[SOLVED] Domain Override (DNS Resolver) Not Working
-
Hi,
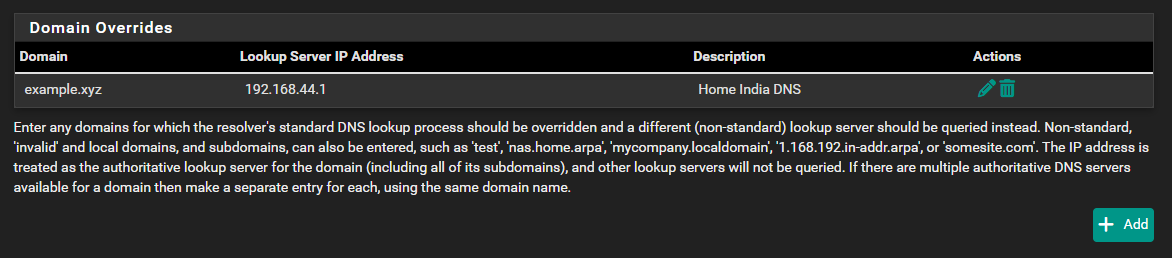
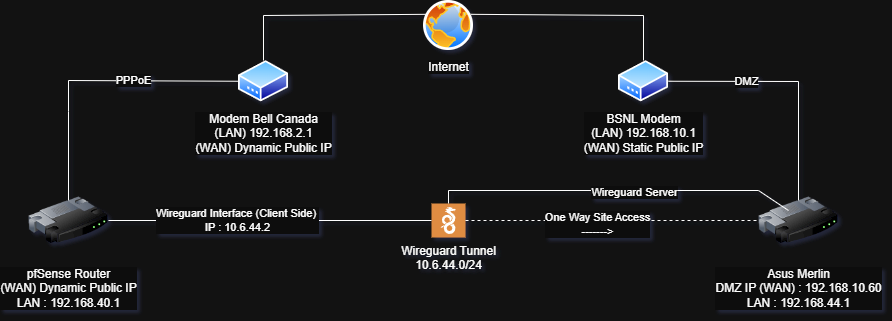
I am trying to get Domain Override working for example.xyz (192.168.44.1) in pfsense for my other Home India connected over Wireguard Tunnel.
pfSense is able to reach the dns server over the wireguard tunnel.
[24.11-RELEASE][root@firewall.example.net]/root: dig @192.168.44.1 rm4.example.xyz ; <<>> DiG 9.20.2 <<>> @192.168.44.1 rm4.example.xyz ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20219 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;rm4.example.xyz. IN A ;; ANSWER SECTION: rm4.example.xyz. 0 IN A 192.168.44.16 ;; Query time: 265 msec ;; SERVER: 192.168.44.1#53(192.168.44.1) (UDP) ;; WHEN: Wed Feb 12 00:36:24 EST 2025 ;; MSG SIZE rcvd: 59pfSense DNS Override Not Working
[24.11-RELEASE][root@firewall.example.net]/root: dig @192.168.40.1 rm4.example.xyz ; <<>> DiG 9.20.2 <<>> @192.168.40.1 rm4.example.xyz ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 30754 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1352 ;; QUESTION SECTION: ;rm4.example.xyz. IN A ;; Query time: 0 msec ;; SERVER: 192.168.40.1#53(192.168.40.1) (UDP) ;; WHEN: Wed Feb 12 00:37:31 EST 2025 ;; MSG SIZE rcvd: 43 -
@manjotsc said in Domain Override (DNS Resolver) Not Working:
pfSense is able to reach the dns server over the wireguard tunnel.
[24.11-RELEASE][root@firewall.example.net]/root: dig @192.168.44.1 rm4.example.xyz
; <<>> DiG 9.20.2 <<>> @192.168.44.1 rm4.example.xyz
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20219
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;rm4.example.xyz. IN A;; ANSWER SECTION:
rm4.example.xyz. 0 IN A 192.168.44.16;; Query time: 265 msec
;; SERVER: 192.168.44.1#53(192.168.44.1) (UDP)
;; WHEN: Wed Feb 12 00:36:24 EST 2025
;; MSG SIZE rcvd: 59pfSense DNS Override Not Working
[24.11-RELEASE][root@firewall.example.net]/root: dig @192.168.40.1 rm4.example.xyz
; <<>> DiG 9.20.2 <<>> @192.168.40.1 rm4.example.xyz
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 30754
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1352
;; QUESTION SECTION:
;rm4.example.xyz. IN A;; Query time: 0 msec
;; SERVER: 192.168.40.1#53(192.168.40.1) (UDP)
;; WHEN: Wed Feb 12 00:37:31 EST 2025
;; MSG SIZE rcvd: 43Not clear, what this comparison should proof. Both are requesting the same server, which is obviously on the remote site, one succeed, the other one fails. Nice.
