@purleigh
Your post is 'lost'
It's a question about the pfSense GUI package pfBlockerng :
[image: 1747034973323-21726789-53e4-4943-9485-c5df3e3207d4-image.png]
Better : The answer can be found somewhere in that forum
And yes, it's probably a little short-coming, aka bug.
I posted about this a while ago, and proposed a work around.
So, I've a patch :
Open /usr/local/pkg/pfblockerng/pfblockerng.inc
and find
// Collect static DHCPv6 hostnames/IPs
Convert it into comments :
// // Collect static DHCPv6 hostnames/IPs
// foreach (config_get_path('dhcpdv6', []) as $dhcpv6) {
// if (is_array($dhcpv6['staticmap'])) {
// foreach ($dhcpv6['staticmap'] as $smap) {
// $local_hosts[$smap['ipaddrv6']] = strtolower("{$smap['hostname']}");
// }
// }
// }
and then paste just behind it :
// Collect static DHCPv6 hostnames/IPs
## 2024-11-25 Gertjan
foreach (config_get_path('dhcpdv6', []) as $ipv6_interface =>$dhcpv6)
{
if (is_array($dhcpv6['staticmap']))
{
$pdsubnet = '';
foreach ($dhcpv6['staticmap'] as $smap)
{
if (strpos($smap['ipaddrv6'],'::',0) !== false)
{
if (get_interface_track6ip($ipv6_interface))
{
$track6ip = get_interface_track6ip($ipv6_interface);
$pdsubnet = gen_subnetv6($track6ip[0], $track6ip[1]);
// remove '::' from prefix $pdsubnet
$pdsubnet = substr($pdsubnet,0,strpos($pdsubnet,'::'));
}
}
$local_hosts[$pdsubnet.$smap['ipaddrv6']] = strtolower("{$smap['hostname']}");
}
}
}
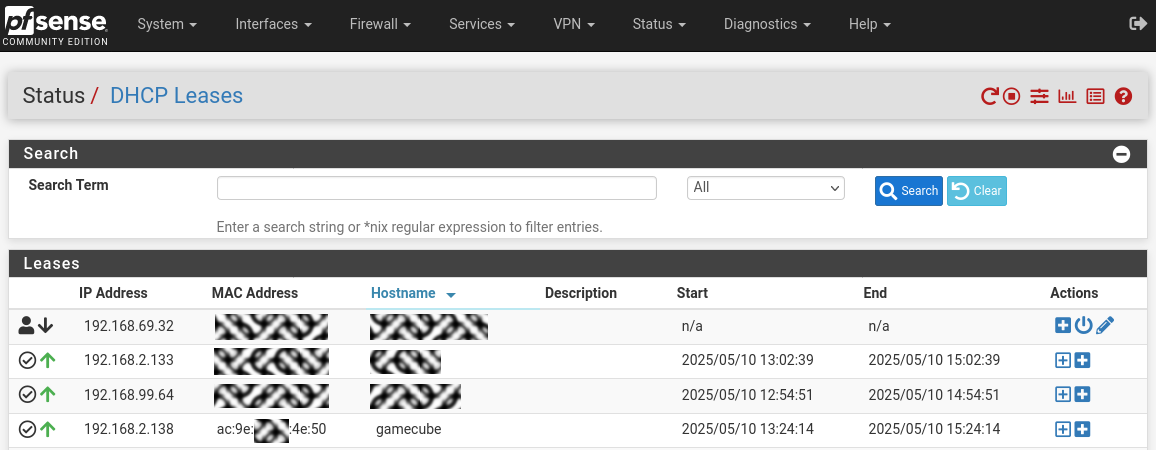
This issue is : you use probably 'IPv6 Prefix tracking", like me.
In that case, static FHCPv6 lease are configured like :
[image: 1747035383882-5375144e-1ce3-454b-bf69-db16fe98cd82-image.png]
and that shorted IPv6 notation isn't the real IPv6.
Or, pfBlockerng uses the IPv6 SRC IP to reverse find host names. And that will fail.
The path shown above test for the shortened ::xx IPv6, and if it finds wone, it prepends the prefix of that LAN interface.
Afaik, the issue isn't listed here.