Trouble accessing pfSense Web Interface when WAN is down
-
I've got two internet connections, and when both go down, I'm am unable to access the pfSense web interface. Strangely, SSH also stops working. Even a reboot doesn't seem to resolve the issue.
My network setup involves three VLANs - one for my main PC, another for servers, and the last one for Wi-Fi. Here's the kicker: the web GUI sometimes works, but only when I'm accessing it from my main PC VLAN.Any ideas or suggestions on how to troubleshoot and fix this would be greatly appreciated.
-
@milindhvijay internet connection being up or not would have nothing to do with lan side access. Now the gui can be very sluggish if dns is not working..
But ssh should have no sort of issue, can you ping pfsense IP?
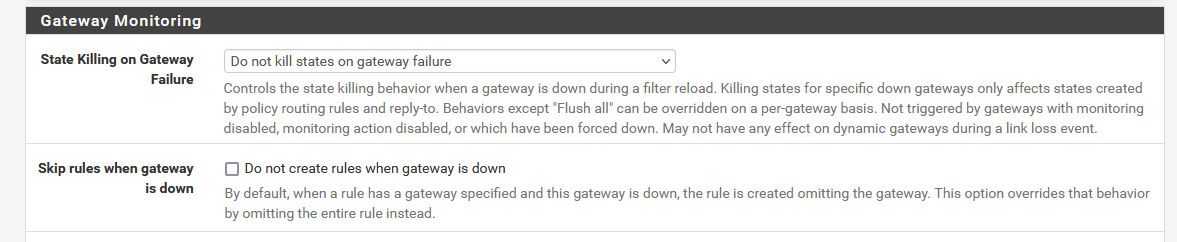
Do you have pfsense to kill states when internet goes down? Do you have gateway setup in your rules - where skipping rules could cause you not to have access.
So on your lan what are your rules? Do you have any floating rules? By default the anti-lockout rule should allow you access to your gui and ssh no matter what.
But generally speaking, your wan being down should not be causing access from lan to be hindered.. Now without dns (ie wan down) the gui can be very sluggish to respond - it likes to do its checks as its loading..
How are you trying to access? via some fqdn (dns being down could prevent this) or just IP?
-
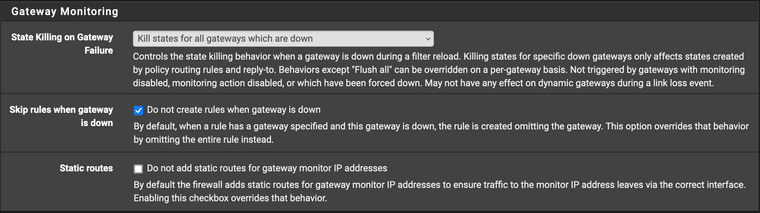
Yes, I have set it to kill states for all gateways which are down.
I do not have anything in Floating tab except for pfblockerNG and QoS. Both FQDN and IP wouldn't work.
I have seen posts online with the same issue and the only workaround was meddling with fetching of EULA.
-
@milindhvijay said in Trouble accessing pfSense Web Interface when WAN is down:
meddling with fetching of EULA.
What? Can you link to such a resource?
You have it set to kill all states when gateways fail - so you would have to create a new state to connect to the gui after internet goes down, because all existing states would be killed.. Turn that off.. Or create a new session to connect after your internet goes down.
Do you have a rule with a gateway in it on your lan side? Your setting there would not create a rule if the gateway is down.. Can you post up your lan side rules please.
Your not running vlans on the physical interface are you - if the physical interface goes down, then any vlans on it would also be down
Here didn't really want to shut down my real internet, but I killed my pfsense VM gateway access - see how it shows offline.. So to pfsense that internet connection is offline.. And ping never went away.. I started that ping before I shutdown the gateway, didn't loose a packet.
