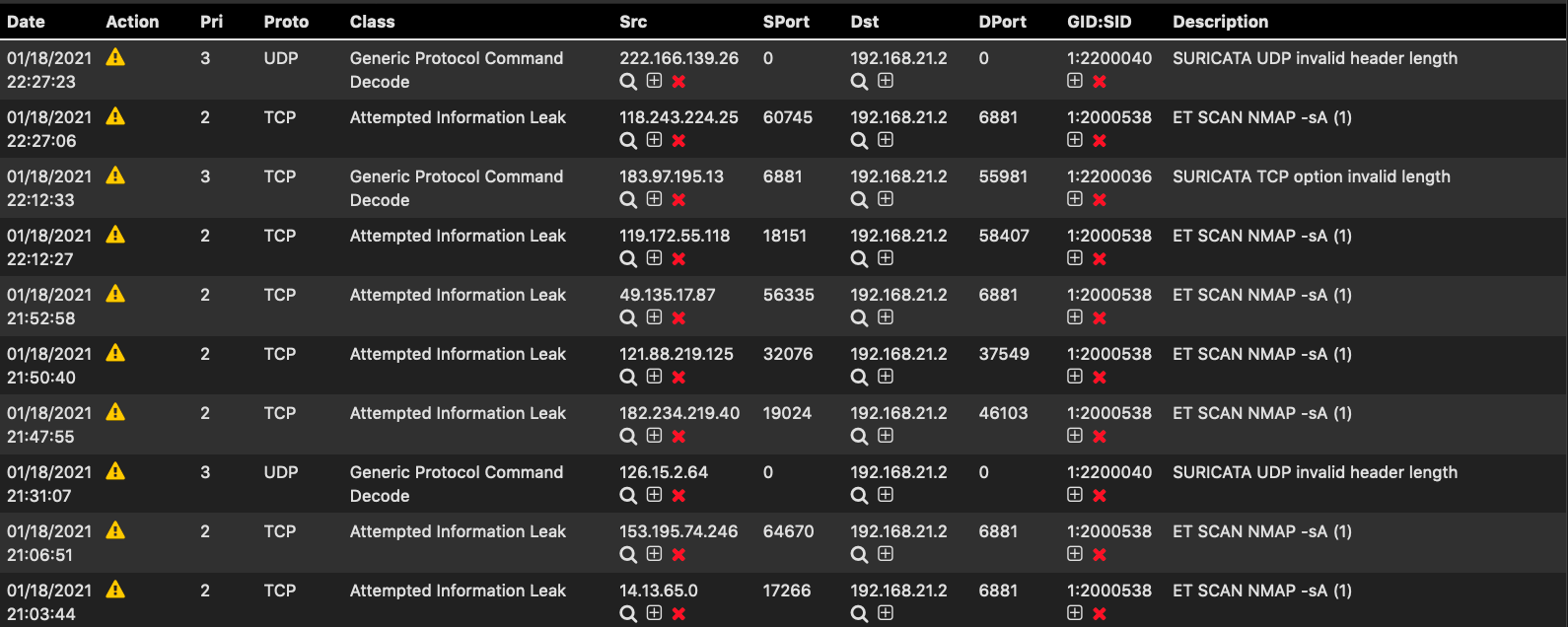
Let's start first with answering your question about the Protocol rule. That rule is coming from the set of built-in Suricata rules that are part of the base package. I forget exactly what the name of that category is at the moment, but if you look under the RULES tab at the list of categories in the drop-down selector you will find some that have "Events" in the name. Those are the built-in Suricata rules. They always get enabled by default. You can suppress that particular rule alert, or you can completely disable that rule SID. Click the red X under the GID:SID column to disable the rule, or click the plus (+) sign to add it to a Suppress List.
Now lets talk about ALERT versus DROP. All rules from the vendors (both the Snort and Emerging Threats teams) come with the rule action set to ALERT. If you want some rules to alert only and others to actually block traffic, then you need to change the ALERT action to DROP for those rules that you wish to block traffic. There are two ways to do that. And for the Snort rules, if you choose to use an IPS Policy, there is a third "sort of" way I will describe last.
The most straightforward way to change ALERT to DROP is to click on the rule action icon on the RULES tab (or you can also do this on the ALERTS tab). A modal dialog will pop up giving you the option to choose the rule action. This works fine for a few rules, but it very time-consuming for lots of rules.
So on to option #2. Use the SID MGMT tab and the features there. The dropsid option is what you want. Open up the sample file on that tab and read through it (you will see the sample files after you click the checkbox to enable SID management). The are ample comments sprinkled throughout with examples. There is also a Sticky Post at the top of this sub-forum describing how to use the SID MGMT feature here: https://forum.netgate.com/topic/128480/how-automatic-sid-management-and-user-rule-overrides-work-in-snort-and-suricata. The SID MGMT feature is a very powerful tool for managing your rules. I highly recommend taking some time to read up on it and experiment with it. A virtual machine is a great place to play with the option to see how it works.
Finally, if you are using the Snort rules with Suricata and enable an IPS Policy (on the CATEGORIES tab), then you have an option to let the IPS policy metadata embedded within the rules govern whether the action is ALERT or DROP for each rule. The Snort team embeds IPS Policy metadata in their rules (only the Snort rules, the ET rules do not have this, so ignore this for ET rules). This policy metadata associates a given rule with one of the pre-defined IPS Policies such as "Connectivity", "Balanced", etc. It also provides alternate rule actions for the various policies. There is a drop-down selector on the CATEGORIES tab (when you enable IPS Policy and have the Snort rules enabled) that lets you choose to have the package code automatically change rule actions for you from ALERT to DROP for those rules in your IPS Policy choice that the Snort team recommends be DROP.