iPhone w/ manually configured IPv4 - not in DHCP leases list
-
Hi all,
Home network, pfSense + UniFi.Considering:
- I wish to make static mappings for all of our home devices
- iPhones use "private WiFi" i.e. fake MAC addresses
- Those MAC addresses keep changing
- switching off "private WiFi" will raise an iOS "privacy warning" in WiFi settings so clients re-enable this feature outside of my control
Solution:
Configure the iPhone to use manual IPv4 (in iOS settings -> WiFi -> i -> Configure IP -> Manual) for this particular network SSID only.Result:
- that iPhone always connects using the same IP. Good.
- FW rules based on IP do work. Excellent, this was the objective
Question:
In the pfSense DHCP leases list, the IP doesn't show up. I chose an IP outside the DHCP pool.
I do understand that this particular IP wasn't assigned by DHCP so it's not a "DHCP lease" but it is a lease. So where can I see it listed in pfSense?
Also, in UniFi Client Devices I do see this device with the correct IP. -
@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
but it is a lease.
No it isn't - not if you set it on the device. You would see it pfsense arp table if you looking for it and it has talked to pfsense say in the last 20 minutes. Which is the default arp cache timeout
-
@cabledude alt approach: set DHCP to reject requests from unknown MAC addresses. Then if they enable private MAC they can’t connect. Unless they configure a static IP that is allowed out.
-
@steveits said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
@cabledude alt approach: set DHCP to reject requests from unknown MAC addresses. Then if they enable private MAC they can’t connect. Unless they configure a static IP that is allowed out.
You can also use an MDM solution like Microsoft Intune to force the setting via configuration policy on a Wi-Fi network basis. This is what I do on all of my devices.
If you want to make it simple, use MAC address Filtering on your Wi-Fi network blocking all unknown MAC addresses.
-
Thanks all for explanations and suggestions. Highly appreciated.
There is actually one other reason I wish to use static mappings for all trusted devices: monitor which devices connect to my network. My reasoning is: any new leases issued by DHCP (IP in DHCP pool) should be considered either new or unauthorised. Forcing known MAC would work for trusted devices, but I would not be able to add new devices without making a temporary settings adjustment.
Would there be a simpler way to scan leases for unauthorised devices?
MDM sounds great but too heavy for my simple home network.
-
@cabledude Who is turning back on the private mac setting on their devices? Can you not just tell them not to do that - and if they do they just wouldn't have access to the reservation you setup so they get specific IP?
I use reservations for all my devices as well - but then I don't then go and turn on random mac setting, and my wife doesn't either ;) heheh
-
@johnpoz said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
Can you not just tell them not to do that
Can you talk to my wife about that please?
@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
I would not be able to add new devices without making a temporary settings adjustment
We allow DHCP by MAC in our building so that people can't just plug in if they aren't a paying tenant. The DHCP log will show the repeated lease request...usually every few seconds so it's rather obvious. It can be set to ignore those to save the logging, then un-ignore to see them when you add a new device. But then again homes have many devices nowadays and it seems to be an ever growing list at mine.
Using an IP is tricky...likely the kids will eventually figure out a static IP that works for example, unless they aren't geeks like us. Wi-Fi can sometimes be set to allow/block by MAC address for example.
-
@johnpoz
No one has actually done so yet, but if my kids would actually do it they would get a new, different IP from DHCP pool and evade screen time restrictions I set up in FW rules.Part of this is the perfectionist in me trying to set up a solution to manage trusted devices (like yourself) and check for rogue stuff at the same time.
MAC filtering for security considerations isn’t 100% solid as MAC can be spoofed so I figured I’d leave it open and monitor the lease table.
-
@steveits said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
It can be set to ignore those to save the logging, then un-ignore to see them when you add a new device. But then again homes have many devices nowadays and it seems to be an ever growing list at mine.
Where do I control that ignore / unignore?
Using an IP is tricky...likely the kids will eventually figure out a static IP that works for example, unless they aren't geeks like us. Wi-Fi can sometimes be set to allow/block by MAC address for example.
Actually no, as long as their phone doesn’t show alerts like “privacy warnings” I can get away with setting a manual IP on their device without them noticing.
Enforcing MAC filter would work but I wouldn’t see any blocked attempts, unless by checking the logs as you do, but this I would need to learn how to.Is there any way to receive alerts from pfSense in case someone tries to get in?
-
@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
Where do I control that ignore / unignore?
