Possibility of capturing ssl-keys using tcpdump in the pfsense shell
-
Hello,
Let me know if this in the wrong sub-topic.
Per the following documentation documentation I would like to know if it is possible to capture TLS keys using the SSLKEYLOGFILE environment variable.
I got as far as capturing keys this way using curl, however, this does not seem to work for tcpdump (the capture utility default to pfsense).
How could this be achieved?
Alternative approaches / suggestions are very much welcome
-
@b3rt what data are you trying to decrypt exactly - from what to what, is pfsense one of the endpoints in the traffic flow? Or just the man in the middle of some connection?
-
The pfsense would be acting as a MiTM, as the connection originates from LAN and passes the pfsense to the internet.
-
@b3rt you would need to be on one of the end points to get the key.. If you could get the key on a router in the middle then ssl/tls would be completely utterly pointless.
-
Right, that makes sense when you think about it.
I should probably close this thread 🫠 -
@b3rt you could be a MITM, but you would have to run it through a proxy, and hand the client a cert he trusts that is behind pfsense thinking its the cert for where its trying to go.
Say you had some traffic you needed to decrypt to see what the client was doing if they are going to https://somewhere.domain.tld - you could run through the proxy and send it a cert you signed for somewhere.domain.tld, since you created the cert you would have the keys needed to decrypt the traffic.. Then the proxy sends the data on using the cert from the actual somewhere.domain.tld
This is fairly easy to do if you control the PC making the connection, it gets more difficult with say some IOT device or something where you can not get the device to trust the cert you created as valid cert for where it is trying to go.
This is how enterprises do it.. Where the software creates certs on the fly for any site the client is going - and the client trusts this cert. You can do it with squid, but it's a bit more involved then click click. And again you have to get the client to trust your cert your handing them so you can do the mitm.
-
Interesting you mention IOT devices because that was the intended goal. Going with the squid suggestion, using SSL bumping on squid proxy is possible on pfsense, but it's
probablyimpossible to get the IoT devices to trust your certificate.I'll look into getting this to work for at least my own PC, just to get used to it. Thanks for the suggestions / explanations on the how and why this would be (im)possible.
-
@b3rt yeah with a phone or something like that where you can install trusted CAs you might be able to do it - but with IOT like a lightbulb or something like an alexa or other such iot - prob not possible without some really low level hacking of the iot OS itself.
SSL is meant to be end to end encryption - and not trivial to circumvent and decrypt.. If it was, than it becomes useless.. Not saying it is impossible.. Interesting show recently was Prime Target - about a way to factor prime numbers, which if you could do that would make our current encryption methods useless..
You could look for some tools like SSLstrip or BEAST, but these are exploits against SSL/TLS specific vulnerabilities.. And not actually breaking the encryption.. But with the security of iot devices it wouldn't be unbelievable to think they are not up to date with the implementation of ssl/tls they are using ;)
-
getting to the firmware itself, adding your own ca to its trusted ca list, then reflashing or triggering a firmware update, all the while that last process happens over the connection i want to be in the middle in, not to speak of the legality of such things, would make it impossible indeed

-
@b3rt see my edit of above post, there are some tools you could try ;) but once you had hacked the iot os to trust your cert - you wouldn't have to do that in real time or anything.. You would then really own all its encrypted comms. Until its firmware was updated, etc..
-
getting a squid transparent proxy running on pfsense with ssl/mitm from scratch wasn't easy tbqh (but maybe that's another topic...)
it is quite satisfying though to see the RT access logs flow in pfsense, and the secure lock in the browser at the same time (=
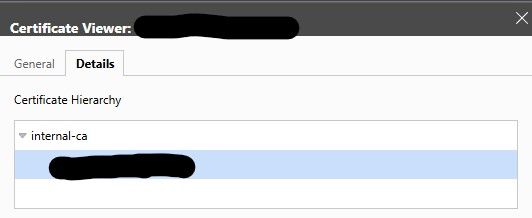
but still, as you mentioned before, without the device accepting my ""internal-ca"", it's besides the point