Access Modem GUI Behind Firewall
-
@Globaltrader312 what is inside your “lan subnets” alias? You have that listed for every rule as source, thus everything on every subnet is approved to go anywhere? Maybe start compartmentalization of the source acls with specific subnets, again they are fail overs, you need a different port for the modem is what I would do and or make a lan side nat with one say access it as 8080 and nat it to 80 with that host ip I did that with syslogs. Thus firewall would attempt to access it on 8080 and it would nat it over to the modem’s IP address and forward it with port forwarding to port 80.
-
@JonathanLee in the Lan subnet all devices macs iPhones iPads and other devices are in the network. nothing more i simply followed the Netgate instructions and configured it that way.
-
@Globaltrader312 try for me, make a lan side nat that has port 8080 as destination and that modem’s ip and set it port forward to 80 with the modem ip as destination. After attempt to access that address in your url with ipaddessofmodem:8080 just port forward it with some random port that the firewall knows where to send it.
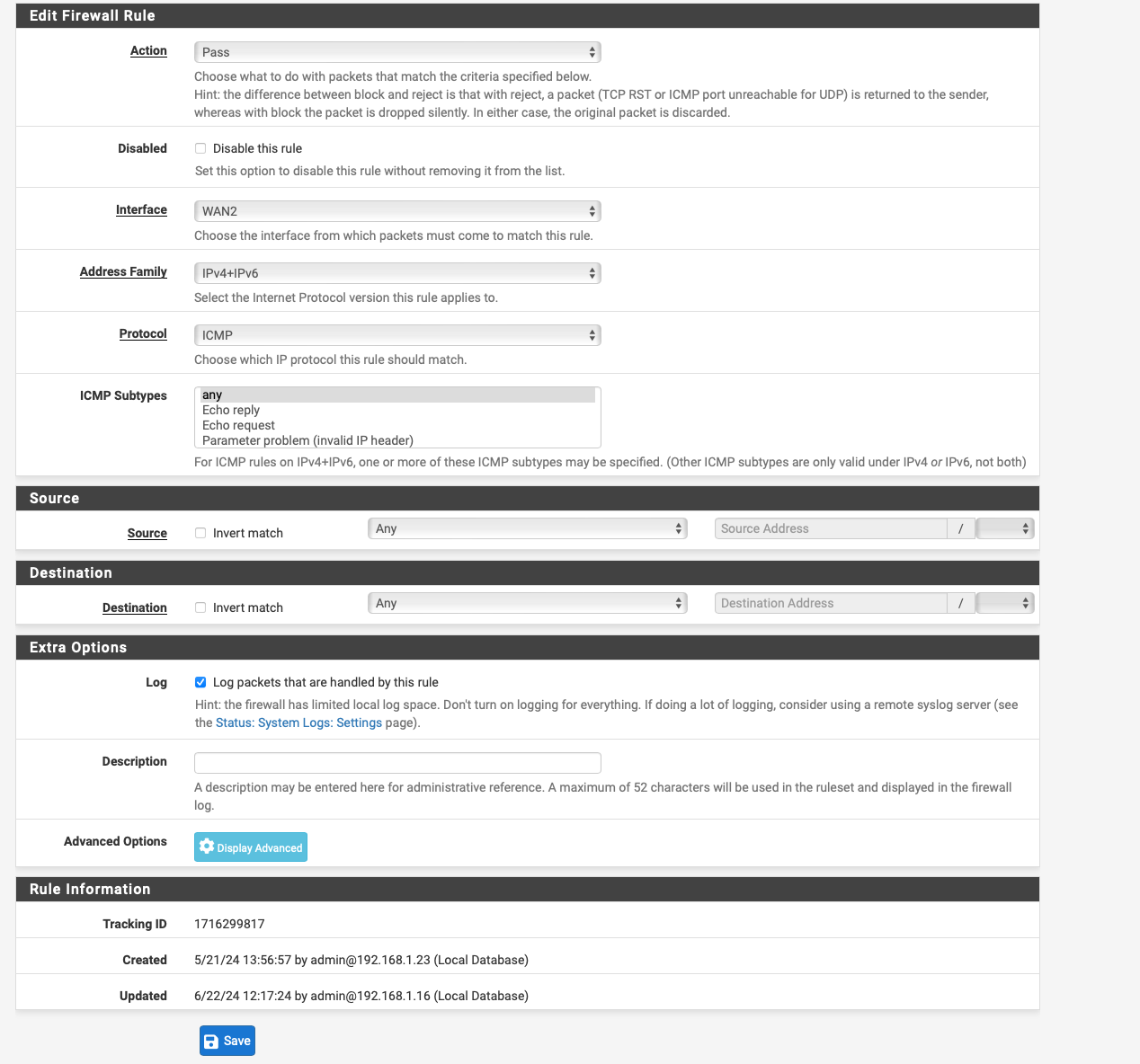
So source “any” destination “192.168.5.1:8080” port forward it to “192.168.5.1:80” after see if you have ACL bytes
Make sure it uses the correct gateway. that way it can get around your any any lockout rule and know where to go. I had to do this with a non standard syslog port from an AP so that the firewall could see the logs.
I hate to ask this you are sure you use in the url 192.168.5.1 and only use port 80 there is no lock showing when you access that gui from a direct laptop connection? What a puzzle, I love this stuff I did a HE ipv6 set up a couple weeks ago and it was working perfectly until my wife said set it back the way it was because she didn’t like that I wasn’t 100 percent sure of it.
