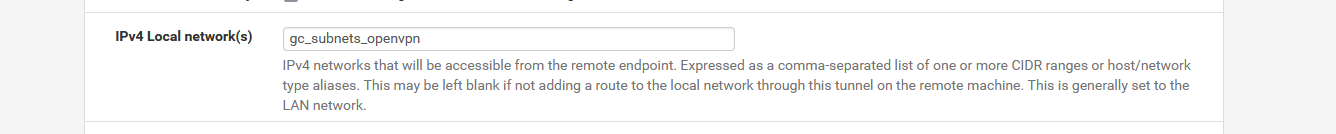
So, I found a problem in the server configuration. I had to include the remote networks in the IPv4 Local network(s) section. Now it says:
192.168.1.0/24,192.168.34.0/24,192.168.42.0/24,192.168.45.0/24,192.168.48.0/24,192.168.51.0/24,192.168.54.0/24
and it works for some of those, but only for some.
I compared the two client configurations on 192.168.34.1 and 192.168.54.1:
<openvpn>
<openvpn-client>
<auth_user></auth_user>
<auth_pass></auth_pass>
<proxy_user></proxy_user>
<proxy_passwd></proxy_passwd>
<vpnid>1</vpnid>
<dco>disabled</dco>
<protocol>UDP4</protocol>
<dev_mode>tun</dev_mode>
<interface>wan</interface>
<ipaddr></ipaddr>
<local_port></local_port>
<server_addr>hoffmann.homeunix.net</server_addr>
<server_port>1194</server_port>
<proxy_addr></proxy_addr>
<proxy_port></proxy_port>
<proxy_authtype>none</proxy_authtype>
<description><![CDATA[Ipheion Solutions management interface]]></description>
<mode>p2p_tls</mode>
<topology>subnet</topology>
<custom_options>verify-x509-name "server" name</custom_options>
<caref>66d22c7d1f7c9</caref>
<certref>66d22c7d9e38e</certref>
<crlref></crlref>
<tls>********</tls>
<tls_type>auth</tls_type>
<tlsauth_keydir>1</tlsauth_keydir>
<digest>SHA256</digest>
<tunnel_network></tunnel_network>
<tunnel_networkv6></tunnel_networkv6>
<remote_network>192.168.54.0/24</remote_network>
<remote_networkv6></remote_networkv6>
<use_shaper></use_shaper>
<allow_compression>asym</allow_compression>
<compression></compression>
<auth-retry-none></auth-retry-none>
<passtos></passtos>
<udp_fast_io></udp_fast_io>
<exit_notify>none</exit_notify>
<sndrcvbuf></sndrcvbuf>
<route_no_pull></route_no_pull>
<route_no_exec></route_no_exec>
<dns_add></dns_add>
<verbosity_level>1</verbosity_level>
<create_gw>both</create_gw>
<data_ciphers>AES-128-GCM,AES-256-CBC</data_ciphers>
<data_ciphers_fallback>AES-256-CBC</data_ciphers_fallback>
<ping_method>keepalive</ping_method>
<keepalive_interval>10</keepalive_interval>
<keepalive_timeout>60</keepalive_timeout>
<ping_seconds>10</ping_seconds>
<ping_action>ping_restart</ping_action>
<ping_action_seconds>60</ping_action_seconds>
<inactive_seconds>0</inactive_seconds>
</openvpn-client>
</openvpn>
and
<openvpn>
<openvpn-client>
<auth_user></auth_user>
<auth_pass></auth_pass>
<proxy_user></proxy_user>
<proxy_passwd></proxy_passwd>
<vpnid>1</vpnid>
<dco>disabled</dco>
<protocol>UDP4</protocol>
<dev_mode>tun</dev_mode>
<interface>wan</interface>
<ipaddr></ipaddr>
<local_port></local_port>
<server_addr>hoffmann.homeunix.net</server_addr>
<server_port>1194</server_port>
<proxy_addr></proxy_addr>
<proxy_port></proxy_port>
<proxy_authtype>none</proxy_authtype>
<description><![CDATA[pfSense-UDP4-1194-millers-config_OpenVPN]]></description>
<mode>p2p_tls</mode>
<topology>subnet</topology>
<custom_options>verify-x509-name "server" name</custom_options>
<caref>66bd527e46839</caref>
<certref>66bd527ec81c0</certref>
<crlref></crlref>
<tls>********</tls>
<tls_type>auth</tls_type>
<tlsauth_keydir>1</tlsauth_keydir>
<digest>SHA256</digest>
<tunnel_network></tunnel_network>
<tunnel_networkv6></tunnel_networkv6>
<remote_network></remote_network>
<remote_networkv6></remote_networkv6>
<use_shaper></use_shaper>
<allow_compression>asym</allow_compression>
<compression></compression>
<auth-retry-none></auth-retry-none>
<passtos></passtos>
<udp_fast_io></udp_fast_io>
<exit_notify>none</exit_notify>
<sndrcvbuf></sndrcvbuf>
<route_no_pull></route_no_pull>
<route_no_exec></route_no_exec>
<dns_add></dns_add>
<verbosity_level>1</verbosity_level>
<create_gw>both</create_gw>
<data_ciphers>AES-128-GCM,AES-256-CBC</data_ciphers>
<data_ciphers_fallback>AES-256-CBC</data_ciphers_fallback>
<ping_method>keepalive</ping_method>
<keepalive_interval>10</keepalive_interval>
<keepalive_timeout>60</keepalive_timeout>
<ping_seconds>10</ping_seconds>
<ping_action>ping_restart</ping_action>
<ping_action_seconds>60</ping_action_seconds>
<inactive_seconds>0</inactive_seconds>
</openvpn-client>
</openvpn>
The only real differences are in
the description,
the CA reference,
the cert reference, and
that the second has remote network specified, client side.