Sorry I was thinking of these:
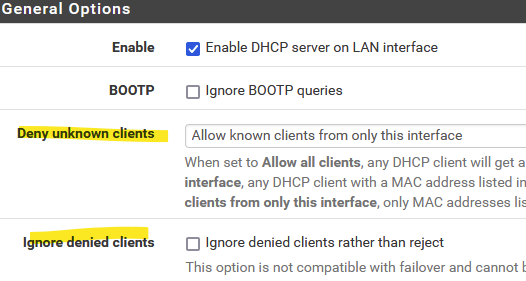
There the ignore setting is for MACs you have set to deny, further down the page under "MAC address control."
Tbh the "ignore" seems a bit inconsistent...sometimes I find it logging anyway until I restart the DHCP server. But not always.
-
@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
Is there any way to receive alerts from pfSense in case someone tries to get in?
As in, log in to pfSense? There are various login protection options in System/Advanced/Admin Access but I haven't tried to see if it notifies. Probably?
-
@cabledude solution to that is don't worry about what IP they get, just give them access to ssid vlan that has the restrictions for everyone ;)
Don't give them the psk to any of the other wifi networks..
-
@johnpoz
Yes the kids are on the "trusted devices" VLAN, just like my laptop, appletv, all phones and iPads etc.For the kids I created a FW rule in this VLAN that allows an IP alias (containing their IP's) during a schedule (Firewall -> Schedules). It works as long as their devices connect to their static mappings. This is only enforced when their MAC addresses are always the same, hence my need to either (a) keep them from using the "Private WiFi" feature or (b) use a manual IP set on each of their devices.
I will get this sorted on my own.As for the other issue: monitor rogue DHCP connections. The best solution would be all static mappings for known devices and have pfSense send an email notification for any new MAC address that successfully connect.
Alternatively I could allow only known clients in DHCP but then I'd have to change that to all clients if I want to add a new device.
-
@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
No one has actually done so yet, but if my .... check for rogue stuff at the same
Discover the magic :
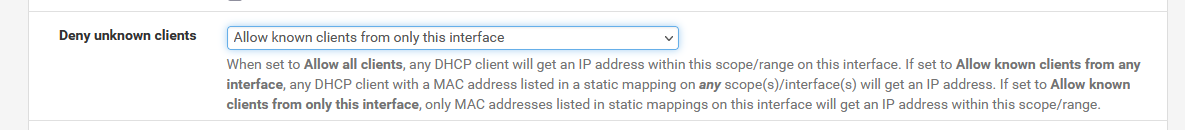

When they, kids etc, decide to delete the Wifi profile, and re connect from scratch, their iPhone/pad/whatever will default to 'randomized MAC'. This means they can't connect anymore, as their Phone will not get recognized.
They will have to de activate this option - slide to the left :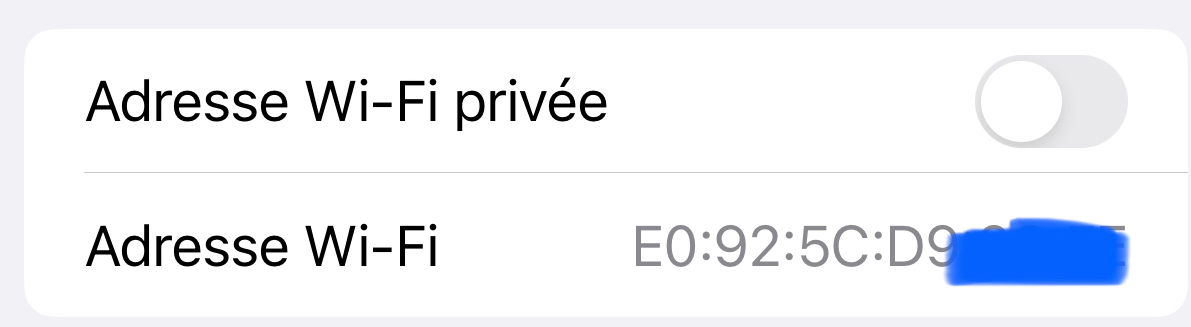
Of course, they forget to do that, sliding the Wifi private address selector to the left, as they have forgotten that 'home' is a trusted, secured place. The result is : they won't get an IP anymore. "Now, its really broken".
I just say to them : "why deleting the Wifi profile in the first place ?"
and
"You do close the front door when you leave home ?"The thing is : I've nothing against this 'randomize MAC by default' as it can be useful for every Wifi spot, except the home.
So, no need to explain what so ever to the wife or kids : it's an auto learning process.