-
so I looked again
the ports 80 and 443 are used, I have changed them to 8080 in the modem and to 444
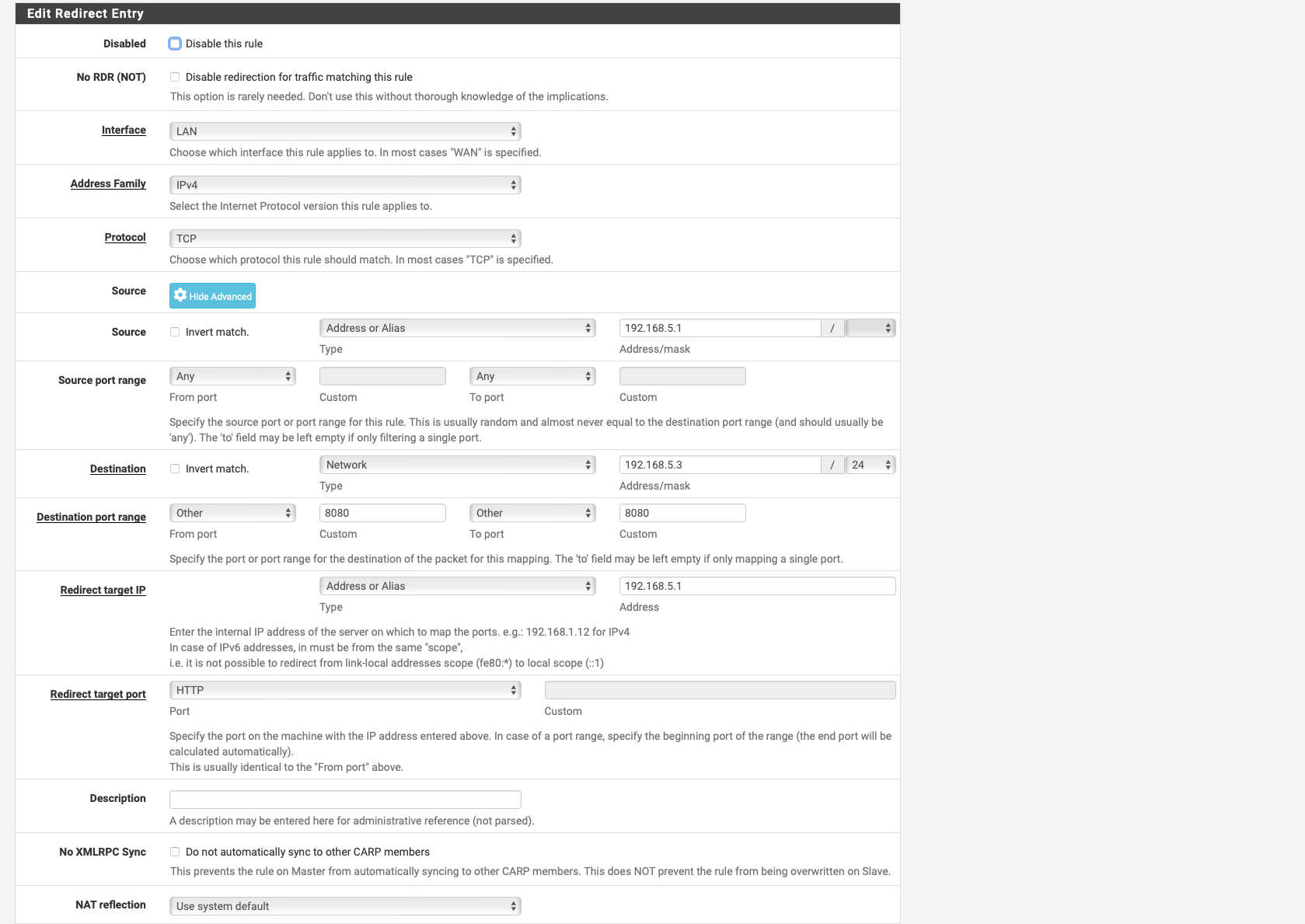
I generally know how to make a port forward, but unfortunately I am not sure about this for Lan, if I want to set a port forward there I have the following but no field for port specification.
-
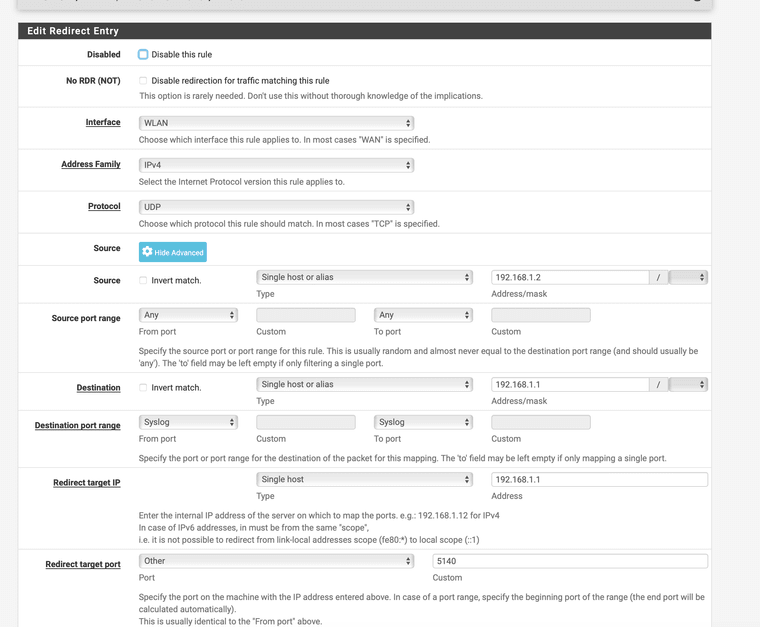
Something like this it is it is located under "Firewall" "NAT"
Except use tcp/udpInterface set to LAN, Source "any" first to try and set Destination to 192.168.5.1 and port 8080
