Help with local port forwarding
-
Not sure where to post this, as its not quite under the DNS, its not quite under NAT, it might be routing... anyway, move where this should be please :)
ANYWAY:
I am trying to start setting up my local resolutions but need some specific port to be adjusted as i have certain services running off port by 1 (so, my TrueNAS runs its interface as port 444 rather than 443, same with my pfSense box).
Anyway, im trying to set up the forwarding rule, but i dont seem to be doing something right.
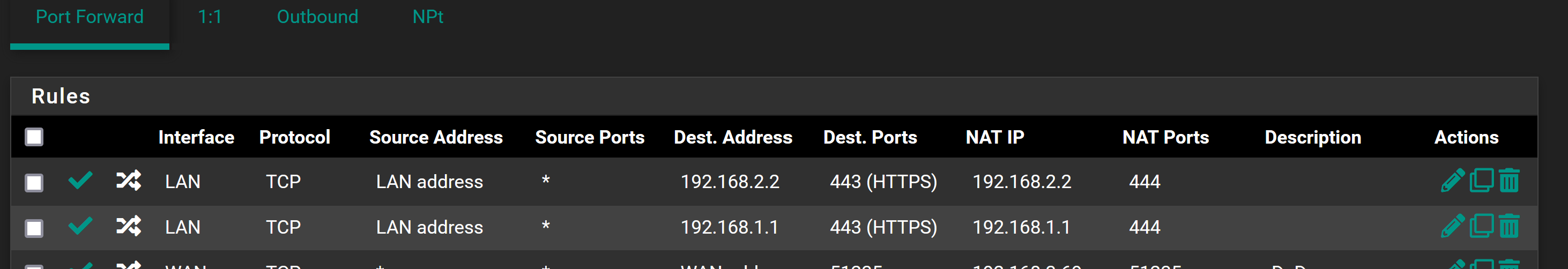
Attached is a pic of my NAT rule(s). I want all local traffic going to 192.168.1.1:443 to go to 192.168.2.2:444 (same with 192.168.2.2:443 to 192.168.2.2:444). Further accomplished by local DNS fulfilment (which currently works. if i go to pfsense.home:444 it takes me to my pfsense box.)
-
@menethoran
Source LAN address might not really be what you have. -
@viragomann well, i dont want ANY, because that would cause issues with calling servies from my truenas (192.168.2.2 which hosts services behind traefik on port 80 and 43, forcing everything into https)
-
@menethoran
I don't know, what you need. But your rules actually only forward packets coming from pfSense LAN address on LAN interface.
I'm in doubt that this one gets any hits. -
But 'LAN address' is the IP of the pfSense LAN interface. No traffic is ever going to come from there into the LAN. It can never match anything.
You probably want 'LAN network' there.That shouldn't ever match the Truenas address because I assume that cannot be in the LAN subnet. That portforward can never work if it is.
Steve
-
@stephenw10 switched source to 192.168.0.0/17 (i THINK thats the correct subnet to include all 192.168.X.X)
-
It would be /16 but that's probably not necessary. The port forward is on the LAN interface so the only traffic that can hit it will be from the LAN subnet or other subnets routed via some gateway on it (which you probably don't have).
Steve
-
@stephenw10 i have 2 networks (IoT and Home). IoT exist on 192.168.2.X-192.168.3.X, Home exists on 192.168.1.X. I want all local traffic trying to reach 192.168.1.1:443 (or more specifically, https://pfsense.home resolves to 192.168.1.1:444, it currently resolves to 192.168.1.1:443. 192.168.1.1 = PfSense, port 444 = port 443, but changed because of security?... (same with another service. though, ultimately, i dont really care if PFSense resolves straight to 443 and i just set the access port back to 443, BUT, i need to know that the 443 to 444 redirect works correctly, as another item on the network needs that to happen (ie, its access is on 444 becasue it cant exist on 443 because another servie monitors that port)
-
@menethoran and why would say 192.168.X.X/17 or /16 send traffic to pfsense if its trying to go to 192.168.1.1 or 192.168.2.2 ?
Not sure what you hoping to accomplish here?
If your devices on 192.168.2.2 and 1.1 listen on 444, then talk to them on 444
Why are you having them listen on 444 if you want devices to use 443 to talk to them?
What exactly are you wanting to happen, and we can either go over why that something doesn't make any sense, or how to do it. From what you have posted so far it doesn't make any sense.
But the only way a port forward for sending traffic to 444 vs 443, would be if pfsense receive the traffic to route to 2.2 or 1.1 from whatever client is trying to talk to those IPs. But if your devices are on some /16 or /17 network that includes 2.2 or 1.1 they would never send the traffic to pfsene in the first place.
-
@menethoran said in Help with local port forwarding:
but changed because of security?
Huh - changing the port, that your going to allow anyway even if using some other port to get there isn't security..
My pfsense listens on 8443 for access to the gui.. To get to the gui I go to https://sg4860.local.lan:8443, this is pfsense name on my network. I use 443 for openvpn, and also allow for that to be forwarded to another service behind pfsense, etc. So yeah that is why I don't have pfsense gui listen on 443.. Because I want to use 443 for other stuff other than the gui.
Devices I want to allow, I allow networks or devices I want to allow to talk to 8443.. If I don't then I don't let them talk to that IP:Port
-
I assume then that LAN here is Home?
A port forward on LAN should then be:
Source: LAN net
Destination: LAN address
Target: LAN address (though you could also use localhost here for clarity).Steve
-
@johnpoz basically, i want it to function like yours does, except i dont want to have to append the port. as far as pfsense is concerned, as i stated previously, i dont care if i switch that back to 443. it was originally set up to 444 for (iirc) security reasons. as ive now further locked down my network, i am less concerned with the 443 vs 444 on pfsense, HOWEVER, my NAS machine needs the interface to run on port 444 because traefik binds port 443 and port 80 to handle internet traffic. i want to be able to connect to the NAS machine via ssl locally, and to do that, i need pfsense to handle local traffic headed towards the NAS machine to come in on 443, but be forwarded to 444 in between my client and the NAS... i would like all of my connections to be ssl, including my internal stuff as much as i can.
-
@menethoran said in Help with local port forwarding:
handle local traffic headed towards the NAS machine to come in on 443
Is that traffic pfsense would route? pfsense is not involved in conversations between devices on the same network.
If you have this say
client lan -- pfsense -- optx -- nas
Where client and nas are on 2 different networks you could do with with simple port forward.
If nas and client on same network, you could do it with say a haproxy setup, where you hit a port on pfsense, and the proxy sends it to the nas.. I do this for couple of services, since I am having haproxy do the ssl offloading, and the destination services run on odd ports and don't even support ssl, etc.
-
@johnpoz oh, thats a FANTASTIC idea, i hadnt thought of using haproxy to do this!