From where did you do the lookups?To verify if a domain override is working on pfSense, I'd rather sent the request to pfSense instead directly to the remote server.
-
@viragomann pfSense (DNS Resolver) doesn't want to resolve, but sending the request to remote DNS, works.
Dig to Remote DNS from pfSense works. (192.168.44.1)
Dig to pfSense (Domain Override) doesn't work. (192.168.40.1)
-
I was half way writing a suggestion about how to test your situation, but then I found out I was wrong.
I have set up a Domain Overrides like you where the server IP pointed to the domain name server of that domain. It is a public accessible domain name server for that domain, my domain, and the server runs on my own hardware - I use "bind" to handle all own domain names.
Sme some PC in my network I made a nslookup request like :
nslookup www.mydoamin.tldWhere www.mydoamin.tld was the domain (host) name I was overriding.
I've set up a packet capture on the WAN (my one and only outgoing interface) and looked for the DNS IP, port 53, UDP - and executed my nslookup.
Packets were captured.
And then I understood that my test was wrong - it was no proof at all that domain overrding works with this setup.So, for what ir's worth :
Your first test : executing dig from "192.168.40.1" (right ?), tell dig to use the DNS @192.168.44.1 = the DNS on the other side of your tunnel ( ! ) - which proofs the tunnel works, and that the DNS on the other side accepted your request, and even send an answer back.
As contacting the other side = 192.168.44.1 over the 'plain' internet wouldn't work.
So, imho, your initial test proofs the VNP (tunnel) and DNS works.The next test, you address your dig to the local pfSense @192.168.40.1 resolver and no answer ...
You could packet capture 'on the other side' and check if the (this) DNS request arrived.
And or packet capture on 'your' side and check where the request goes ... the VPN tunnel ? The WAN ? The latter would fail of course.
How do you have set the revolver's outgoing interfaces ? -
Thanks,
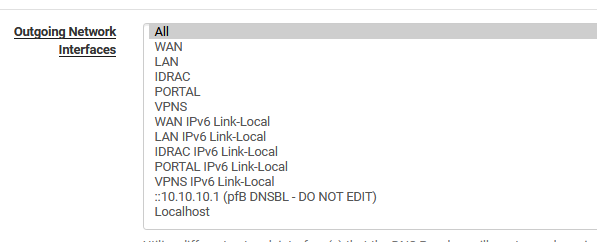
I just got it working, need to get around DNS Rebound and need to set Outgoing Network Interfaces to ALL, I had it set to WAN
Is there a reason why it needs to be to ALL?
https://forum.netgate.com/post/1094958
DNS Resolver under Custom Options
server: private-domain: "example.xyz"[24.11-RELEASE][root@firewall.example.net]/root: dig @192.168.40.1 rm4.example.xyz ; <<>> DiG 9.20.2 <<>> @192.168.40.1 rm4.example.xyz ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 2463 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1352 ;; QUESTION SECTION: ;rm4.example.xyz. IN A ;; ANSWER SECTION: rm4.example.xyz. 0 IN A 192.168.44.16 ;; Query time: 266 msec ;; SERVER: 192.168.40.1#53(192.168.40.1) (UDP) ;; WHEN: Wed Feb 12 07:52:08 EST 2025 ;; MSG SIZE rcvd: 5 -
@manjotsc said in [SOLVED] Domain Override (DNS Resolver) Not Working:
Is there a reason why it needs to be to ALL?
If I’m following pre-coffee, it’s the “connected over Wireguard Tunnel” part, where otherwise you’ve told unbound not to use the tunnel.
-
@SteveITS make sense now, I been going in circle for couple hours, didn't even think about that.
Thanks,
-
@manjotsc said in Domain Override (DNS Resolver) Not Working:
need to set Outgoing Network Interfaces to ALL, I had it set to WAN
Oh ... cool ... tel unbound to use (only) WAN as an outgoing interface, while it should have been to using the Wireguard tunnel (which also goes over WAN) to do its job.
edit : I'm actually echoing what @SteveITS said
@manjotsc said in Domain Override (DNS Resolver) Not Working:
Is there a reason why it needs to be to ALL?
You've already got my point : because someone decides that that settings is perfect for us ^^
As the fireguard connection is a second type of WAN interface : a network that goes "somewhere" outside the local LANs, and not reachable by classic WAN, you have to inform unbound about it.
Set it to(it was set by default on All - which proofs Netgate's default settings are perfect - who are we to make them any better
 )
)
but yeah, WAN is fine, but check-select also your wireguard interface.
I don't quiet understand what danger or harm there is if it also uses my local LAN connections (no DNS devices will reply from there ) so I don't bother : All is fine for me.
Their might be cases where All is not good - I just didn't discover them yet.@manjotsc said in Domain Override (DNS Resolver) Not Working:
server:
private-domain: "example.xyz"There is another part worth look at - same file :
# Domain overrides include: /var/unbound/domainoverrides.confLook at what "/var/unbound/domainoverrides.conf" contains.