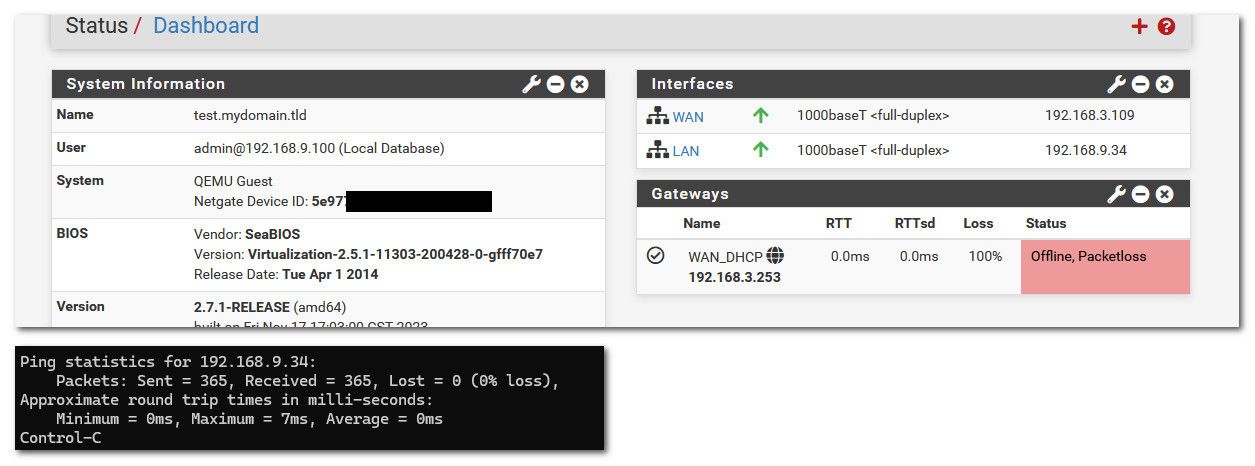
In a typical setup pfsense wan going down, or gateway offline has zero to do with lan side interfaces. So either you have rules that are going away, or you are killing states? And need to restart a connection from your client or your whole physical interface is showing down? And your vlans on that interface because its actually down would not work..
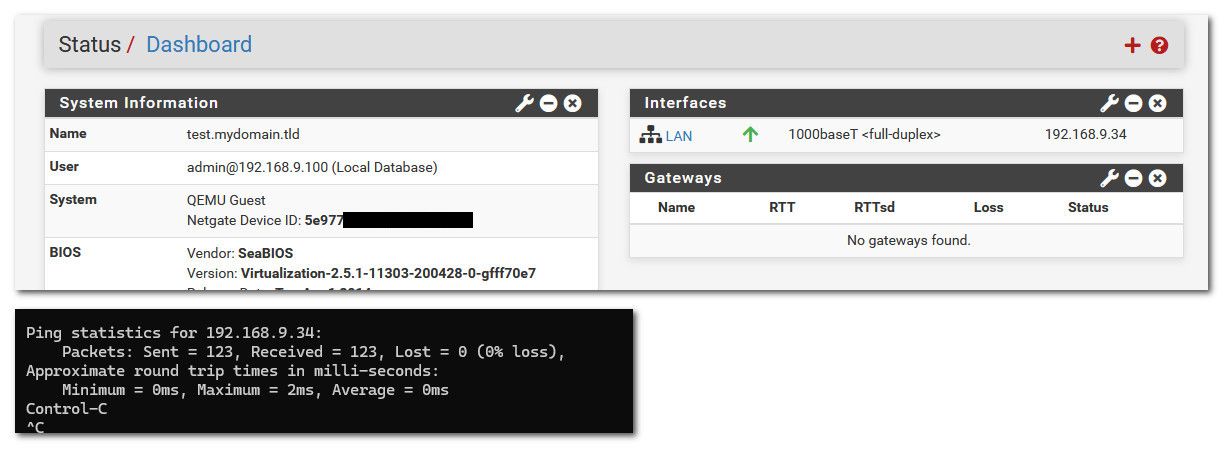
edit: here I turned off the wan in pfsense, and still have access to the gui, didn't loose single ping to the lan IP.. ssh to it still works
-
@johnpoz said in Trouble accessing pfSense Web Interface when WAN is down:
What? Can you link to such a resource?
There are some posts suggesting a host override for ews.netgate.com which means the check for updated license terms will timeout immediately instead of potentially delaying loading the dashboard. But I don;t recommend that. And in most cases it does nothing useful anyway.
Steve
-
@stephenw10 said in Trouble accessing pfSense Web Interface when WAN is down:
There are some posts suggesting a host override for ews.netgate.com
So users without a clue suggesting borked shit to fix their lack of understanding ;) yeah very typical of "help" on the internet hahahah
While that might remove the few seconds of delay dns not working and having to time out.. I concur its a not a good idea ;)
-
@johnpoz I set kill states for gateways which are down because previously had some issues with failovers.
I have 3 VLANs and I thought the Anti-Lockout rule on LAN would suffice for all other VLANs as well. Right now I added a new rule on wifi vlan and I can access GUI when both WANs are down (PON Loss)

@stephenw10 Thanks both of you.
-
@milindhvijay still not understanding what the issue is exactly.. Your wan being down has nothing to do with vlans routing between each other.. Pfsense can route between devices connected to it be the "wan" is there or not..
