Outbound NAT "A valid target IP address must be specified" while everything appears to be valid?
-
Hello all,
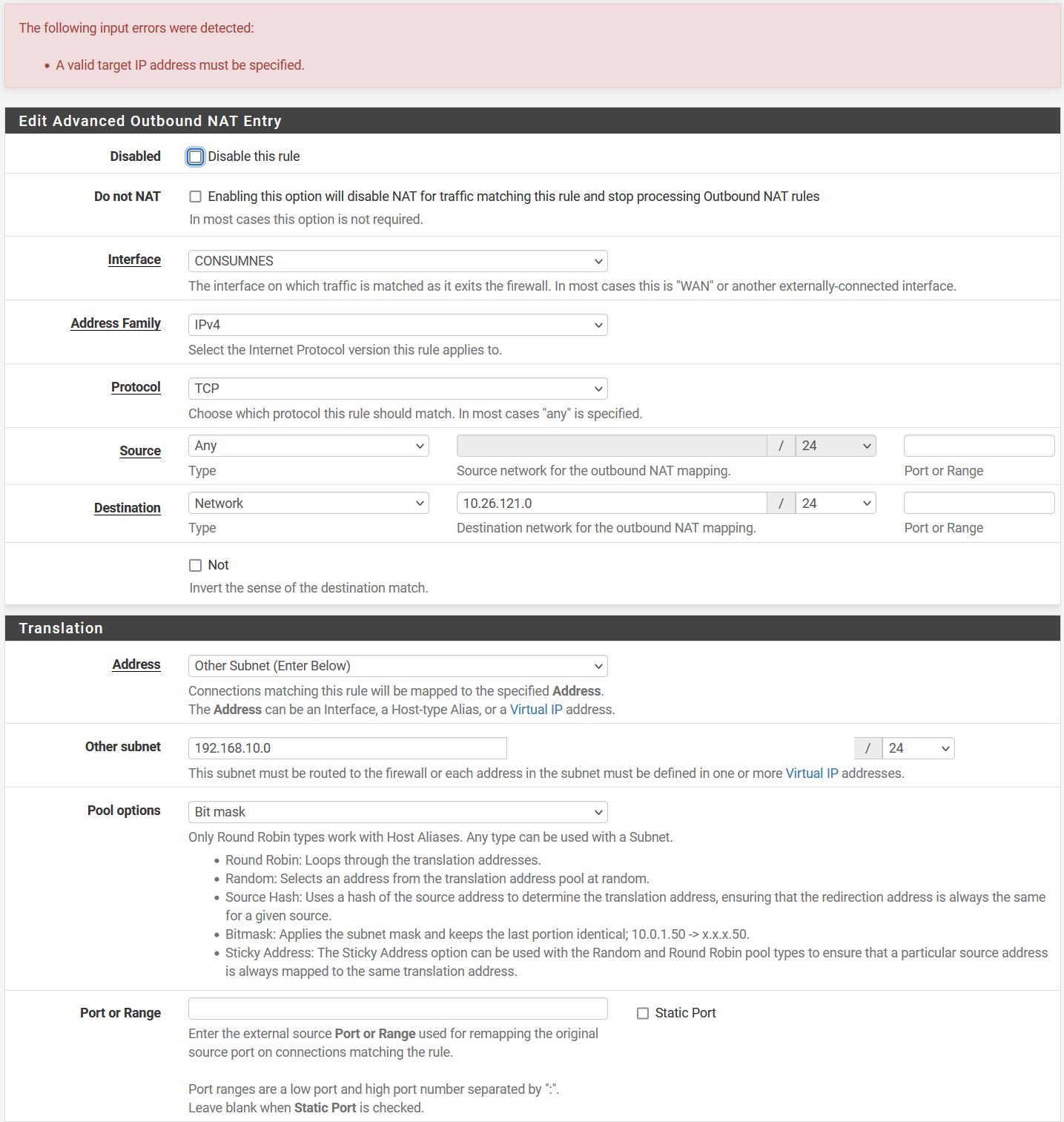
I am trying to set up an outbound NAT to translate an internal subnet to potentially colliding client subnets over a routed IPsec tunnel. Every time I try to enter the NAT into Outbound NAT I get an error "A valid target IP address must be specified." but I don't see any errors. Can you please tell me what I am doing wrong so that an internal device can communicate across the lan to 10.a.b.c and translate it to the customer's 192.168.x.c?
-
-
@sticcino Set a Source network or IP or alias, e.g. the LAN subnet.
https://docs.netgate.com/pfsense/en/latest/nat/outbound.html#working-with-manual-outbound-nat-rules
"Avoid using a source address of any as that will also match traffic from the firewall itself. This will cause problems with gateway monitoring and other firewall-initiated traffic."edit: or that

-
@SteveITS Thanks, I had tried that as part of it, but I figured that either I was being a total idiot about NAT or it was an issue such as the one JimP sent...
@jimp Thanks for the response, that looks like it. FWIW, I also see it on plus 22.x and on CE 2.6.0 with patch manager having the suggested patches applied.
-
Okay, so what am I messing up now, that when I edit it in XML, even with the source specified to 172.a.b.0/24 I see it translating the source instead of the destination??
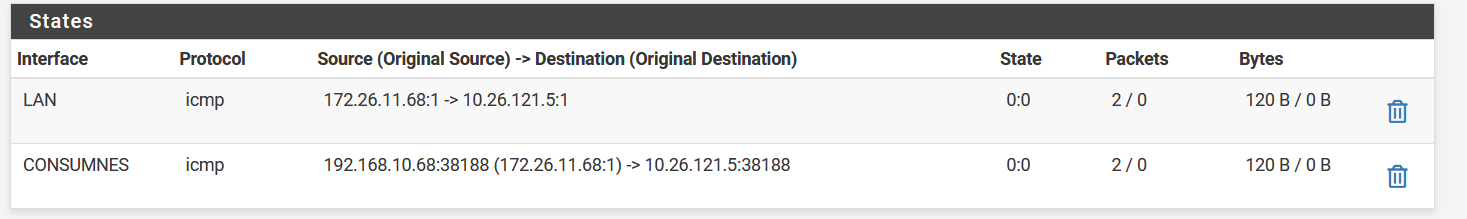
I expected since this is an outbound on the destination, the destination should be trasnlated??
-
@sticcino Outbound NAT is going to translate packets arriving from Source, going to Destination, to the Translation address.
It's typically used, for example, when a router has multiple IPs set up as WAN IP + virtual IPs, and a particular outgoing connection should use a VIP instead of the default WAN IP. Say, to isolate SMTP traffic or something like that.
Is 10.a.b.c set up on your router? It might be a port forward is more applicable here? Not super clear on the goal.
-
@SteveITS Trying to use NAT to translate destination addresses. I have multiple connections over VPNs with colliding subnets that cannot change (and I have no control over those networks), and I need the addressing to be transparent. I want to be able to send traffic to 10.a.b.server on my side and translate it to the customersub.server as it goes out the ipsec tunnel.