@gabacho4 right, so working from home again today and noticed the same thing is happening again (ah man!)
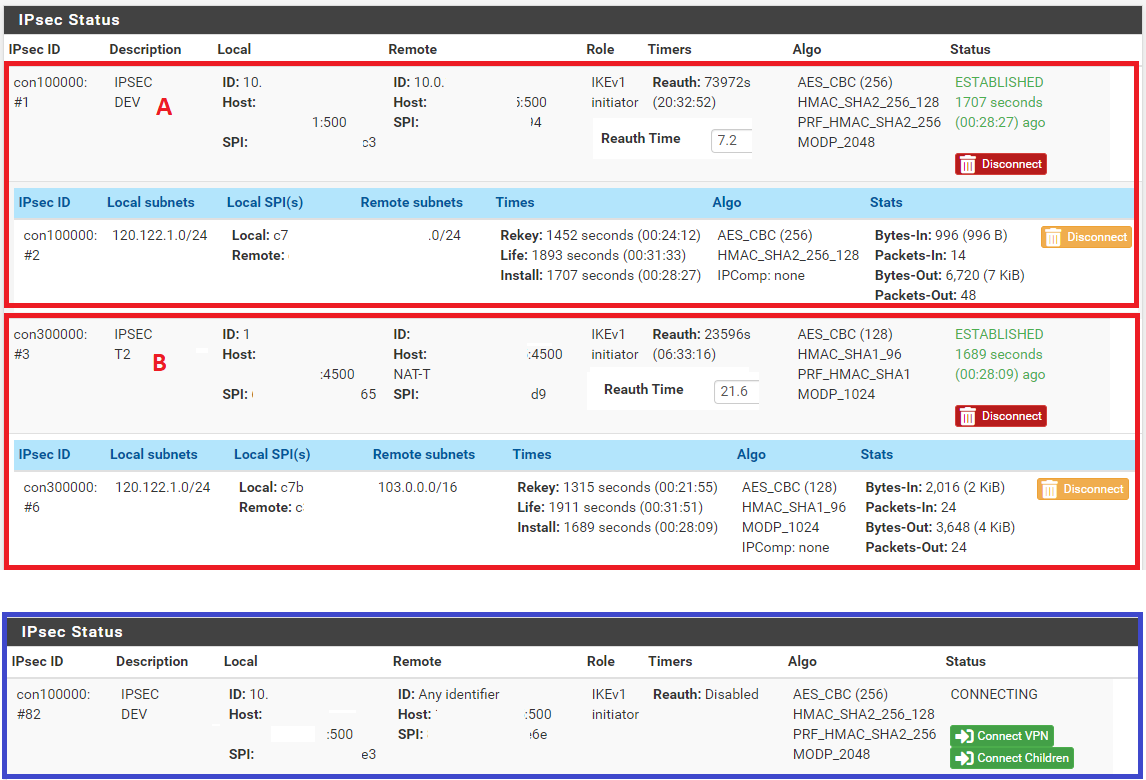
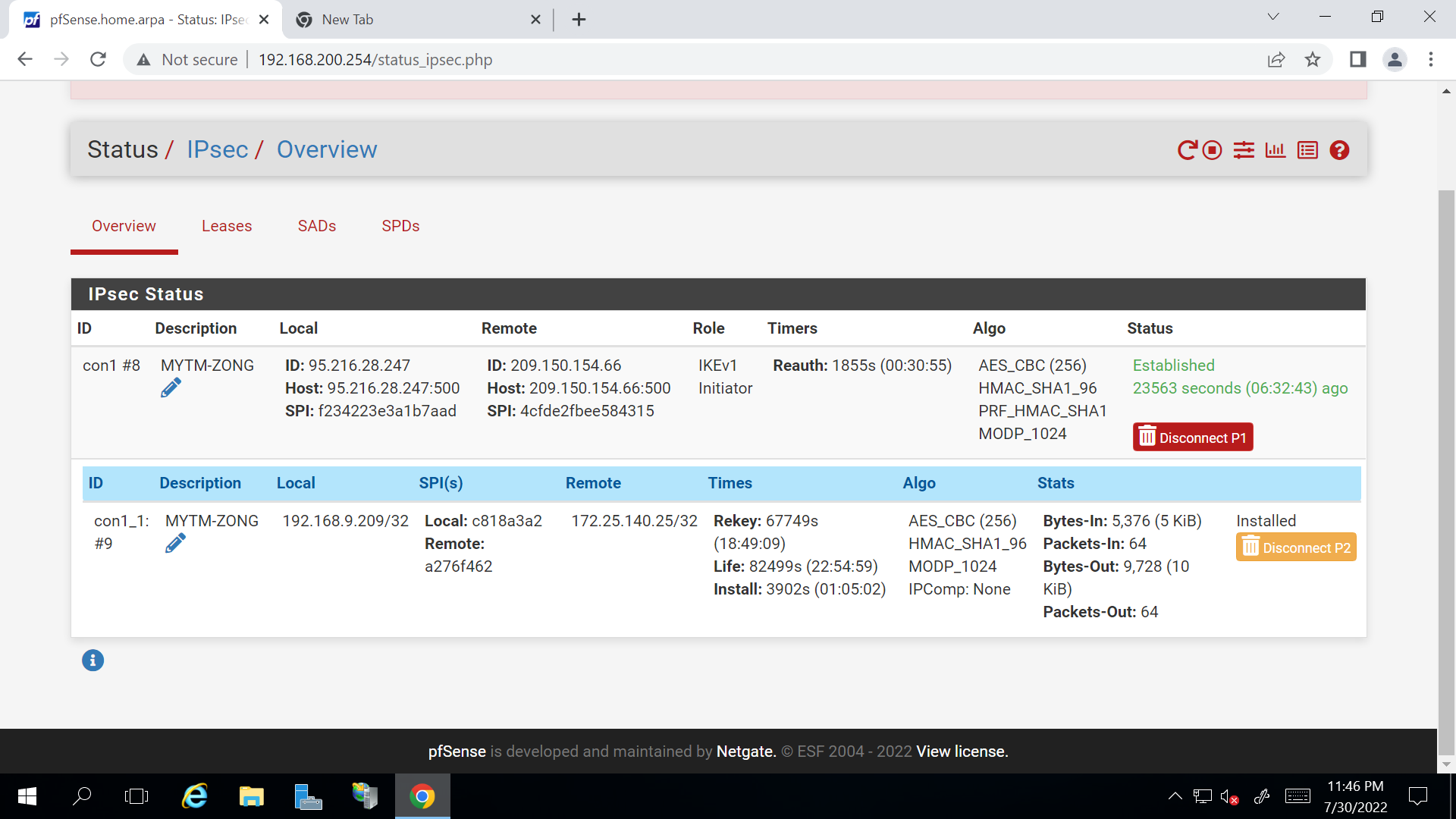
If I keep pinging it, phase 2 tunnel remains open. However if I leave it for a minute or so, it stops responding to traffic from site a -> b.
Eventually either I manually initiate a ping from site b -> site a or IPSec keepalive ping runs and brings the tunnel back to life.
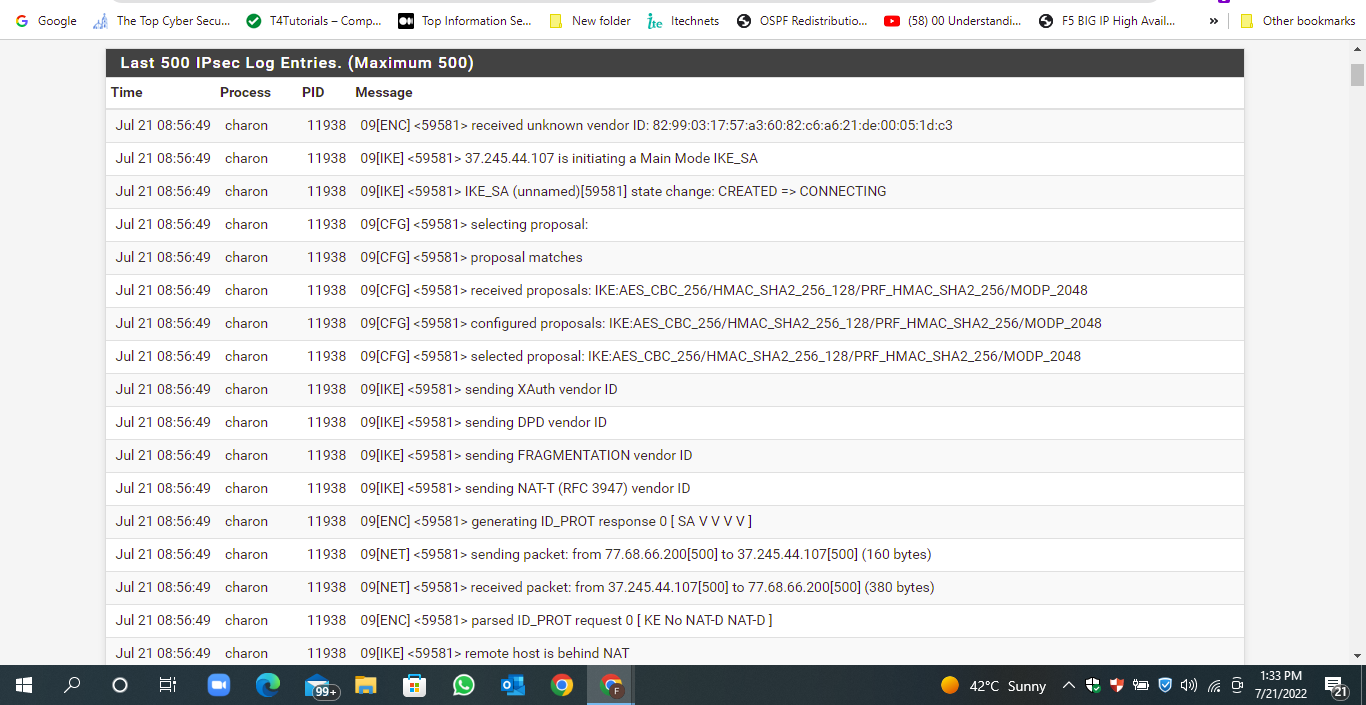
As far as logs go, there's nothing I wouldn't expect on either end, as below...
Spoiler
2022-07-26 09:17:42.639596+01:00 charon 5863 12[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:17:42.639664+01:00 charon 5863 12[ENC] <con1|724> parsed INFORMATIONAL request 16 [ ]
2022-07-26 09:17:42.639720+01:00 charon 5863 12[ENC] <con1|724> generating INFORMATIONAL response 16 [ ]
2022-07-26 09:17:42.639767+01:00 charon 5863 12[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:17:52.691369+01:00 charon 5863 13[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:17:52.691441+01:00 charon 5863 13[ENC] <con1|724> parsed INFORMATIONAL request 17 [ ]
2022-07-26 09:17:52.691478+01:00 charon 5863 13[ENC] <con1|724> generating INFORMATIONAL response 17 [ ]
2022-07-26 09:17:52.691534+01:00 charon 5863 13[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:01.845443+01:00 charon 5863 08[IKE] <con1|724> sending DPD request
2022-07-26 09:18:01.845486+01:00 charon 5863 08[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:18:01.845514+01:00 charon 5863 08[IKE] <con1|724> activating new tasks
2022-07-26 09:18:01.845543+01:00 charon 5863 08[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:18:01.845572+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL request 13 [ ]
2022-07-26 09:18:01.845640+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:01.852339+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:01.852393+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL response 13 [ ]
2022-07-26 09:18:01.852417+01:00 charon 5863 08[IKE] <con1|724> activating new tasks
2022-07-26 09:18:01.852452+01:00 charon 5863 08[IKE] <con1|724> nothing to initiate
2022-07-26 09:18:11.704381+01:00 charon 5863 05[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:11.704452+01:00 charon 5863 05[ENC] <con1|724> parsed INFORMATIONAL request 18 [ ]