They do something wrong, they assume the consequences.@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
Is there any way to receive alerts from pfSense in case someone tries to get in?
There are many options.
Use the LAN interface for yourself, and only accepts trusted devices on this network.
Everybody else : on another (OPT1) interface, where you simply block all traffic that wants to go the the OPT1 IP (= pfSense): Block port 22, 80 an 443, and you'll be fine.
Use a difficult password.
See what System > Advanced >Admin Access => "Login Protection" can do for you.iPhone w/ manually configured IPv4 - not in DHCP leases list
To be in the list, the DHCP server has to receive a DHCP request from the (DHCP) client device.
The thing is :
When you set manually the IP details like IP, gateway and DNS, you de activate the DHCP (client) process. The device needs IP info to use a network. It can use DHCP, and this is the default method.
Or you do it manually.
It one or the other.So, the pfSense DHCP server never receives a DHCP request from that device.
So, it will never create a lease for that device.
So, there will be no lease.Please confirm that you
 right now.
right now. -
Dear Gertjan,
First of all: thank you very much for the time spent on your part, I highly appreciate that . I will reply below:
. I will reply below:@gertjan said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
The thing is :
When you set manually the IP details like IP, gateway and DNS, you de activate the DHCP (client) process. The device needs IP info to use a network. It can use DHCP, and this is the default method.
Or you do it manually.
It one or the other.Quite right. UniFi works differently and does list devices with IP set manually-in-device. Like you said, I have now come to understand that pfSense only shows actual leases (i.e. issued by the pfSense DHCP Server service) on the "DHCP leases" page. Oh well.
Furthermore, devices with manual IP configured-in-device actually do function properly and firewall rules with exceptions based on IP actually do work for these devices too, even though we can't see them in the leases list. But I like seeing them so I'm back to all DHCP now.
Discover the magic :


Yes I am familiar with this setting and I've used it successfully in the past for quite some time.
Rogue IP lease monitoring
At some point, couple of years ago, I went back to "Allow all clients" because I wanted to monitor the leases list to make sure there weren't any rogue IP clients popping up on the grid. So because all my devices have static mappings, basically all was well as long as no new leases in the DCHP pool would come up.But then Apple introduced Private WiFi - randomized MAC and of course new leases popped up for every iOS device, hence the attempt to revert to manual-in-device IP configuration (see above).
It took a while for me to discover (my bad) that the Private WiFi option is selectable per WiFi network so initially I let it play. Soon after that, I figured out I can set their devices to Private WiFi OFF for the home WiFi SSID and ON for everywhere else. Great insight.
So I set all family iOS devices to Private WiFi OFF and reworked the static mappings list. So far I have still kept DHCP settings at "Allow all clients" for this particular VLAN to be able to monitor new devices connecting.
But there must be a smarter way to do this

Of course I could re-enable "Allow known clients from only this interface" and rely on the firewall to let no other devices connect in the first place, which is what others on this page do.
When they, kids etc, decide to delete the Wifi profile
I suppose by deleting the WiFi profile you mean they tap the network and then tap "forget this network"?
, and re connect from scratch, [...]
So, no need to explain what so ever to the wife or kids : it's an auto learning process.Ah yes, now I know for sure that is what you meant - forget this network.
They do something wrong, they assume the consequences.
Okay, I am now very seriously considering to turn on "Allow clients from only this interface" again.
But...
@cabledude said in iPhone w/ manually configured IPv4 - not in DHCP leases list:
Is there any way to receive alerts from pfSense in case someone tries to get in?
There are many options.
Use the LAN interface for yourself, and only accepts trusted devices on this network.
Everybody else : on another (OPT1) interface, where you simply block all traffic that wants to go the the OPT1 IP (= pfSense): Block port 22, 80 an 443, and you'll be fine.I created separate VLANs, which may or may not be what you mean, but VLANs are effective.
However my own "trusted" devices currently are in the same VLAN as the other family phones, pads, laptops. like you did, I may move my own to the LAN, thanks for the suggestion.Use a difficult password.
Obviously got that, it's in my iCloud Keychain.
See what System > Advanced >Admin Access => "Login Protection" can do for you.
Added some fields there, thanks.
So far I have used OpenVPN to access pfSense from outside the firewall and that is the most secure.
I am now considering using Synology reverse proxy (with domain name and certificate) to allow for easy access to pfSense, outside and inside. But something is holding me back. HTTPS should be secure but attackers can get to the login screen easily. I disabled the admin account, but still...
Please confirm that you
 right now.
right now.