The lock out for lan is only for "lan" that would be a pretty shitty rule if set on the lan, and it allowed any network device on any network of pfsense to talk to the gui..
Wan being down should only be problematic is if you had rules that had a gateway set in them.. Then pfsense can either not use that rule if the gateway is down, or create the rule without the gateway being used..
Did you have such rules - not exactly sure how policy routing to one of your gateways would even get you to your lan IP for the gui, where you accessing the public IP to get to the gui?
I have to assume you doing some sort of gateway settings in you rules since you mention you have 2 wans, to leverage load balancing this is normally done by setting the gateway as the group that has the wans in them, etc..
So I have to think something related to that is what was causing you your problem.. Creating a rule that allows what you want without policy based routing, ie not gateway set would remove any settings for pfsense to change the rules that have gateways set, etc.
-
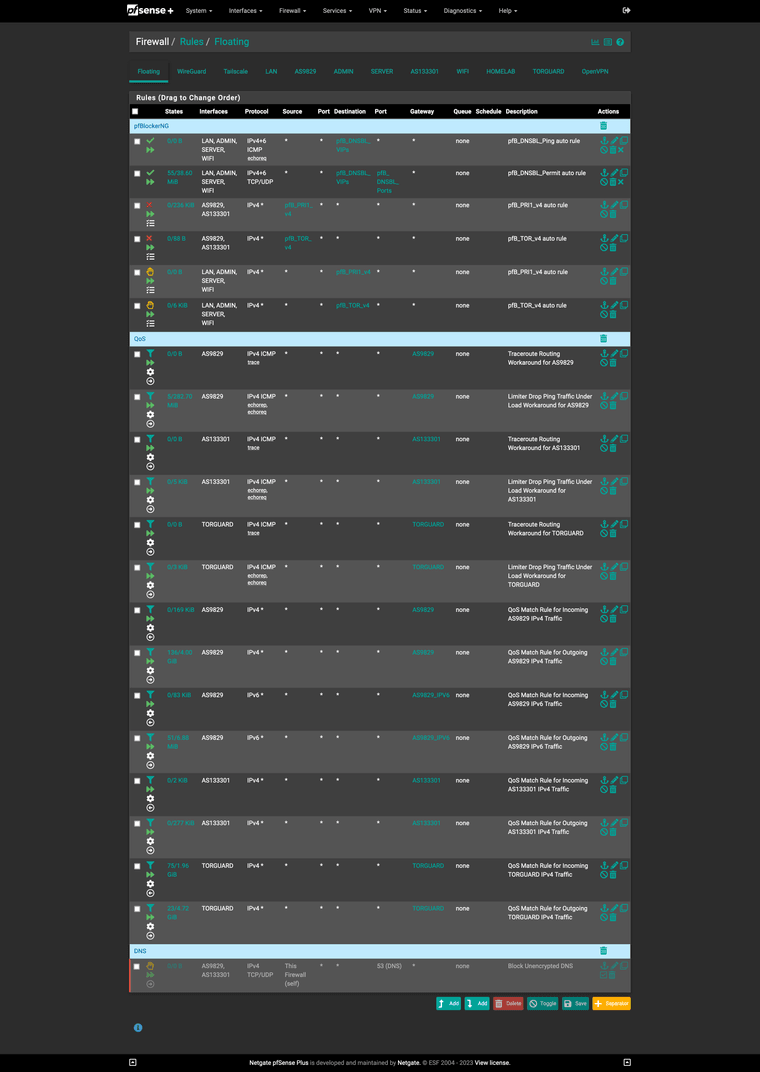
@johnpoz Here are all my Firewall Rules.