After redirect target port set to HTTP and redirect target IP ad 192.168.5.1
Try this first to see if you can access it and or get logs. forget about 443 right now
-
OHHHH YEAH I FORGOT
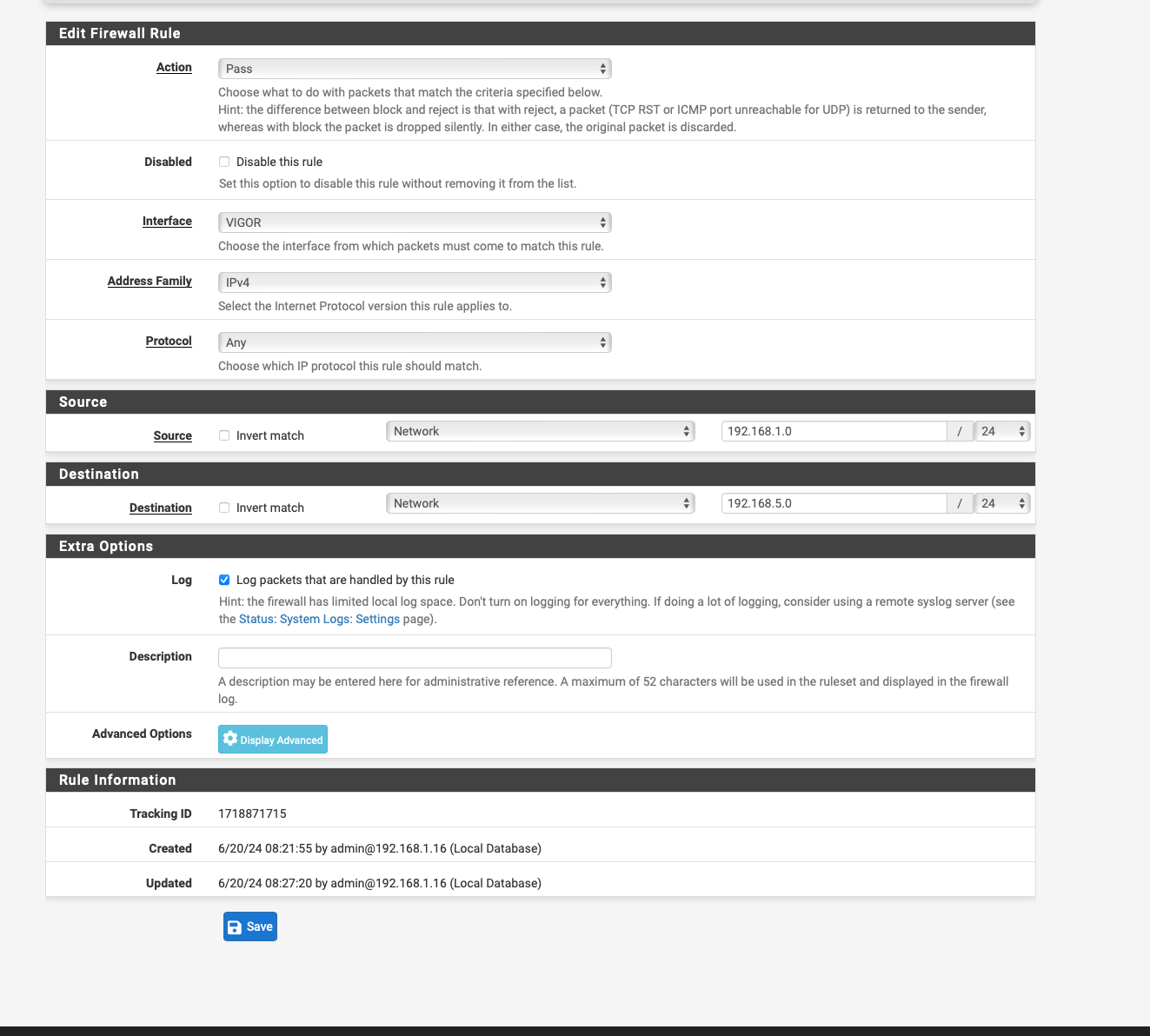
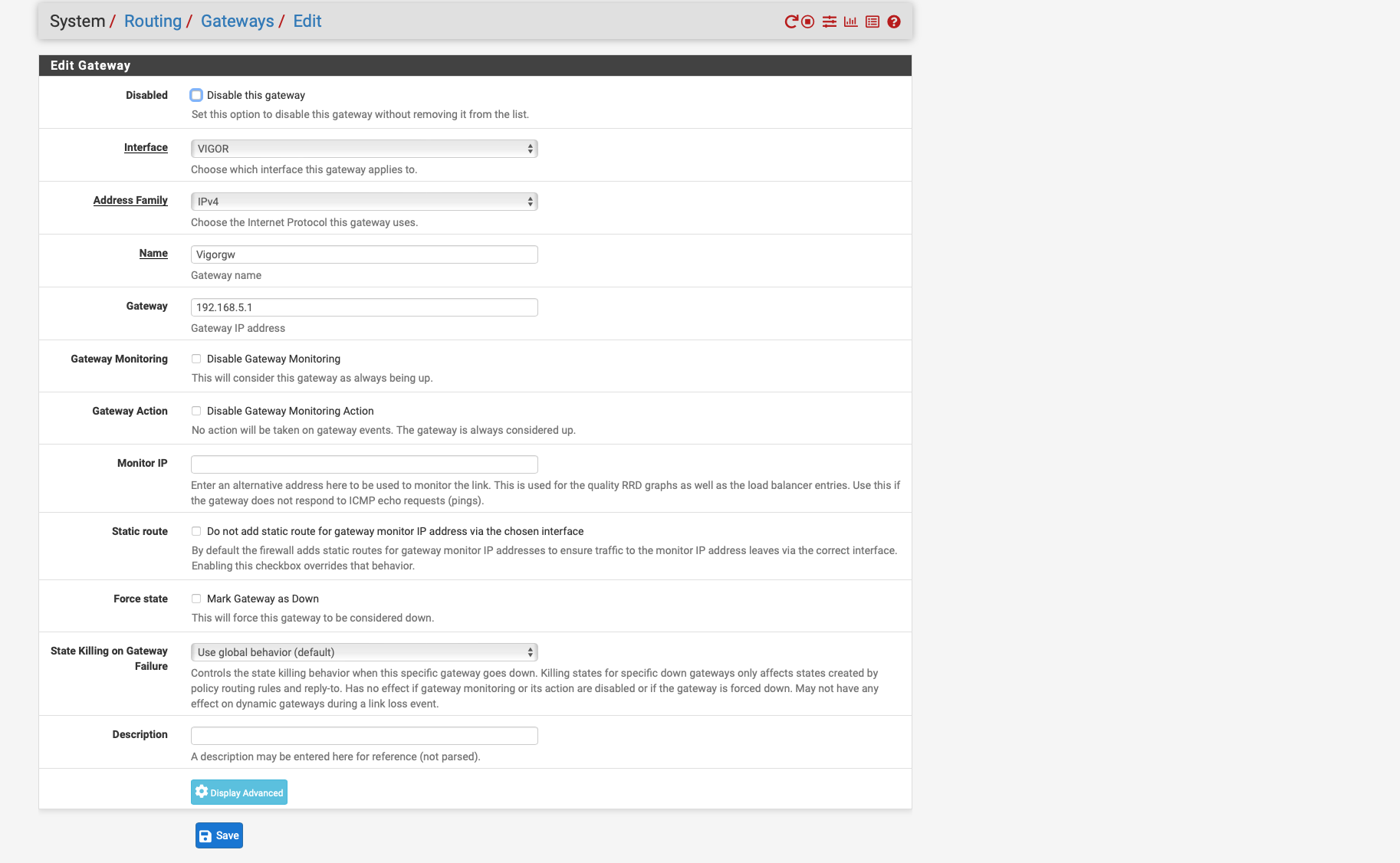
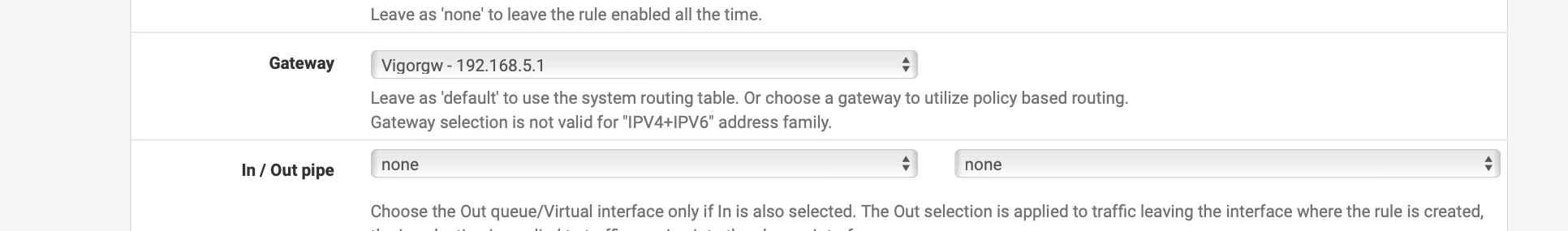
!!! Just Try a floating rule that can use all the interfaces and set the gateway to the one where the modem resides that would work also.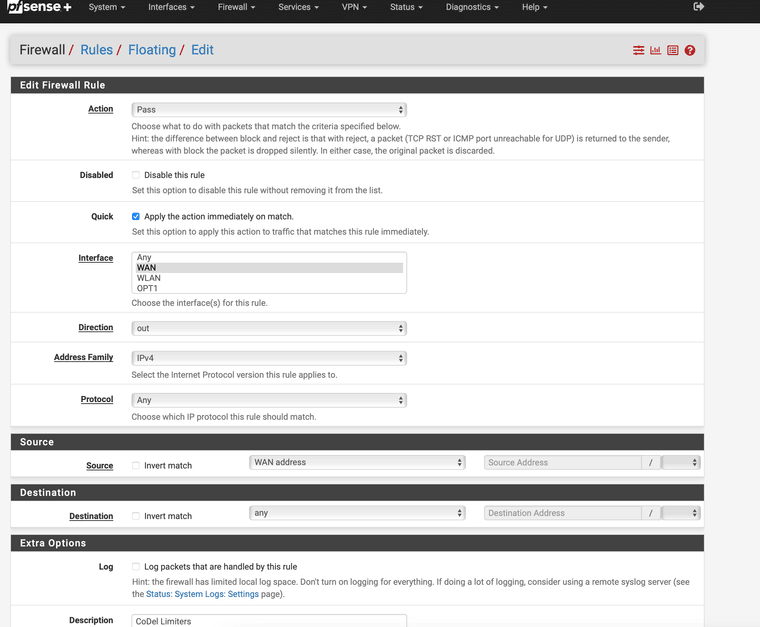
Gateway is under extra options. I think this would work better Don't use my settings set your destination to that modem and use the gateway it needs
-
-
@Globaltrader312 does the corresponding auto generated rule show traffic?
Please do me a favor and create a floating rule if there is no traffic, I feel like it is auto hitting the first rule in the ACL and that is directing it to the wrong gateway or the other WAN, thus it can't access it and drops the packets please turn on logging on the other rules and we can see in the logs where it hits also.
