Want to setup squid-proxy and squidguard but have lots of questions.
-
My primary objective is to filter web content viewed by my children. I've been reading the documentation on how to install and setup squid proxy and squidguard. The problem is that the documentation seems to assume a basic starting point/configuration (which makes sense) but my setup is already pretty complicated. I want to make sure that setting up squid-proxy and squidguard isn't going to break some of the other things that I've already setup.
Here are my questions:
-
I've noticed right from the start of the documentation that, "The add-on packages Squid, SquidGuard and Lightsquid are deprecated in pfSense Plus and pfSense CE software." Should I stop this effort all together at this point? What would be the alternative to use if my primary objective is to filter what web sites my children are accessing? I'd like it to be a transparent proxy, meaning I don't want to go around to each device and configure proxy settings. Since this package is deprecated, is my only option now to setup a dedicated proxy server and configure devices to use it? If the answer to this question is to stop this effort right now due to this package being deprecated, and setup a dedicated squid proxy server, then the remaining questions in this post can be ignored; except for maybe question 2.
-
Related to question 1, I have a few devices (iOS) that have Qustodio installed. Qustodio is a parental control utility that monitors our kid's activity on their phones and tablets. It accomplishes this by establishing a VPN back to the parent company. Will Qustodio bypass the proxy? In other words, would establishing a VPN on a client machine get around the proxy and squidguard? You might ask, if I'm paying to Qustodio then why do I want squidguard? Well, Qustodio doesn't support Linux devices. I have several Linux laptops that are shared by my kids, I don't want them getting around the content filtering on their iOS devices by using the Linux laptops.
-
I want to use SSL intercept. The instructions say that I need to create a Certificate Authority. I believe I already have one. Additionally, I'm using acme/haproxy with SSL certs signed by Let's Encrypt to perform SSL termination and reverse proxy for my web services. Should I / Can I specify the CA that's being used for those? Does Squid care which CA I use? The instructions don't seem to indicate whether it matters which CA is provided.
-
I have several family members who VPN into my house to access my web services. Will squid somehow start proxying for those connections? I would want to avoid that. How can I ensure that they'll still be able to access my house once I've setup squid? I suspect I just exclude those connections from the squid proxy configuration.
-
I have setup a wireguard VPN connection to a VPN provider and configured pfsense to forward all internet traffic down the tunnel first. I've done this with the expectation that our ISP won't be able to monitor our internet usage. Will the Squid proxy know to forward all of its traffic down this tunnel too? I know this sounds like a contradiction. I want to filter internet content for my kids, but I don't want my ISP seeing what we're doing. This is the weird dichotomy of being a (paranoid) parent and a (paranoid) computer geek at the same time.
I guess that's all my questions.
-
-
i'm interested in a somewhat similar concept as well regarding the tsl/cert thing, particularly your 3rd point.. hopefully folks will chime in.
the problem is as of yet, getting squid updated and supported with pfsense has been iffy.. one of the guru's on here created an update package that, after installing the latest version of pfsense, you could get squid updated, however it requires running scripts that he wrote, and while they work well, if most people are shying away from squid/clamav because 99% of all web traffic today is encrypted, so clamav won't really serve a purpose.. even suricata and snort can't do their jobs to their full capability because of the encryption, but i digress..
i was wondering if the following setup were possible:
- use haproxy for tls termination on the wan,
- from there, send all unencrypted traffic to another device that's piggy-backing off the pfsense box. a small box that's running linux with a full-fledged modern antivirus solution (like crowdstrike or sentinalOne for example) for scanning,
- the stream gets sent BACK to the pfsense box to be further scanned by suricata (or snort),
- data stream moves on to the clients, maybe re-encrypting it to satisfy the browsers and other apps that would otherwise complain..
it seems like it should be possible.. the modularity of it all is a nice idea because if i'm not satisfied with the antivirus solution, i can just install another one instead of being locked into clamav..
i figured linux for the AV part because there are far more enterprise grade AV solutions for linux than freeBSD.
overly complicated? meh.. maybe.. but that doesn't mean it wouldn't work, especially for a small network.. plus it's less expensive and more flexible than something from palo alto..
sure, put crowdstrike on the clients and call it a day, but i'd like to be able to stop the bugs from getting in at the firewall rather than wait until their in..
opinions?
