Port Forwarding stopped working after upgrading to 2.8.0
-
so i found out that my websites i host werent hosting anymore
they used to work i Port forward port 80 to my webserver VMand on 2.7.2 it worked fine but i noticed now i upgraded to 2.8.0 it no longer allows port 80 to be port forwarded from the Internet side.. it has no issues working on the internal network
but when i goto www.example.com from a 2nd wan or so the pages cant be found.. i try to ping the dns name and it will give me the ip address of my dynamic dns ip address but i cant access it..
i not sure if the other port forwards i have work but the web hosting i do for a few websites none are working just behind the internal network
is there something i need to toggle on and off to get port forwarding to work again after upgrading? or do i need to do which i had to do in past save the config... format and install the latest pfsense and then import the xml config file.. as i found that helped..
but confused why its doing this
oh ya openvpn isnt working either i get the TLS handshaking error so i guess as it cant port forward through pfsense
here is pic of my port forward
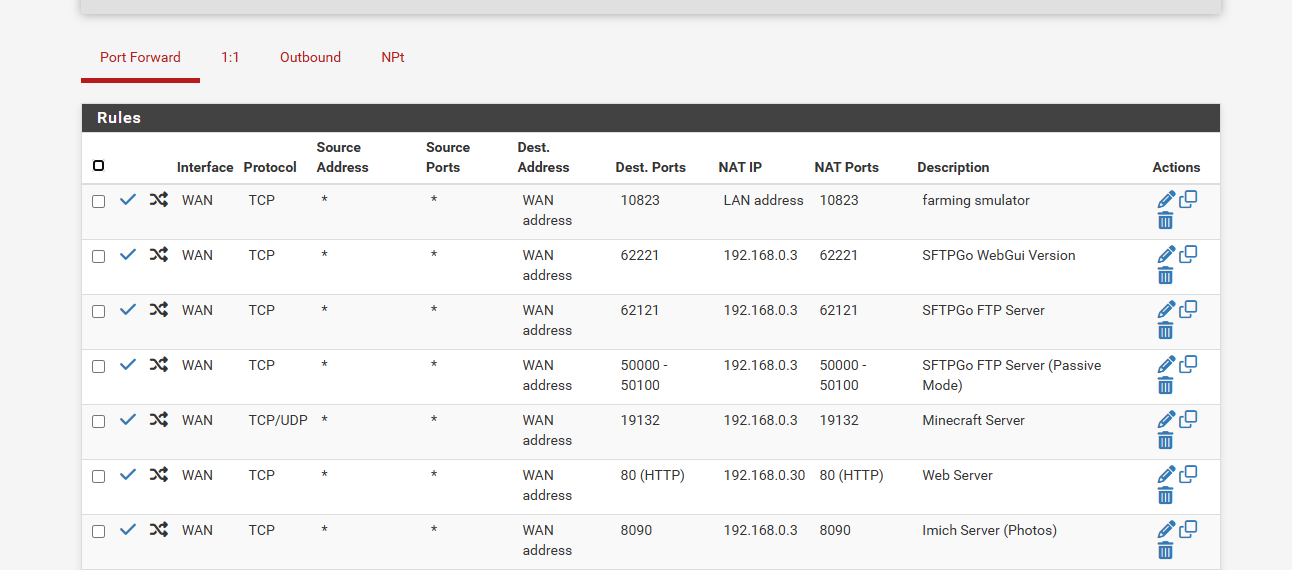
-
@comet424 Nothing should be necessary on your part. Did you go through https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat-port-forwards.html ?
Every so often there are similar posts and sometimes the issue is a software firewall on the web server and not even pfSense...
-
@SteveITS no i havent ill take a look
i know i been running the setup 10 years havent changed things
i just know after i upgraded i had issues
i run windows server 2016 that hosts my websites if that helps at all?
but ill check the url you sent
as it is frustrating.. the websites work on the local network
but come from a external internet address it will show the ip of the pfsense box but it wont port forward.
-
@comet424 I would try to disable the Windows firewall to test. If the Windows network detection changes as to public/private/domain those can have different rules.