2022-07-26 09:18:11.704489+01:00 charon 5863 05[ENC] <con1|724> generating INFORMATIONAL response 18 [ ]
2022-07-26 09:18:11.704532+01:00 charon 5863 05[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:20.912446+01:00 charon 5863 05[IKE] <con1|724> sending DPD request
2022-07-26 09:18:20.912527+01:00 charon 5863 05[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:18:20.912576+01:00 charon 5863 05[IKE] <con1|724> activating new tasks
2022-07-26 09:18:20.912636+01:00 charon 5863 05[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:18:20.912689+01:00 charon 5863 05[ENC] <con1|724> generating INFORMATIONAL request 14 [ ]
2022-07-26 09:18:20.912803+01:00 charon 5863 05[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:20.919686+01:00 charon 5863 05[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:20.919751+01:00 charon 5863 05[ENC] <con1|724> parsed INFORMATIONAL response 14 [ ]
2022-07-26 09:18:20.919777+01:00 charon 5863 05[IKE] <con1|724> activating new tasks
2022-07-26 09:18:20.919812+01:00 charon 5863 05[IKE] <con1|724> nothing to initiate
2022-07-26 09:18:30.799984+01:00 charon 5863 05[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:30.800058+01:00 charon 5863 05[ENC] <con1|724> parsed INFORMATIONAL request 19 [ ]
2022-07-26 09:18:30.800105+01:00 charon 5863 05[ENC] <con1|724> generating INFORMATIONAL response 19 [ ]
2022-07-26 09:18:30.800149+01:00 charon 5863 05[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:39.937634+01:00 charon 5863 16[IKE] <con1|724> sending DPD request
2022-07-26 09:18:39.937679+01:00 charon 5863 16[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:18:39.937711+01:00 charon 5863 16[IKE] <con1|724> activating new tasks
2022-07-26 09:18:39.937740+01:00 charon 5863 16[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:18:39.937788+01:00 charon 5863 16[ENC] <con1|724> generating INFORMATIONAL request 15 [ ]
2022-07-26 09:18:39.937870+01:00 charon 5863 16[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:39.945121+01:00 charon 5863 16[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:39.945170+01:00 charon 5863 16[ENC] <con1|724> parsed INFORMATIONAL response 15 [ ]
2022-07-26 09:18:39.945192+01:00 charon 5863 16[IKE] <con1|724> activating new tasks