Floating:
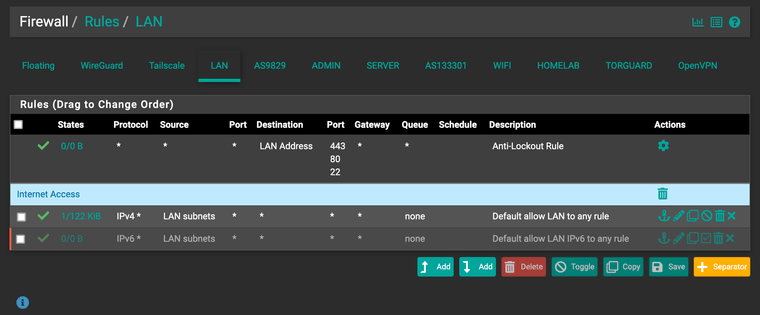
LAN:
VLAN 10 (ADMIN):
I had this highlighted rule which explains why I was able to access GUI from this VLAN when both WAN is down.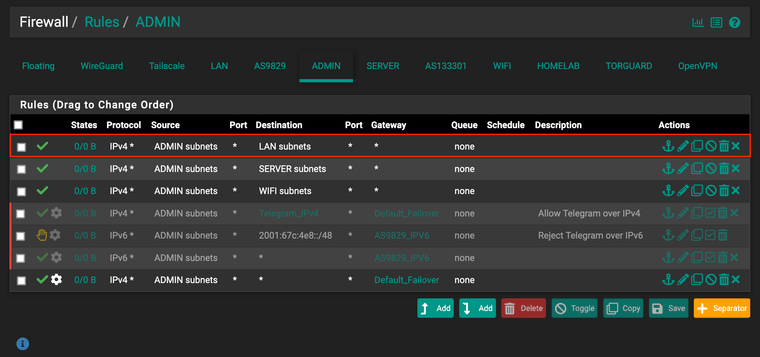
VLAN 30 (WiFi):
Before adding the highlighted, I could not access GUI when WAN was down.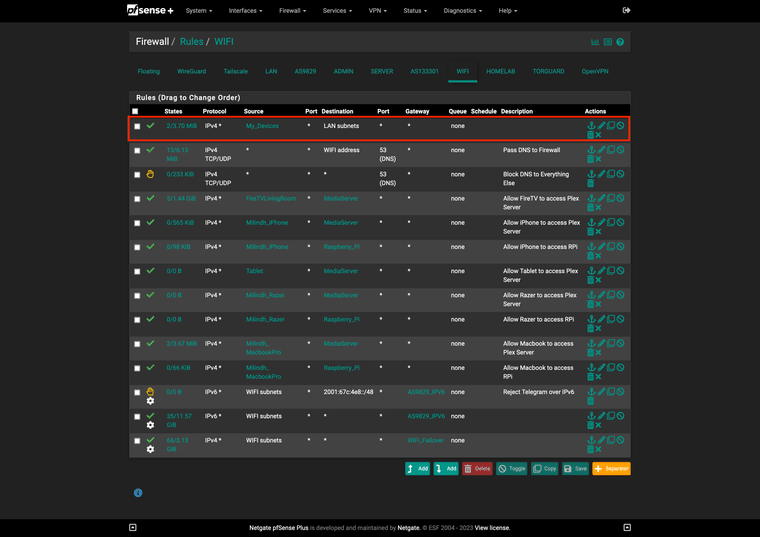
-
@milindhvijay So like I was say if you have a rule using a gateway, which you have. And you have it set to NOT create rules when gateway is down.. Before you had no rules that would allow access to the IP on your admin vlan.
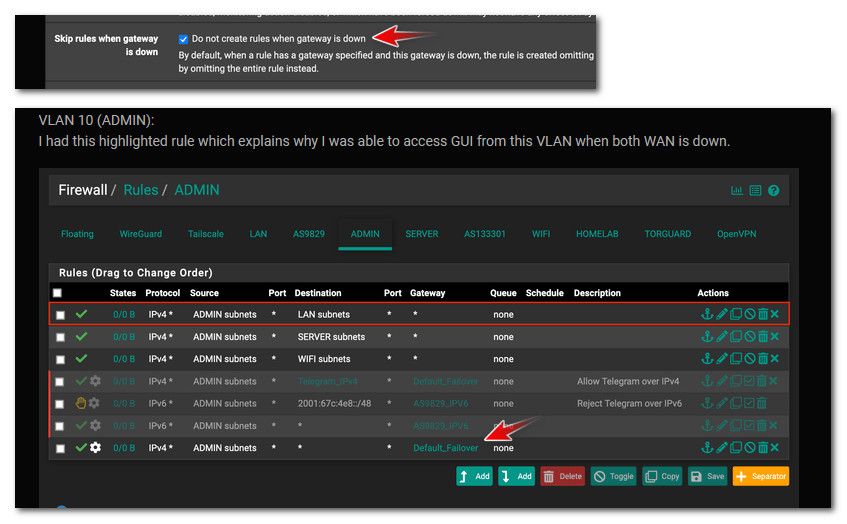
So when your gateway goes down, per your settings that last rule there with the gateway set as "default_failover" would not be there.. So until you added that rule you have highlighted what rule if you remove that last one since you are telling it not to create rules when a gateway is down would of allowed you access to pfsense gui on any IP?
If that rule you created is to allow access to web gui, why would you say lan subnets. Why would you not just allow access to the admin interface address?
But yeah your rules from before you added completely explains why yes if your wan(s) were down you would not be able to access web gui or even ssh.. Because you had no rules that allowed it when your gateway(s) are down.
I brought this up in my first post..