-
@JonathanLee said in Access Modem GUI Behind Firewall:
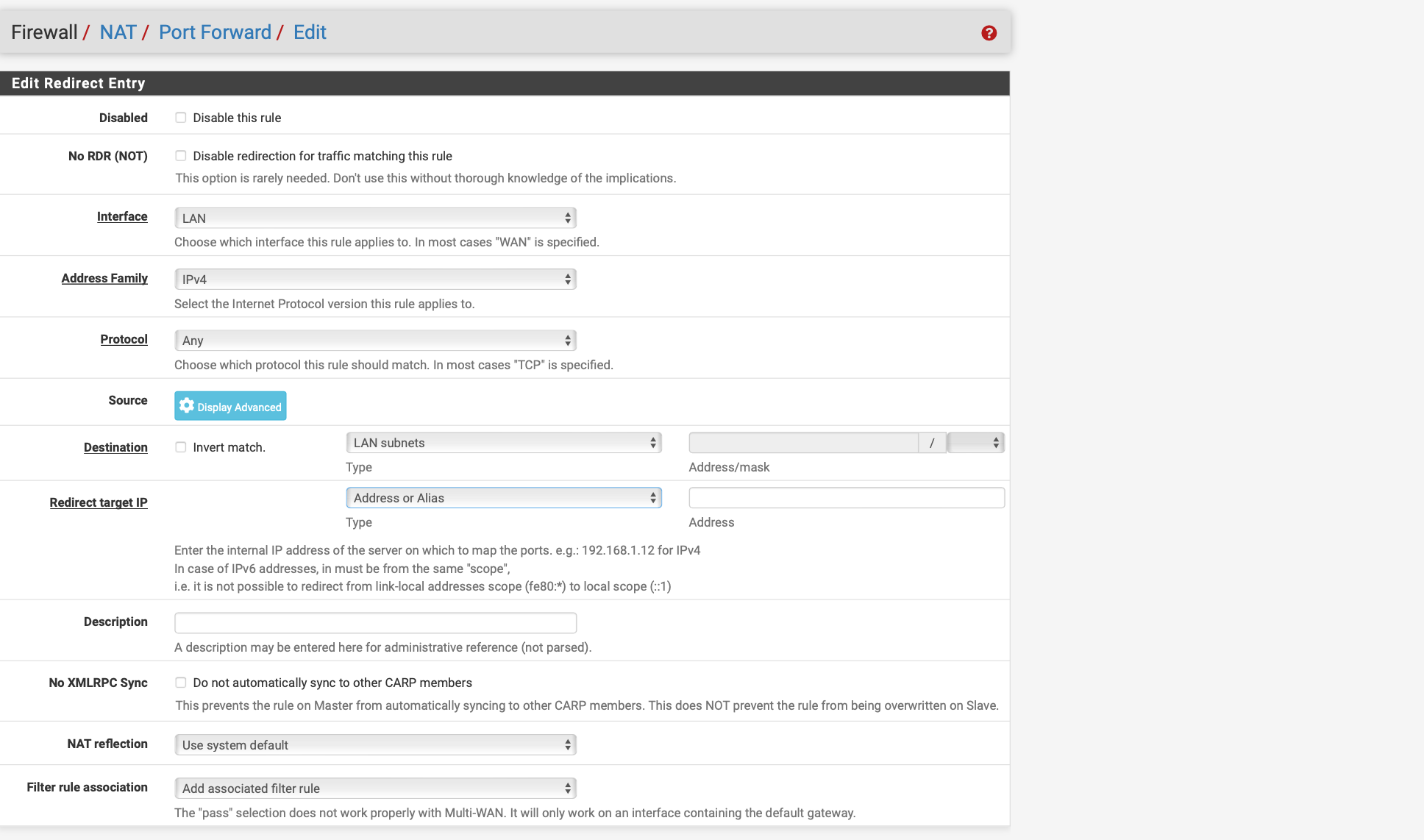
Please do me a favor and create a floating rule if there is no traffic, I feel like it is auto hitting the first rule in the ACL and that is directing it to the wrong gateway or the other WAN, thus it can't access it and drops the packets please turn on logging on the other rules and we can see in the logs where it hits also.so i have created a floating rule as seen on the screenshots unfortunately it does not help
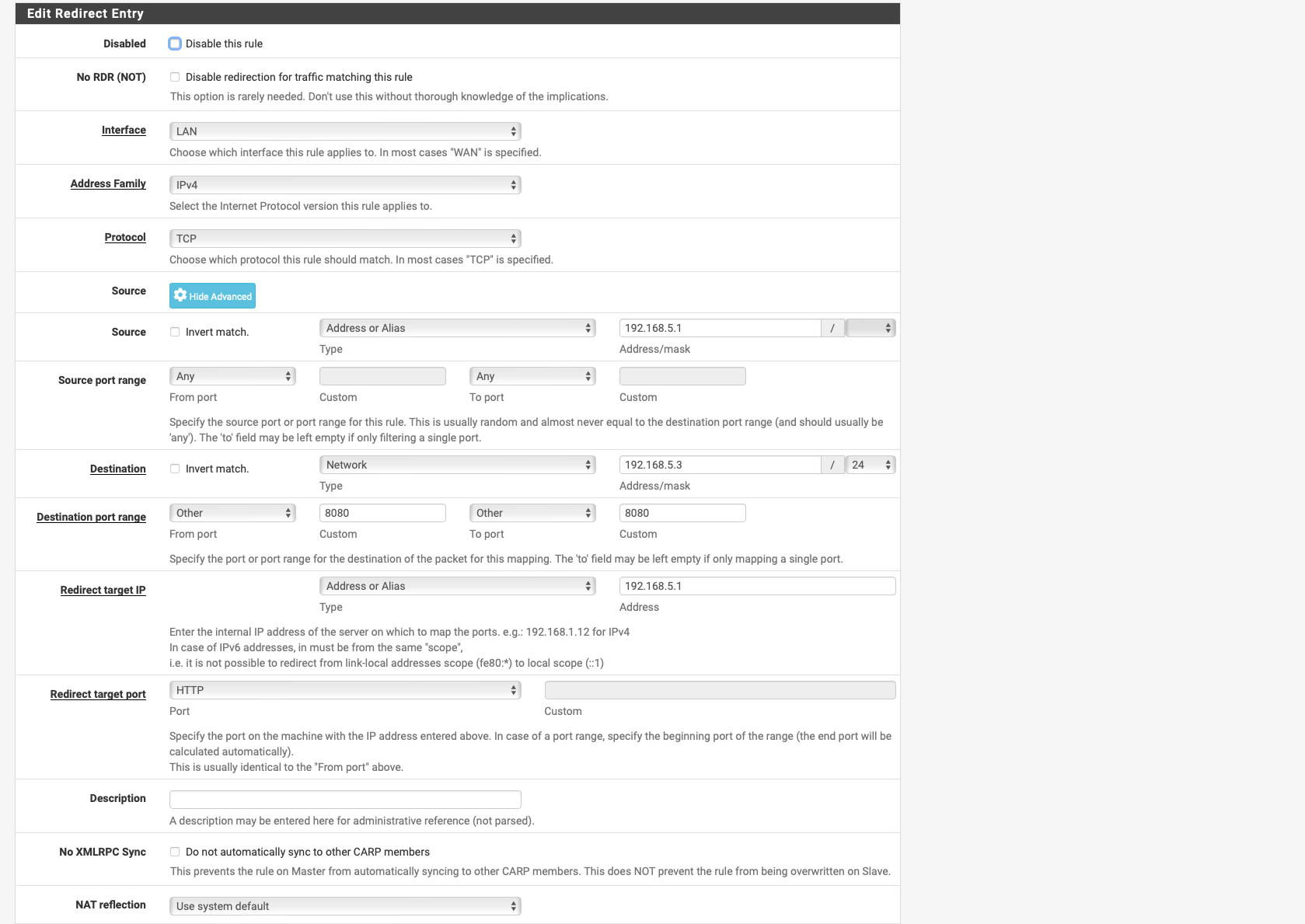
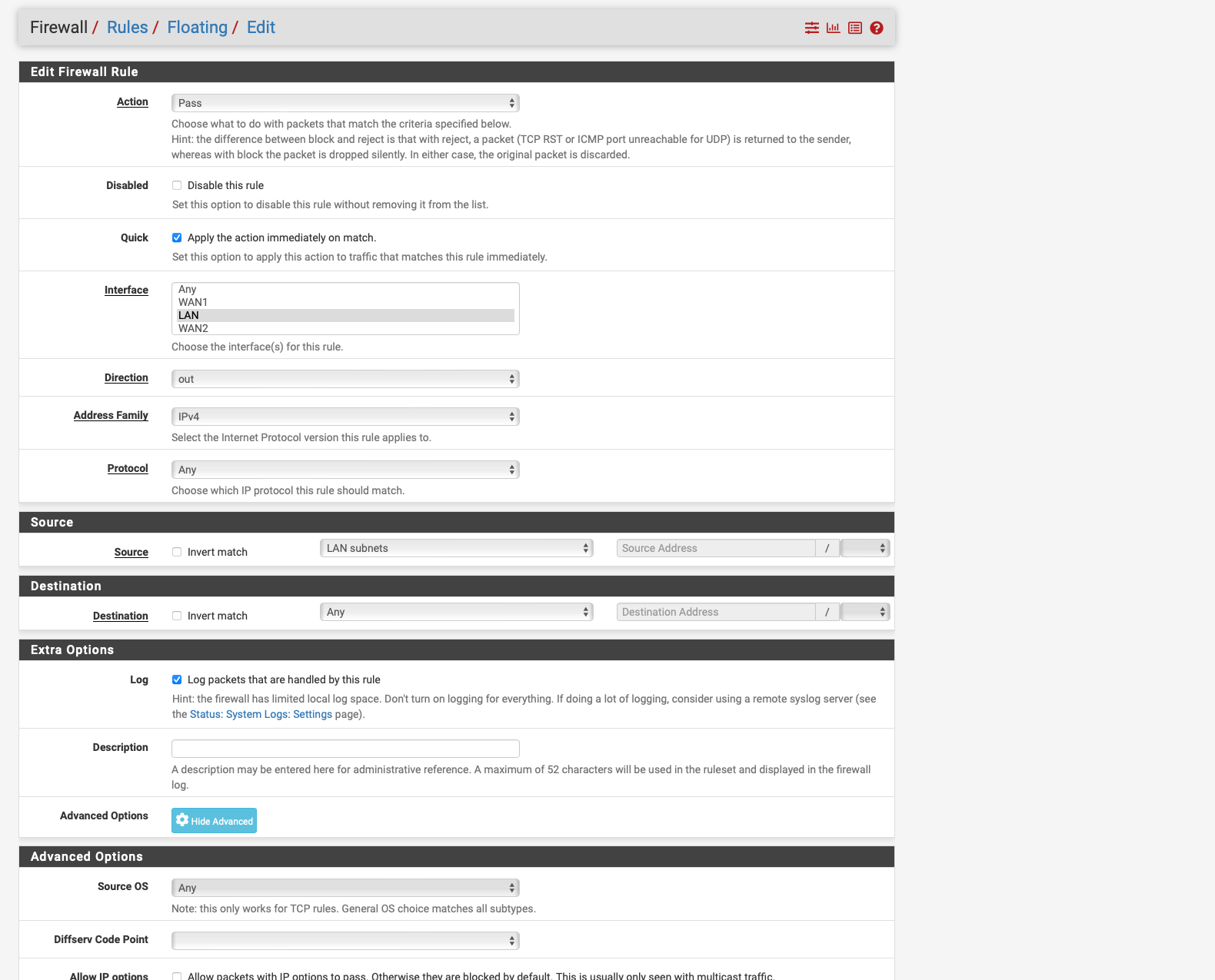
-
Floating Rule destination should be 192.168.5.1 and under advanced extra set this to the gateway that the modem resides on. Please delete the other NAT rule after let's see if it shows in logs. Does anything show in logs?
Please enable logging on all the lan interfaces and attempt to access it again and look after under "status" "system logs" click on submenu "firewall"
-
@Globaltrader312 Not sure if it's solved or not.
What bothers me is the fact that you get no ARP entry for the Vigor. If I delete the ARP entry for my modem and run a ping to the modem, the MAC (of course) shows up again. That seems not to be the case for you.
I would try to ping the Vigor router from the VIGOR interface, that should work in any case since it's on the same link, no routing or anything needed (I know you did a ping with default settings).
Diagnostics > Ping
Hostname 192.168.5.1
IP Protocol IPv4
Source address VIGORIf that works check please again the ARP table for the MAC of your modem (14:49:BC:4C:84:00 according to you screenshot from the modem gui).
Addition: The Vigor als got a ARP table, Chapter IV > IV-1-4 ARP Table in the user manual. The MAC of bge1 has to appear there.
