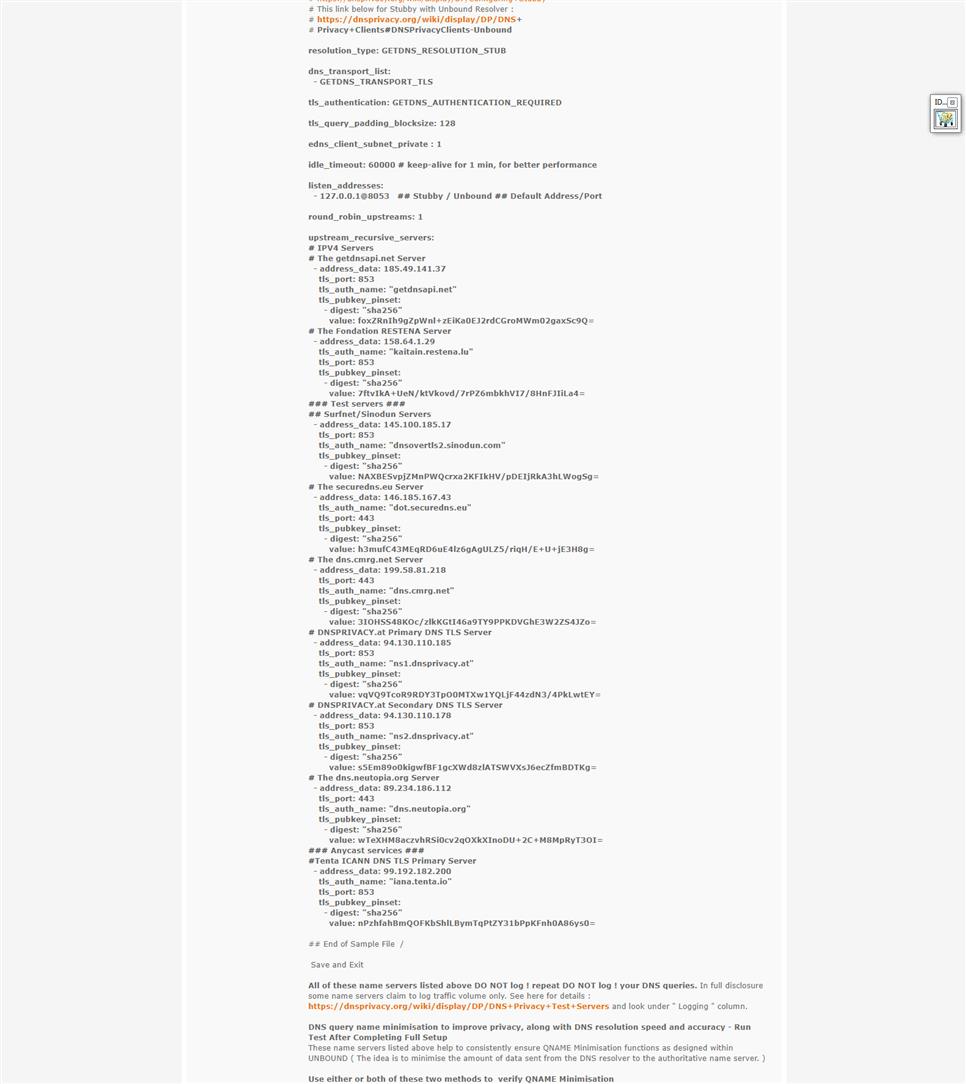
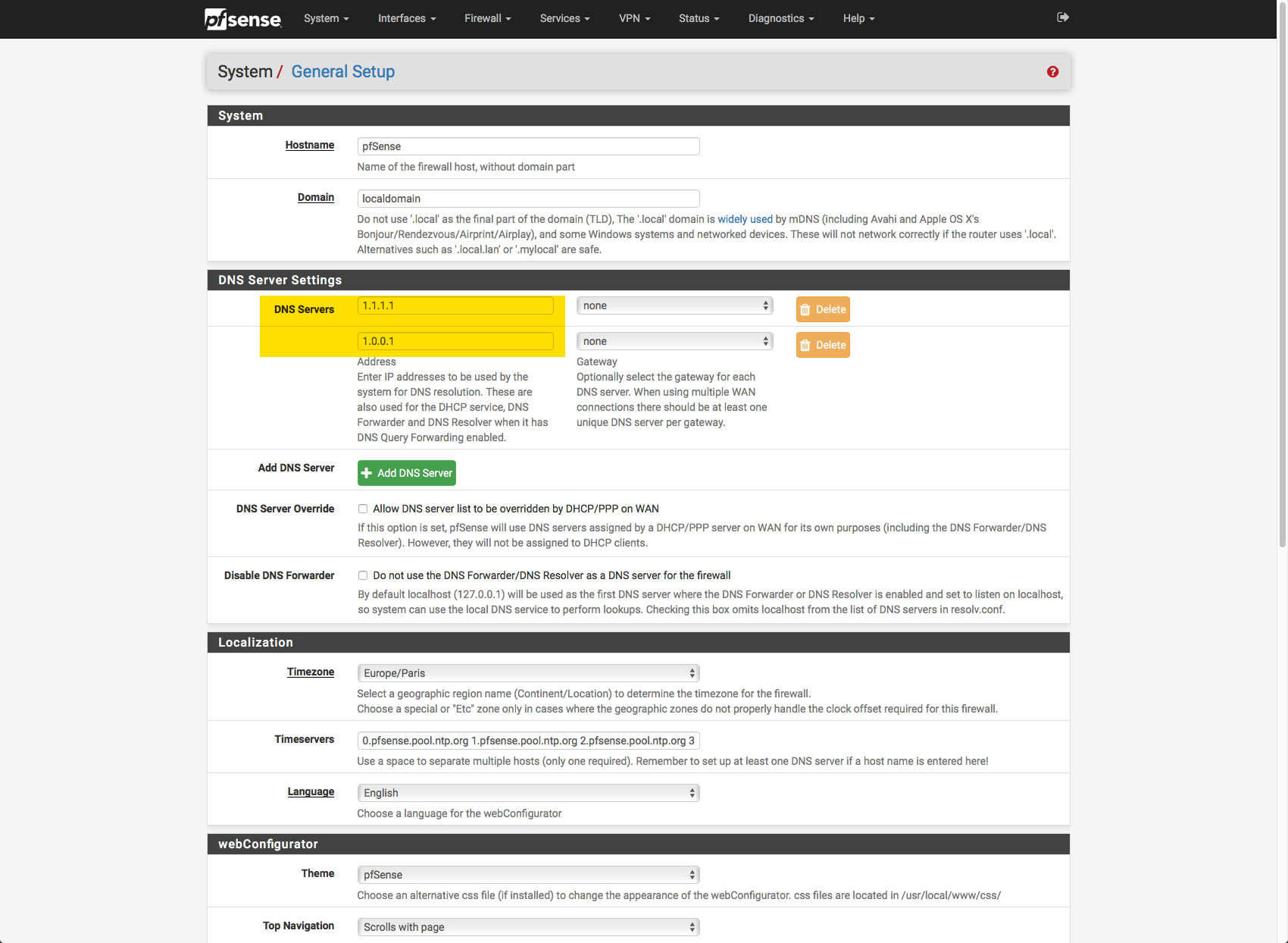
-
0 Votes6 Posts892 Views
-
1 Votes1 Posts4k Views
-
0 Votes9 Posts2k Views
-
0 Votes3 Posts335 Views
-
0 Votes14 Posts5k Views
-
0 Votes4 Posts990 Views
-
0 Votes3 Posts762 Views
-
0 Votes8 Posts2k Views
-
0 Votes2 Posts295 Views
-
0 Votes2 Posts334 Views
-
0 Votes9 Posts1k Views
-
0 Votes9 Posts1k Views
-
1 Votes4 Posts969 Views
-
0 Votes2 Posts1k Views
-
0 Votes4 Posts8k Views
-
0 Votes3 Posts656 Views
-
0 Votes3 Posts538 Views
-
0 Votes2 Posts976 Views
-
0 Votes2 Posts551 Views
-
0 Votes1 Posts505 Views
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.