-
I use it and love it. It requires a lot of work to configure it, and certs installed.
https://forum.it-monkey.net/index.php?topic=23.0
My favorite guide for Squid and Squidguard.
I use custom settings here.
Some devices are splice only
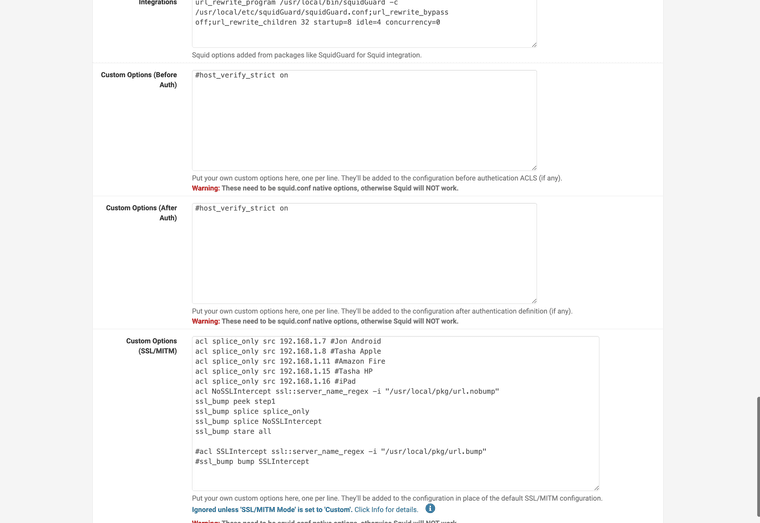
I have a regex based splice only file for sites you always want spliced.
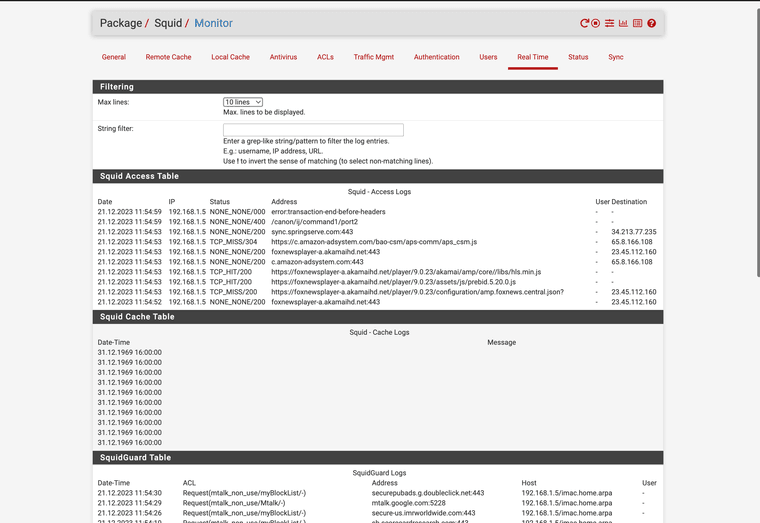
Works great it has amazing code, Marcos worked wonders on it. I will let my 2100 die with the version that supports it.
Here is it running in real time
My accelerator running.