-
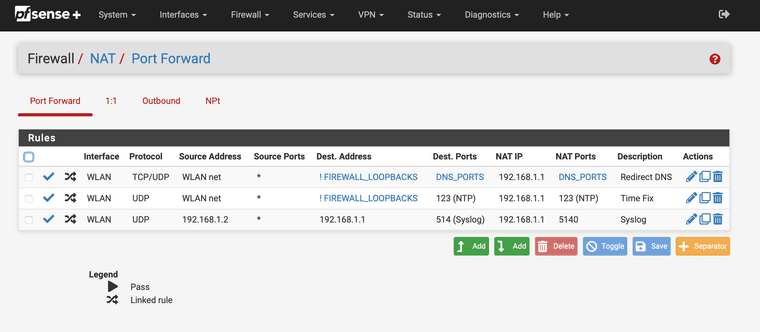
@JonathanLee so i have deleted everything except the floating rule.
see screenshot
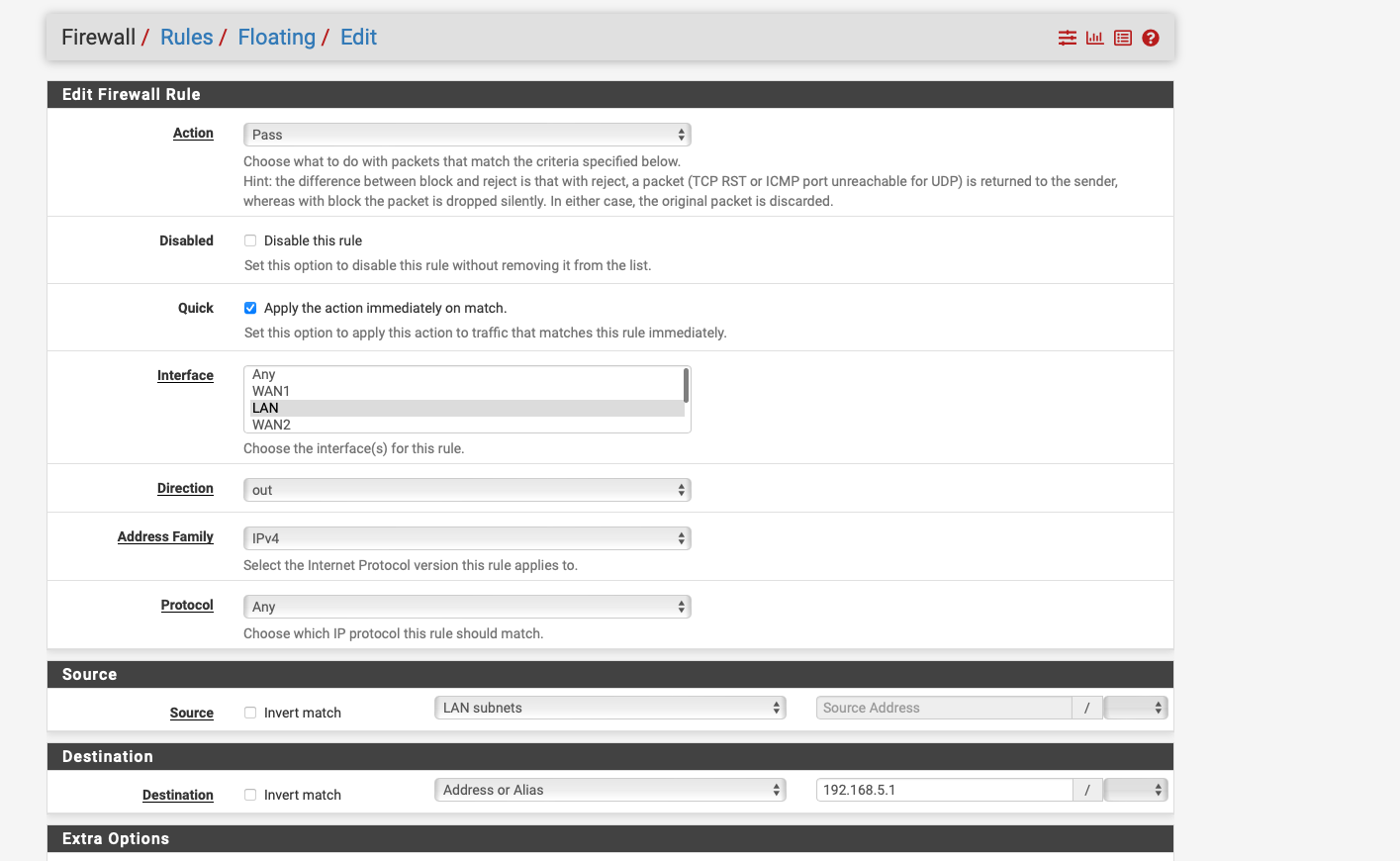
-
@Globaltrader312 So when I ping the vigor interface, the Vigor Mac is displayed.
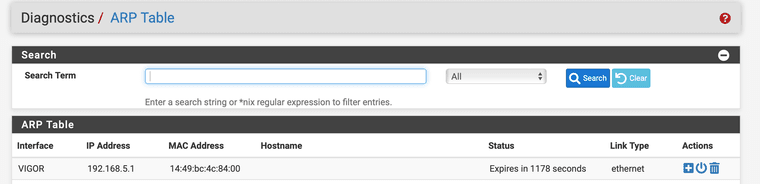
-
@Globaltrader312 Well, that part looks good. Don't know about the floating firewall rule. I didn't add any firewall rule for the modem access. Have you tried disabling the rule for the moment?
