Static Ip choosing the mobile client virtual pool not user assigned static ip
-
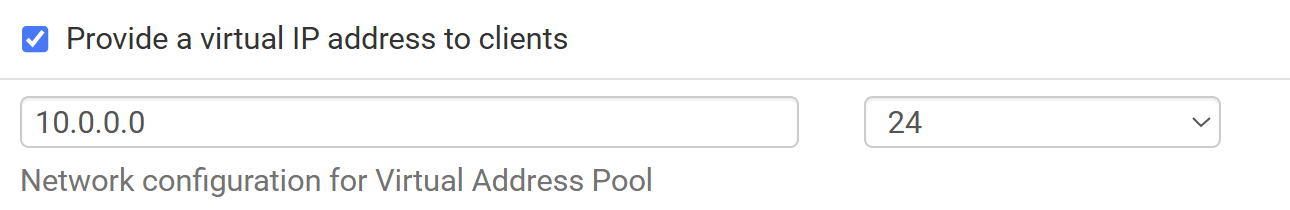
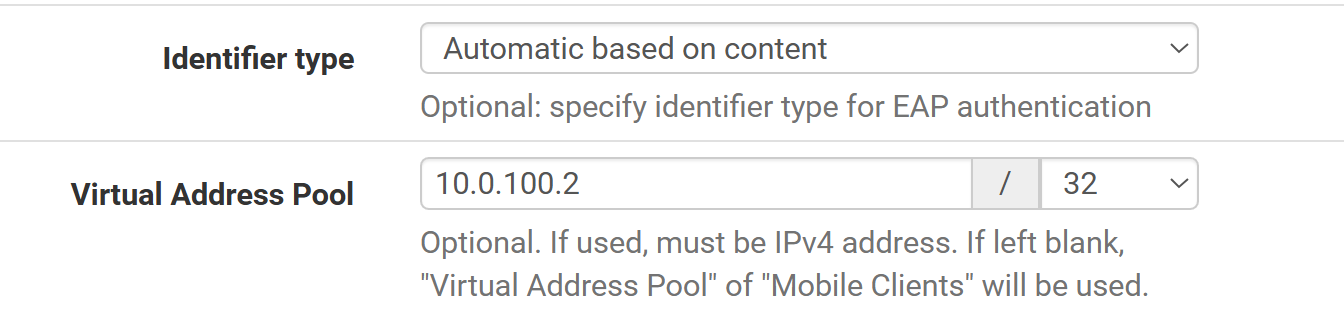
I want to setup each user to have a static ip for software development reasons where I want them to get the same ip address every time. The mobile client setups virtual pool range always gives out the ip addresses rather than the per user statically assigned. So the first picture Virtual address pool wins over the second picture which is per user.
Mobile Client
beats
Preshared Key of user s@s.com
I made sure the VPN->IPsec->Pre-Shared Keys->Edit
virtual address pool does not conflict with the virtual ip address to clients in the first picture.It always assigns my client 10.0.0.1 when I want it to use the pre-shared-key users 10.0.100.2. I followed the directions in not making it blank but it doesn't win.
connections {
bypass {
remote_addrs = 127.0.0.1
children {
bypasslan {
local_ts = 192.168.0.0/22
remote_ts = 192.168.0.0/22
mode = pass
start_action = trap
}
}
}
con-mobile : con-mobile-defaults {
# Stub to load con-mobile-defaults
}
con-mobile-userpool-1 : con-mobile-defaults {
remote {
id = "s@s.com"
eap_id = %any
}
pools = mobile-userpool-1
}
con-mobile-userpool-2 : con-mobile-defaults {
remote {
id = "d@d.com"
eap_id = %any
}
pools = mobile-userpool-2
}
}
con-mobile-defaults {
fragmentation = yes
unique = replace
version = 2
proposals = aes256gcm128-aesxcbc-modp1024,aes128gcm128-sha256-modp1024,aes256-sha256-modp1024
dpd_delay = 10s
rekey_time = 77760s
reauth_time = 0s
over_time = 8640s
rand_time = 8640s
encap = yes
mobike = no
local_addrs = 172.124.3.133
remote_addrs = 0.0.0.0/0,::/0
pools = mobile-pool-v4
send_cert = always
local {
id = 172.124.3.133
auth = pubkey
cert {
file = /var/etc/ipsec/x509/cert-1.crt
}
}
remote {
id = %any
eap_id = %any
auth = eap-mschapv2
}
children {
con-mobile {
# P2 (reqid 1): IPSec Mobile Phase 2
mode = tunnel
policies = yes
life_time = 3600s
rekey_time = 3240s
rand_time = 360s
start_action = none
local_ts = 0.0.0.0/0
esp_proposals = aes256gcm128-modp2048,aes256gcm96-modp2048,aes256gcm64-modp2048,aes128gcm128-modp2048,aes128gcm96-modp2048,aes128gcm64-modp2048,aes256-sha1-modp2048,aes256-sha256-modp2048,aes256-sha384-modp2048,aes256-sha512-modp2048,aes256-aesxcbc-modp2048,aes192-sha1-modp2048,aes192-sha256-modp2048,aes192-sha384-modp2048,aes192-sha512-modp2048,aes192-aesxcbc-modp2048,aes128-sha1-modp2048,aes128-sha256-modp2048,aes128-sha384-modp2048,aes128-sha512-modp2048,aes128-aesxcbc-modp2048,chacha20poly1305-modp2048
close_action = start
dpd_action = restart
}
}
}
pools {
mobile-pool-v4 : mobile-pool {
addrs = 10.0.0.0/24
}
mobile-userpool-1 : mobile-pool {
addrs = 10.0.100.2/32
}
mobile-userpool-2 : mobile-pool {
addrs = 10.0.4.2/32
}
}
mobile-pool {
# Mobile pool settings template
}
secrets {
private-0 {
file = /var/etc/ipsec/private/cert-1.key
}
eap-1 {
secret = [omitted for security]
id-0 = s@s.com [changed for security]
}
eap-2 {
secret = [omitted for security]
id-0 = d@d.com [changed for security]
}
}