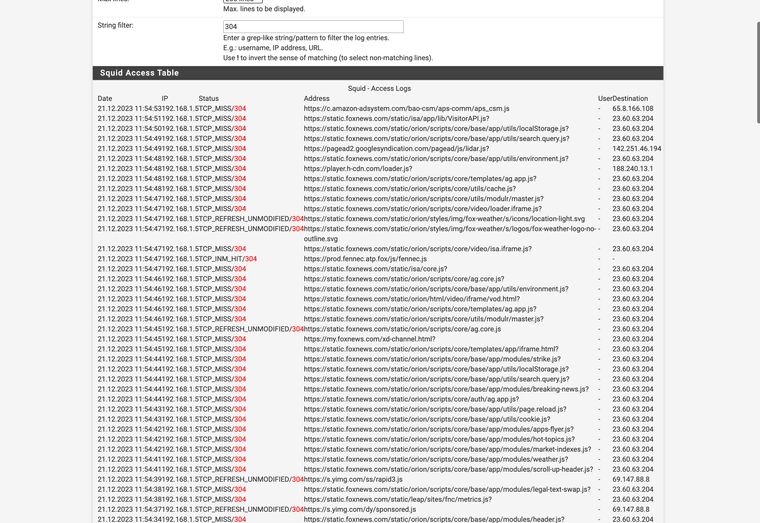
A blocked URL
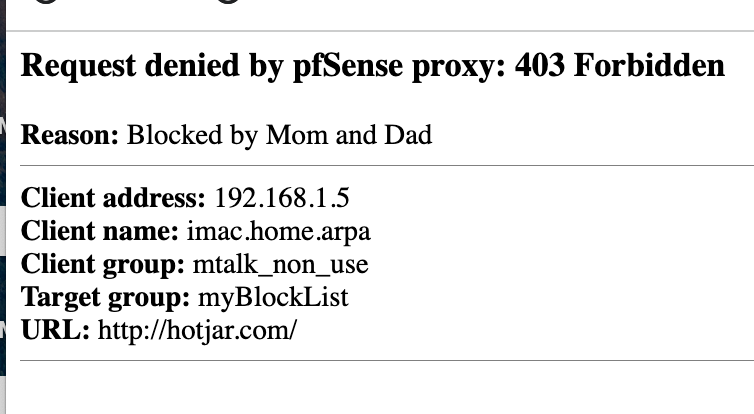
-
could you use a wpad configuration to auto input your proxy into web browsers instead of installing a cert on each pc?
that has always interested me -
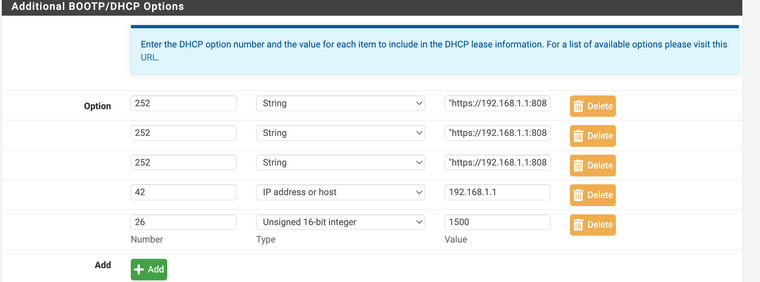
@jc1976 Yes use DHCP option 252 with it point to your wpad
"https://192.168.1.1:8080/wpad.dat"
It is the most amazing package. It is complex to configure..
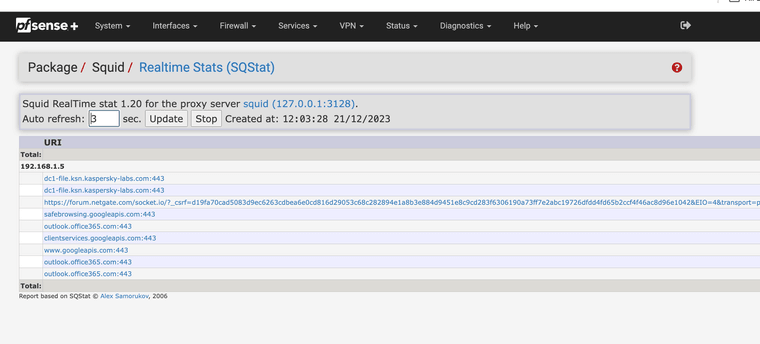
Real time view with litesquid
It doesn't care about DoH or DNL over TLS.
It is simple it looks at the get requests and blocks.
Of course you need the splice list for office stuff outlook teams email. The URL blocker is amazing. Thank you Marcos!!!! very secure consumer side cybersecurity tool. Big Tech hates it. It's the giant spotlight of cybersecurity.
-
it's even got on the fly https/http antivirus if your system has the RAM for clamAV. It will stop a virus and show an error page.
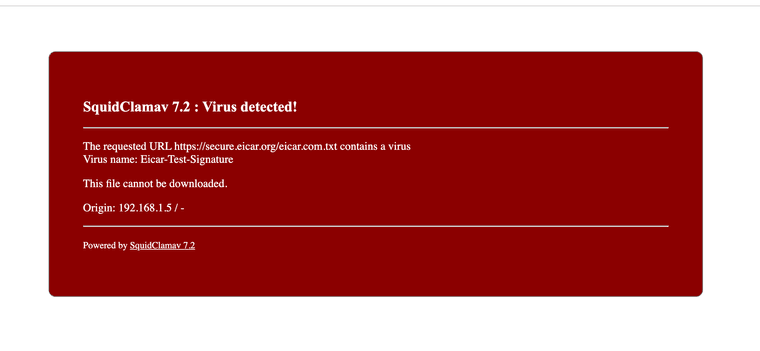
-
@jc1976 I use SSL certs, it can't run without them, you got to own the hardware to install the certs.