2022-07-26 09:18:39.945231+01:00 charon 5863 16[IKE] <con1|724> nothing to initiate
2022-07-26 09:18:49.924878+01:00 charon 5863 14[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:49.924960+01:00 charon 5863 14[ENC] <con1|724> parsed INFORMATIONAL request 20 [ ]
2022-07-26 09:18:49.925006+01:00 charon 5863 14[ENC] <con1|724> generating INFORMATIONAL response 20 [ ]
2022-07-26 09:18:49.925049+01:00 charon 5863 14[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:18:59.927890+01:00 charon 5863 10[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:18:59.927960+01:00 charon 5863 10[ENC] <con1|724> parsed INFORMATIONAL request 21 [ ]
2022-07-26 09:18:59.927995+01:00 charon 5863 10[ENC] <con1|724> generating INFORMATIONAL response 21 [ ]
2022-07-26 09:18:59.928038+01:00 charon 5863 10[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:09.994610+01:00 charon 5863 10[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:09.994721+01:00 charon 5863 10[ENC] <con1|724> parsed INFORMATIONAL request 22 [ ]
2022-07-26 09:19:09.994778+01:00 charon 5863 10[ENC] <con1|724> generating INFORMATIONAL response 22 [ ]
2022-07-26 09:19:09.994849+01:00 charon 5863 10[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:19.996800+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:19.996884+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL request 23 [ ]
2022-07-26 09:19:19.996928+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL response 23 [ ]
2022-07-26 09:19:19.997050+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:30.000328+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:30.000429+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL request 24 [ ]
2022-07-26 09:19:30.000496+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL response 24 [ ]
2022-07-26 09:19:30.000586+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:40.003944+01:00 charon 5863 12[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:40.004053+01:00 charon 5863 12[ENC] <con1|724> parsed INFORMATIONAL request 25 [ ]
2022-07-26 09:19:40.004132+01:00 charon 5863 12[ENC] <con1|724> generating INFORMATIONAL response 25 [ ]
2022-07-26 09:19:40.004206+01:00 charon 5863 12[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:50.096681+01:00 charon 5863 08[IKE] <con1|724> sending DPD request
