@nimrod said in CPU Temp stuck at 27.9C:
But setting PL1 and PL2 affect how turbo works, and how much power is being used. Setting them at 10W/12W - which they really should have been at the factory - temps are now down to 40'sC with "max battery" set in BIOS or mid 50'sC with "max performance battery". I don't think I'm going to even look at "max performance" again, it's doing what I need.
Please tell me where are those settings located, and i will check tomorrow at site. I have similar issue with overheating but the unit is in the rack case that has 120mm fan blowing right above it. Last time i was playing with Topton, except for options to disable VT-d and turbo function, there were no other settings i could adjust. Also, if you can, please tell me whats the exact model and bios bios version.
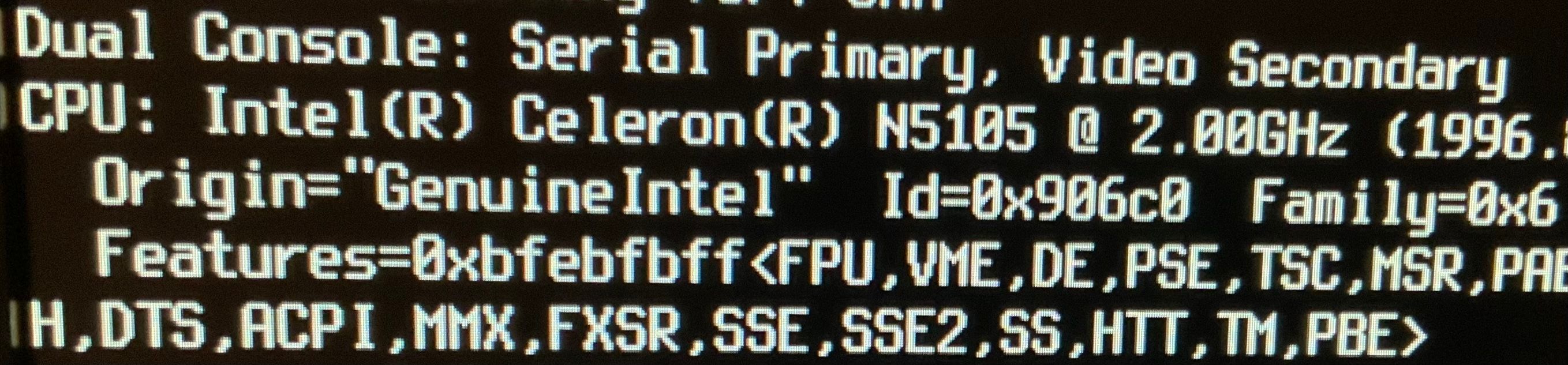
The bios version is 5.19, and the model I have is this one. This has one of these Bluetech boards.
As for the settings, there's a fair bit I've collated from various different sources.
In the BIOS, Advanced, CPU, Power Management, View/Configure Turbo Options.
Set Power Limit 1 Override Enabled
Set Power Limit 1 as 10000 (10W)
Set Power Limit 2 Override Enabled
Set Power Limit 2 as 12000 (12W)
CPU VR Settings, sett PSYS PMax Power at 176.
Go into Acoustic Noise Mitigation, and enable.
Set Slow Slew Rate for VccIn Domain to [Fast/16]
And then set C States enabled.
I also enabled ACPI, but I haven't noted down where that was.
In tunables in pfSense,
hw.acpi.cpu.cx_lowest=C3
hw.ibrs_disable=1
machdep.hwpstate_pkg_ctrl=0
dev.cpu.0.cx_lowest=C3
dev.cpu.1.cx_lowest=C3
dev.cpu.2.cx_lowest=C3
dev.cpu.3.cx_lowest=C3
I completely understand. Im not bashing Topton or any other device, but you literally get what you pay for.
Oh definitely. I've paid much more for much worse, though, especially in the modem-router and load balancer/fallover arena.
Keep in mind that Netgate 4100 comes with QAT support, so it can not be even compared with those cheaper devices.
Not something that I need. I don't run VPNs or anything like that. I use pfSense as a router that can actually do IPv6, with fallover to 4G when NBN goes AWOL, and filtering with pfBlocker and Suricata.
Also, you should have gone with Yanling if Netgate is not an option. They are the OEM for Protectli. And those devices are well made with proper support and bios updates.
A four-port with a J3160, 8GB of memory and 120GB hard drive is about twice the price of the Topton N5105 based one after I've purchased the memory and drive. It's tough to justify. Performance wise they're not even close! Single core and multicore, it's a third of the processing grunt for twice the price. Looking at the benchmarks that wouldn't be much better than the GX-412TC that's in the PCEngine board it's replacing. I'd just keep using the PCEngines APU4 board.