-
@SteveITS so i disabled the private and public firewall.. i also ran windows update to make sure its all up todate
on the computer thats on the outside of the network i still cant access websites
if i ping each webaddress they all come up with the same ip address of my pfsense box but the pings fail they dont get forwarded to the 192.168.0.30 ip address
and i have Pure NAT setup from that article it was as far as i got i not sure how to read the logging or trace stuff so never made it that far yet
-
so like
if i type
www.example.com on the local network in the web browser i get the website
if i ping www.example.com on the local network it pings and returns my ip addressand my TTLbut if i use computer on the outside of pfsense
and i
goto www.example.com in the broswer i just get blank cant be found
and if i ping www.example.com on the outside of pfsen it sees the ip address but returns nothing
as it gets destination error..hope that helps too..
and Windows server is up to date and the firewalls private and public are disabled
i tried
system logs firewall under status normal viewand i searched for 192.168.0.30 the webserver address and it didnt find any ip
-
so i did a ping from the remote computer to the www.example.com the example website
it gets ip but the request time out... the states filter shows this if it helps
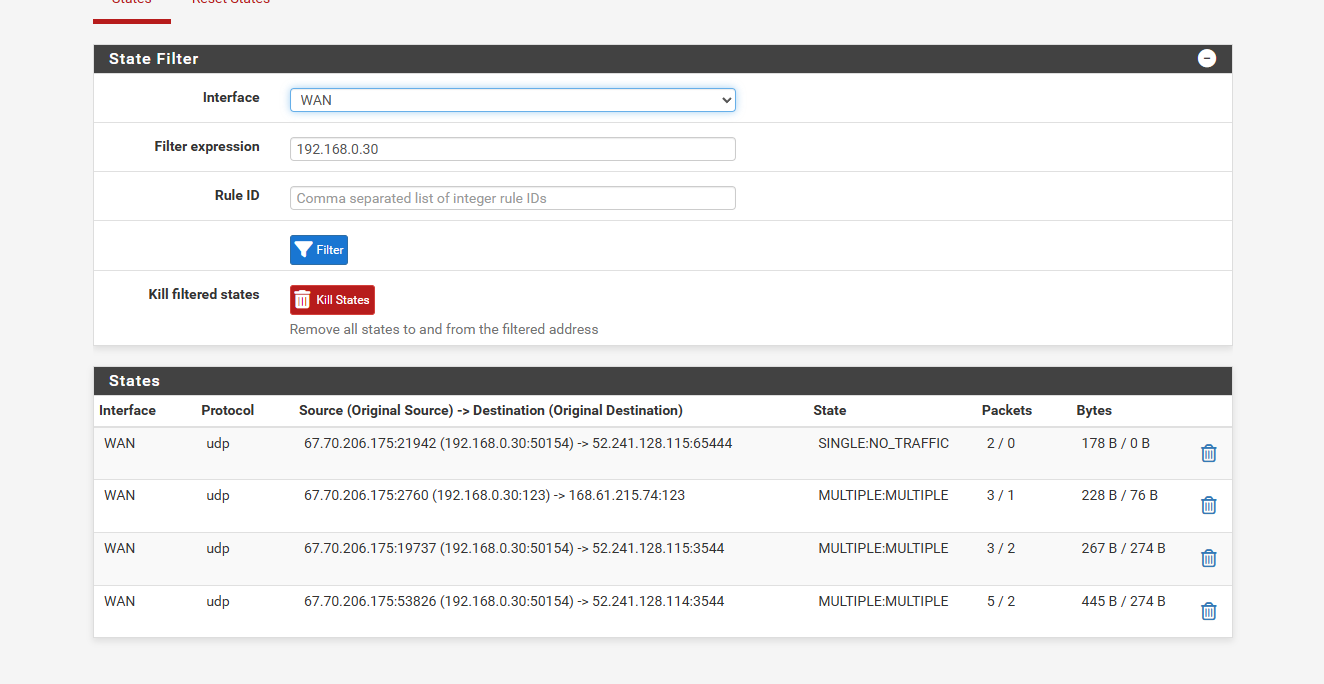
-
@comet424 You will need to forward ICMP to forward pings. I don't know that I've tried to forward ICMP and use reflection on that.
Is one of those destinations your remote IP? They look more like outbound connections, at a glance.
-
@SteveITS the 67.70.206.175 is the remote computer not connected to pfsense so i pinged on there the webaddress
and how do i enable icmp thats for pinging right just the port on port forward? or LAN?
and here i did states again and on the remote computer i did the website address in Internet Explorer and got
and i did a kill states before i tried webpage...