2022-07-26 09:19:50.096726+01:00 charon 5863 08[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:19:50.096762+01:00 charon 5863 08[IKE] <con1|724> activating new tasks
2022-07-26 09:19:50.096799+01:00 charon 5863 08[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:19:50.096829+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL request 16 [ ]
2022-07-26 09:19:50.096897+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:50.096965+01:00 charon 5863 06[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:50.097004+01:00 charon 5863 06[ENC] <con1|724> parsed INFORMATIONAL request 26 [ ]
2022-07-26 09:19:50.097035+01:00 charon 5863 06[ENC] <con1|724> generating INFORMATIONAL response 26 [ ]
2022-07-26 09:19:50.097076+01:00 charon 5863 06[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:19:50.106546+01:00 charon 5863 06[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:19:50.106593+01:00 charon 5863 06[ENC] <con1|724> parsed INFORMATIONAL response 16 [ ]
2022-07-26 09:19:50.106616+01:00 charon 5863 06[IKE] <con1|724> activating new tasks
2022-07-26 09:19:50.106651+01:00 charon 5863 06[IKE] <con1|724> nothing to initiate
2022-07-26 09:20:00.100373+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:20:00.100444+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL request 27 [ ]
2022-07-26 09:20:00.100480+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL response 27 [ ]
2022-07-26 09:20:00.100525+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:20:10.103514+01:00 charon 5863 15[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:20:10.103641+01:00 charon 5863 15[ENC] <con1|724> parsed INFORMATIONAL request 28 [ ]
2022-07-26 09:20:10.103738+01:00 charon 5863 15[ENC] <con1|724> generating INFORMATIONAL response 28 [ ]
2022-07-26 09:20:10.103852+01:00 charon 5863 15[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:22:59.538736+01:00 charon 5863 11[IKE] <con1|724> sending DPD request
2022-07-26 09:22:59.538788+01:00 charon 5863 11[IKE] <con1|724> queueing IKE_DPD task
2022-07-26 09:22:59.538832+01:00 charon 5863 11[IKE] <con1|724> activating new tasks
2022-07-26 09:22:59.538888+01:00 charon 5863 11[IKE] <con1|724> activating IKE_DPD task
2022-07-26 09:22:59.538935+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL request 17 [ ]