-
If we did this feature request add on anyone could use it
https://redmine.pfsense.org/issues/14998
It would make the splice lists as easy as pushing a button on the proxy.
Its not a recommended package Netgate depreciated it for a DNS based blocker.
I dislike DNS versions..
-
the only problem with all this is netgate seems to be trying to phase out squid.. hence my thought of being able to splice in a linux box that could handle inline antivirus scanning as it came through the firewall, after tls termination at the wan.
-
regarding your request to have the ability to "not cache" anything, unless i'm reading it wrong, it does have that ability..
under "services -> squid proxy server -> localc cache" at the top you can 'disable caching' by checking the box, and at the bottom of the page you can specify how much ram you'd like to commit to squid caching, if you were to enable caching.. as for hard drive cache system, i have that set to 'null' and for memory cache size i have that at 2 gigs.. but again, if don't enable caching, it seems to me the packet stream would be scanned inline without being cached.
-
@jc1976 I want to cache with it. I like it. I use affordable DSL, so it helps keep everything smooth and my bill down. Yes you can disable caching completely, you can even disable ClamAV if you want and only use splice mode for a URL blocker. So you don't even need certificates like that. Again, with this version you could run it in transparent mode and never need to even set proxies, it would transparently block URLS like that and show an error page. I am doing a more complex version where some devices are https ssl intercepted to look for container virtualized bugs data marshaling network cards, "I found them however I needed Snort AppID to track them down in the end" and some devices are set to transparent mode where it looks at only the get request and nothing else.
It is a very amazing set of software. I am so in love with this package and the way it works. I report stuff all the time with it, track items its great. It is also protected behind a firewall set of rules so it's great for pfSense.
My SG-2100 will continue to use it until the appliance dies. The final version of pfSense after 4 years of config changes, code, bugs, works perfectly, I am not going to give up on it. To everyone that worked on it at Netgate and all the community members to make it finally work, Thank you. The device works how it should for what I need, sure it's super secure maybe to secure but that was what was needed for cybersecurity, to stop the ransomware all the issues stopped with something like this. This was the firewall that helped END it.
-
Hey. Question for you guys:
When squid is attempting to redirect, I get:
<p>The following error was encountered while trying to retrieve the URL: <a href="https://http/">https://http/</a></p>
on an HTML response.
acl { default { pass !badstuff destinations all redirect http://wpad.jvj.com/denied?url=Access+Denied&a=%a&n=%n&i=%i&s=%s&t=%t&u=%u log block.log } }the redirect is behaving as a host, not a URL. what is the proper syntax? As ChatGPT says this is correct. But, cannot be.
-
Hey! Another one!
When I try to go to the squid 'status' on the pfsense GUI, I get a 403 error:
HTTP/1.1 403 Forbidden Server: squid/6.6 Mime-Version: 1.0 Date: Wed, 22 May 2024 10:12:57 GMT Content-Type: text/html;charset=utf-8 Content-Length: 3800 X-Squid-Error: ERR_ACCESS_DENIED 0 Vary: Accept-Language Content-Language: en Cache-Status: squid.jvj28.com Via: 1.1 squid.jvj.com (squid/6.6), 1.1 squid.jvj.com (squid/6.6) Cache-Status: squid.jvj28.com;detail=no-cache Connection: closeI really have looked for every ACL that I could think of. Not finding the issue.
-
@jdb67 there is an open Redmine ticket to fix the status page, Squid has a new url schema to access the status page the GUI code still needs to be updated.
-
@JonathanLee Sweet. Thanks
-
@jdb67 You might also try to email the Squid users support email to get Squid help they are very helpful sometimes the original code writers chime in and help users.
squid-users@lists.squid-cache.org
FYI: You will have to register your email and wait for approval before you can send out a email to everyone on this however.