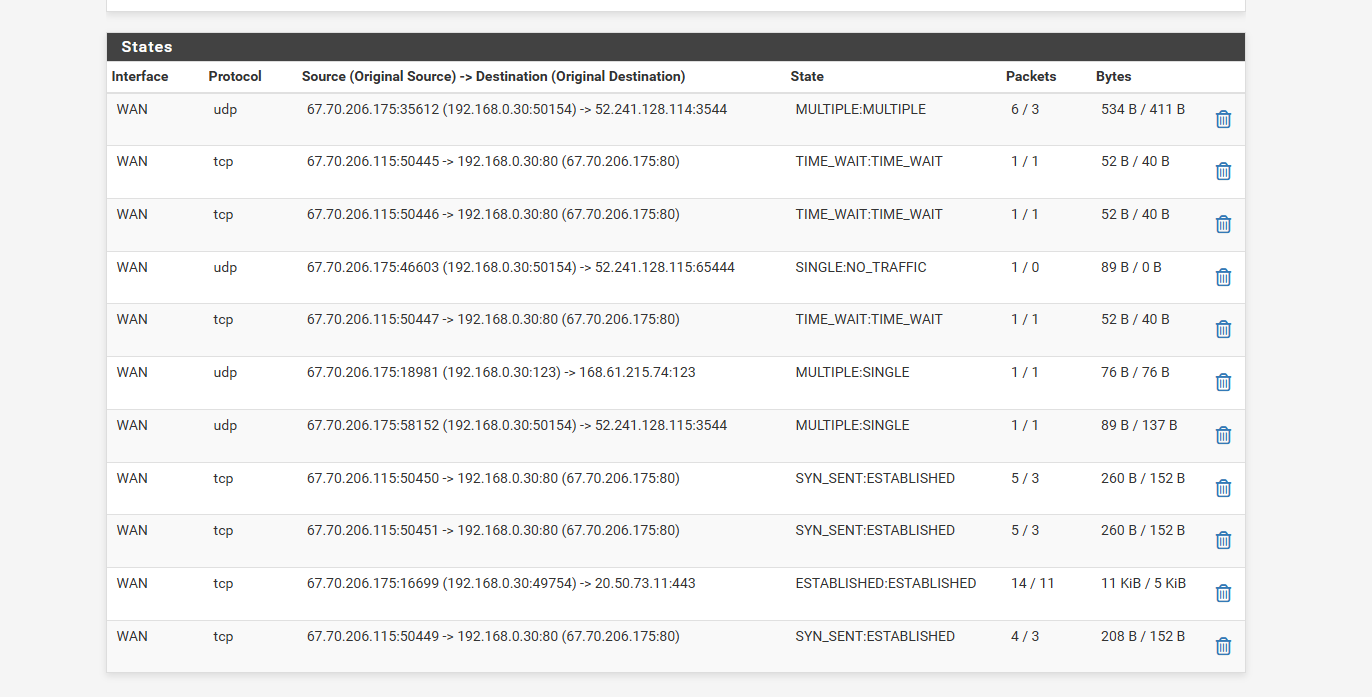
-
so i added icmp on the port forward but got request timed out still
port forward side
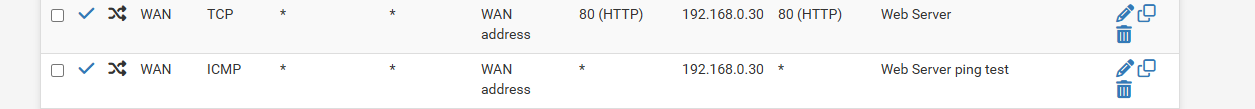
-
@comet424 said in Port Forwarding stopped working after upgrading to 2.8.0:
the X.X.206.175 is the remote computer not connected to pfsense
Nope that's your external WAN IP address in those states.
But in the state table above we can see incoming connections from X.X.206.115 to the WAN address and they are being correctly forwarded to the internal server IP.
I assume you have that filtered for WAN only? If you allow all interfaces you should also see a corresponding state on LAN.
The state you see on WAN shows traffic both ways BUT only 1 packet so it's probably just being refused.
-
Where exactly are you testing from? How is it connected? It's in the same subnet as your WAN.
I can open an http connection to that site and ping it OK from my actual remote location.
-
so the way i testing is
my modem has pppoe and has wifi and lan
so i connect wifi for the remote comp
and its the 67.70.206.115and then i do ppoe on the WAN connection to the modem
and it logs in a 2nd time
and i get the
67.70.206.175 so i have 2 different WAN interfacesfiltered for WAN only if you mean states? then ya i do the screen shots above
if you mean filtered that i only have port forward on WAN to 192.168.0.30 then ya only Wanlike at moment my OpenVPN started working ok on the remote comp i using.. but the Webserver address still show nothing and i cant ping
-
and i do this wifi remote to do testing to make my network work outside of the network on the internet side and it all worked.. before back in 2.7.2 but i not sure if its a problem with my modem or it didnt upgrade right and i gotta start overr by format and then force update from the xml file so not sure
or maybe my modem doesnt like the new pfsense i dunno
-
@stephenw10 since you said you can ping my pfsense box
let me know if this workswww.mcproductions.mine.nu its my old dj website as i wanna upgrade it to AI generated website
but i cant ping it on the remote side.. but if it works for you to goto website and to ping it
the i guess my modem doesnt let me to do what it could before
and my openvpn client can connect to pfsense on the remote comp but not the websites and i need to test those other ports i have for port forwarding
-
@comet424 said in Port Forwarding stopped working after upgrading to 2.8.0:
let me know if this works
www.mcproductions.mine.nu
Yup that works.