-
@Globaltrader312 said in Access Modem GUI Behind Firewall:
I have now selected ppoe as Getway WAN2 and moved it to the top
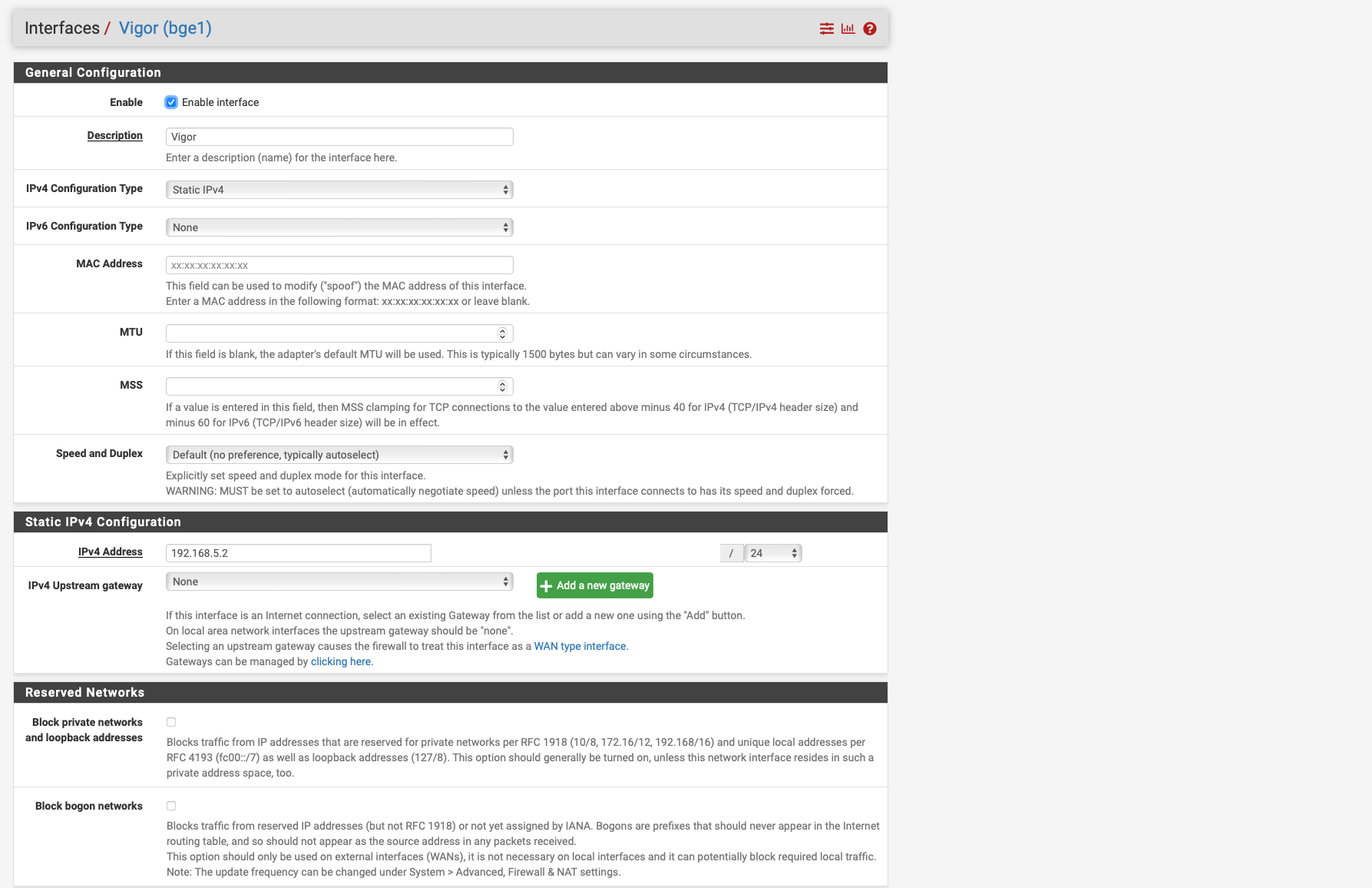
But that is not the case, your not going out the pppoe interface, to talk to the modems actual IP, you would go out just the interfaces IP ie the 192.168.5.2 address.. Not the pppoe interface which rides on top of the physical interface.
-
@johnpoz said in Access Modem GUI Behind Firewall:
But that is not the case, your not going out the pppoe interface, to talk to the modems actual IP, you would go out just the interfaces IP ie the 192.168.5.2 address.. Not the pppoe interface which rides on top of the physical interface.
that's clear to me i just don't know how to change it i followed the instructions from netgate exactly and configured everything the same way then the instructions seem to be useless
-
@Globaltrader312 DON'T Set the gateway on the rule so pfsense can use its normal routing.. It is attached to the 192.168.5 network - it knows how to get there - you can ping it right.. So why would you think you should force it out the pppoe connection.
The rules say nothing of the sort.
If your doing auto nat, pfsense would change your lan connection to the 192.186.5.2 address when talking to the vigor .1 address. Unless you have modified your outbound nat this should be clicky clicky.
You have multiple wan interfaces, and are doing policy routing.. You have to have rules that allow the traffic you want without policy routing.
Your taking instructions for a simple setup, one pppoe connection which normally people wouldn't policy route with and trying to apply them to your not common setup..
-
@johnpoz said in Access Modem GUI Behind Firewall:
DON'T Set the gateway on the rule so pfsense can use its normal routing.. It is attached to the 192.168.5 network - it knows how to get there - you can ping it right.. So why would you think you should force it out the pppoe connection.
The rules say nothing of the sort.
If your doing auto nat, pfsense would change your lan connection to the 192.186.5.2 address when talking to the vigor .1 address. Unless you have modified your outbound nat this should be clicky clicky.
You have multiple wan interfaces, and are doing policy routing.. You have to have rules that allow the traffic you want without policy routing.
Your taking instructions for a simple setup, one pppoe connection which normally people wouldn't policy route with and trying to apply them to your not common setup..
DON'T Set the gateway on the rule so pfsense can use its normal routing... It is attached to the 192.168.5 network - it knows how to get there - you can ping it right... So why would you think you should force it out the pppoe connection.
i don't think anything i just tried something on the advice of the other user.
The rules say nothing of the sort. ok
If your doing auto nat, pfsense would change your lan connection to the 192.186.5.2 address when talking to the vigor .1 address. Unless you have modified your outbound nat this should be clicky clicky. i have set the outboundd nat ruele as in the instructions
You have multiple wan interfaces, and are doing policy routing... You have to have rules that allow the traffic you want without policy routing ok
which ones would that be and how do i set them on my edge router i just had one nat rule and that was enough for that ?
Your taking instructions for a simple setup, one pppoe connection which normally people wouldn't policy route with and trying to apply them to your not common setup... I wasn't sure of anything so I asked if it was the Multi WAN Wan failvoer setup
-
I lost a bit the overview of what got done and what not.
If you have the patience I'd start over. For me it worked well by only creating the modem interface and the NAT Outgoing rule, nothing else needed. Even as I added a second WAN-over-USB-tethering interface and created a gateway group with it (WAN tier 1 and WAN-tethering as tier 2).
-
@patient0 I have now removed the gateway with 192.168.5.1 from the firewall rules as well.
yes i am also a bit confused because in the beginning i only had WAN inteferaces with multi WAN and failover setup including iPV4 gateway and V6 gateway and a gateway group with tier 1 2 3 and set this in the LAN any rule
then I worked as described in the instructions.
again it does not workI will start again from the beginning