2022-07-26 09:22:59.539040+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:22:59.546468+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:22:59.546518+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL response 17 [ ]
2022-07-26 09:22:59.546541+01:00 charon 5863 11[IKE] <con1|724> activating new tasks
2022-07-26 09:22:59.546576+01:00 charon 5863 11[IKE] <con1|724> nothing to initiate
2022-07-26 09:23:03.314643+01:00 charon 5863 11[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:03.314727+01:00 charon 5863 11[ENC] <con1|724> parsed INFORMATIONAL request 29 [ ]
2022-07-26 09:23:03.314771+01:00 charon 5863 11[ENC] <con1|724> generating INFORMATIONAL response 29 [ ]
2022-07-26 09:23:03.314818+01:00 charon 5863 11[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:23:13.270108+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:13.270198+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL request 30 [ ]
2022-07-26 09:23:13.270266+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL response 30 [ ]
2022-07-26 09:23:13.270335+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:23:23.310863+01:00 charon 5863 08[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:23.310932+01:00 charon 5863 08[ENC] <con1|724> parsed INFORMATIONAL request 31 [ ]
2022-07-26 09:23:23.310968+01:00 charon 5863 08[ENC] <con1|724> generating INFORMATIONAL response 31 [ ]
2022-07-26 09:23:23.311017+01:00 charon 5863 08[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
2022-07-26 09:23:33.350443+01:00 charon 5863 15[NET] <con1|724> received packet: from SITEA[500] to SITEB[500] (57 bytes)
2022-07-26 09:23:33.350568+01:00 charon 5863 15[ENC] <con1|724> parsed INFORMATIONAL request 32 [ ]
2022-07-26 09:23:33.350618+01:00 charon 5863 15[ENC] <con1|724> generating INFORMATIONAL response 32 [ ]
2022-07-26 09:23:33.350696+01:00 charon 5863 15[NET] <con1|724> sending packet: from SITEB[500] to SITEA[500] (57 bytes)
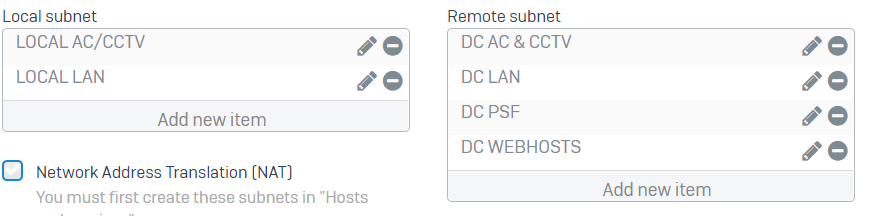
I have the exact same settings from two other sites into Site B and it works no problems at all.
Additionally, I had to add port 500 into the firewall rules as otherwise I was getting retransmit 4 of request with message ID 0 errors when attempting to establish a connection. Now that's gone, but the problem persists!
Chris.