Catalyst 2960-X Switch VLAN Configuration Guide, Cisco IOS Release 15.0(2)EX
-
@johnpoz Thanks a lot.
Resuming, if I understand correctly what you wrote: I must go to the Vlan configuration on the Netgate and tag Vlan 10, 20 and 30.
I have already configure the trunk port on my Cisco.
Is my understandig correct?A
-
@afcarvalho depends.. You only show 1 connection there from pfsense, so I assume you are running multiple vlans over the same physical interface to pfsense.
if that is the case then yes vlans would have to be tagged in pfsense. You can only have 1 untagged network on a wire.. If you have multiple interfaces into pfsense for these different networks/vlans - then they don't have to be tagged. The uplink from your switch to the pfsense interface for that network could just be access and untagged.
The vlans would only have to be setup in the switch, and pfsense doesn't need to understand what tags the switch might use. Only when your going to bring in multiple vlans over the same physical wire (trunk) is when pfsense needs to know what the tags are.
As example of this I run some of my networks untagged on pfsense, where the uplink for that vlan is untagged it to a physical interface on pfsense. Then I run some networks that are tagged to a pfsense interface, because there are multiple vlans over the same physical wire.
-
@johnpoz Thank you again. I have defined the Vlans both on Pfsense and on the Cisco IOS.
I intend to assign Cisco interfaces /ports to each Vlan.
In the PfSense each Vlan manage a DHCP range and I intend to establish rules for a controlled routing between Vlan's (for example I intend to allow users from Vlan10 to comunicate to Vlan 20 but not to Vlan30.
These rules must be defined in pfSense correct?A
-
@afcarvalho yeah if you want don't want vlan X to talk to Y, then those rules would be configured on the vlan X interface.
-
@johnpoz One more question, If I may:
I assume that in Firewall Rule Definition, we always talk of inbound rules (source inbound - target outbound).
If I check the reverse option I am doing what?A
-
@afcarvalho there is no need rules on the destination vlan interface. The state that is created will allow the return traffic. Your destination vlan interface could have zero rules on it, and if you talk to it from vlan that allows the traffic, the answer would come back because of the state created when you allowed the traffic.
-
@afcarvalho said in Help on rules:
@johnpoz One more question, If I may:
I assume that in Firewall Rule Definition, we always talk of inbound rules (source inbound - target outbound).
If I check the reverse option I am doing what?A
There is no reverse option.
Are you talking about the "invert match" maybe? -
@afcarvalho said in Help on rules:
If I check the reverse option I am doing what?
This is, at least on the english language side, called "Invert" meaning the switcher of NOT.
Check the box and it will say the IP is NOT the value of what you entered then do something.
If you're using a language translation and it is stating something that does not mean 'opposite' or 'invert' or 'not' then please let us know by opening a redmine :)