Ok probably you're hitting an asymmetric routing problem that was previously allowed by floating state policy in 2.7.2. This has been switched back to Interface Bound in 2.8 which is more secure:
https://docs.netgate.com/pfsense/en/latest/releases/2-8-0.html#generalYou can try setting back to floating to test if you need to. However from something inside the WAN subnet like that is not really a good test. Especially if it's through an ISP router that may or may not be doing something! Much better to test from real external address like a tethered cell phone if you can.
-
@stephenw10
so i tried the floating and even rebooted pfsense.. but my remote comp still cant do pinging or the website... so its probably what you said the modem could be doing something funky and i need a real external internet to test.. . i dont have a cellphone with internet,. but least you said its workingso ill set it back interface bound policy
i not 100% sure what the 2 options means it kinda sounds like if you have a vpn that it wont leak onto the WAN side you dont need the egress floating ive setup before like a kill switch so if the vpn goes down no internet.. my take it does that kinda thing... if i wrong well i wrong i just trying to guess what it does in simple words terms and not engineer words lol
but ill see about different external internet testing like if i at home depot and use there wifi
be outta the way but least its a different internet to test...,.. here i was going to do a restore from my config file and see if that would fixed things...always learning new something everyday... and here my setup testing was flawless probably the provider updated the modems firmware and thne things bugger up too lol
i appreciate your guys help as i wouldnt have learned my testing remote comp isnt really a good idea
-
Upgrading pfSense wouldn't break any NAT setup.
What did break your NAT is most probably : what was your pfSense WAN IP before you've upgraded ?
And after ? If your WAN IP is "RFC 1918" then don't look any further : you have to change the NAT rule in the up stream, probably ISP router.Next step : every NAT rule has a WAN firewall rule - as traffic has to able to get into the WAN interface.
Here are mine :
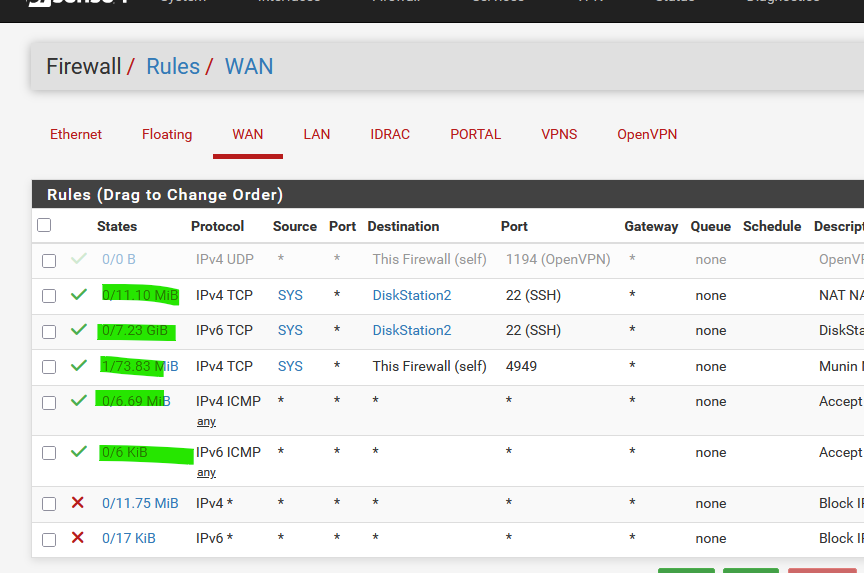
Observe the States column. When traffic start to enter, the Sates counter start to go up.
If they stay at 0/0 then you'll know the traffic never reaches the pfSense WAN interface, so the issue is upstream.Anyway : https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat-port-forwards.html is the check list to follow.
-
@Gertjan
ah ok for me my WAN is PPPOE and i use a login and password and then get a dynamic ip
not sure how that RFC 1918 i remember seeing that and doing it for something in the pastill check i did find out apparently my websites were working but the way i was testing is aysemetical which not sure what that means or what not
but i did find another issues i not sure if its my network card or what not
i got a 10Gtek Dual 1.25GB nic supposed to be intel as i wanted to be compatible with pfsensebut ive been experiencing since i upgraded to 2.8.0 that there so i not sure if 10Gtek company if its compatible with pfsense or not
as networking works.. and then at random times it will work partially say accessing the pfsense page you can access the page login but thats it or you loose connection.. and then might come back.. Vlans come and then they go with my cameras.. but once you reboot pfsense it works totally again.... its weird had no issues with 2..7.2 so i not sure if its a glitch bad upgrade or card that is slowly faulting but this randomise is also randomly how long between issues before was like ever 15 min to an hour to like a day or 2
-
That's not a NIC issue, you'd see everything fail if it was. Sounds more like a routing issue or possible something stalling out PHP.
Check the system logs covering the time it happened.