How do I route outgoing email over WireGuard Tunnel?
-
Have you confirmed that your settings for the tunnel are working properly for other traffic? or is this the first test?
Do you have the Outbound NAT rules in place for that tunnel?
-
@sretalla said in How do I route outgoing email over WireGuard Tunnel?:
Have you confirmed that your settings for the tunnel are working properly for other traffic? or is this the first test?
I am not sure how to answer your first question.
It seems that traffic is coming into my local network over the WireGuard tunnel but is seems that traffic originating on the Local LAN from the Mail Server is NOT going OUT the WireGuard tunnel.
For example receive email at my local self hosted mail server from the outside world. I can also access my locally hosted webpages from the outside world. So the following seems to work.
Internet --> VPS/pfSense ---> WireGuard Tunnel ---> local pfSense ----> Mail Server Host 192.168.4.3 | -----------> Web Server Host 192.168.3.3I can PING from the 4.3 and 3.3 the VPS/pfSense end of the tunnel. I am assuming that traffic that comes IN over the tunnel knows how to get back OUT the tunnel.
But as I said it seems that traffic originating on the Local LAN from the Mail Server is NOT going OUT the WireGuard tunnel to the outside world.
Do you have the Outbound NAT rules in place for that tunnel?
I did NOT setup any NAT Mappings if that is what you are talking about. I am using Automatic Outbound NAT on the LOCAL pfSense and the VPS pfSense.
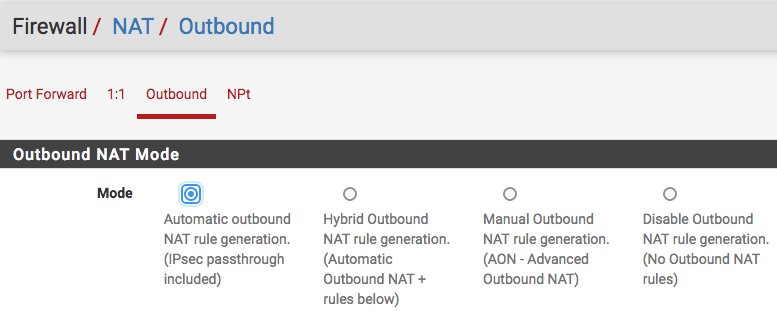
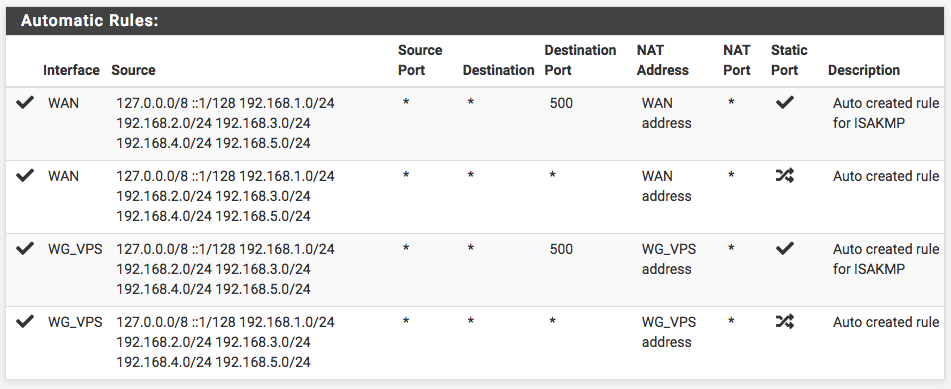
Do I need to create OUTBOUND MAPPINGS FOR 192.168.4.3 ports 25, 465 & 587 and then select Hybrid Outbound NAT Rules? If so how should the MAPPINGS be configured?
-
@sretalla One step forward two steps back.
A missing firewall rule on remote pfSense VPS was blocking traffic originating from the local network pfSense.
Adding a rule I was able to get SMTP traffic to pass from local mail server host ----> local pfSense ---> WireGuard local peer ----> WireGuard VPS but that is as far as it would seem to go.
Struggling with some sort of routing issue with OUTBOUND over WireGuard tunnel. The SMTP traffic did not continue on to the internet via the gateway associated with the mail servers public IP.
Using the PING to on the local pfSense router I attempted to ping apple.com using WireGuard tunnel interface as the source address.
PING apple.com (17.253.144.10) from 10.6.210.1: 56 data bytes --- apple.com ping statistics --- 3 packets transmitted, 0 packets received, 100.0% packet lossI know this must be user error on my part. Hoping I will be guided to the solution soon.
-
@Gertjan said in How do I route outgoing email over WireGuard Tunnel?:
Hello @Gertjan
One, and you probably not going to like it.
No I do not like that idea at all.
You have a VPS, with it's own (I hope) IPv4 and it's own (I hope) IPv6.
Actually the VPS has three (3) public IP address. The first one (1) is for the VPS, the second (2) one is for the web server, the third (3) is for the mail server. Public IP address 2 and 3 are on a subnet different then that of Public IP address 1.
So, do what everybody does ;)
Take the mother of all OSs (Debian), get postfix. Setup.
Add your sauce : imap and or pop.That is not what I am looking or needing to do. I'm guessing there are others that have done what I am attempting to do the difference to their success I guess is that they have a stronger grasp of WireGuard routing and NAT via pfSense.
Hopefully someone will setup and pointout the error(s) in my setup so I can get this working.
What you want, running mail server from your desktop, is I'm sure - possible.
I am not running a mail server from my desktop. I have a VM running a mail server on host machine on my local network. The host machine is connected to the LAN and mail server VM is on its own VLAN.
I have pfSense as a rounter and firewall on the local LAN.
WireGuard "server" is running on pfSense on the VPS and the WireGuard peer is running on pfSense on the local network.
As already stated above : your mail server should use the VPN outgoing connection.
Traffic from this VPN tunnel winds up 'in' the VPS, and should also, in the VPS, routed over to it's extrenal 'real' WAN IP to the final destination.HOW? That is the problem I am having and cannot get that to work.
The other way around : mail (port 25) traffic that comes into your your VPS should be routed to the VPN tunnel, and on the pfSense side routed to the 192.168.4.3 == your mail server.
I am doing 1:1 NAT on the VPS pfSense so all traffic for the mail server public IP goes over the WireGuard tunnel to locally hosted mail server at 192.168.4.3.
It seems that I am having a problem getting any traffic originating from the local network to go out the WireGuard tunnel to the Internet.
Any help to get this worked out would be most appreciated.
-
@Seeking-Sense For a start show all your "mail-vlan" rules and the wireguard peer config on your local machine.
-
@Bob-Dig how about a rough network diagram.
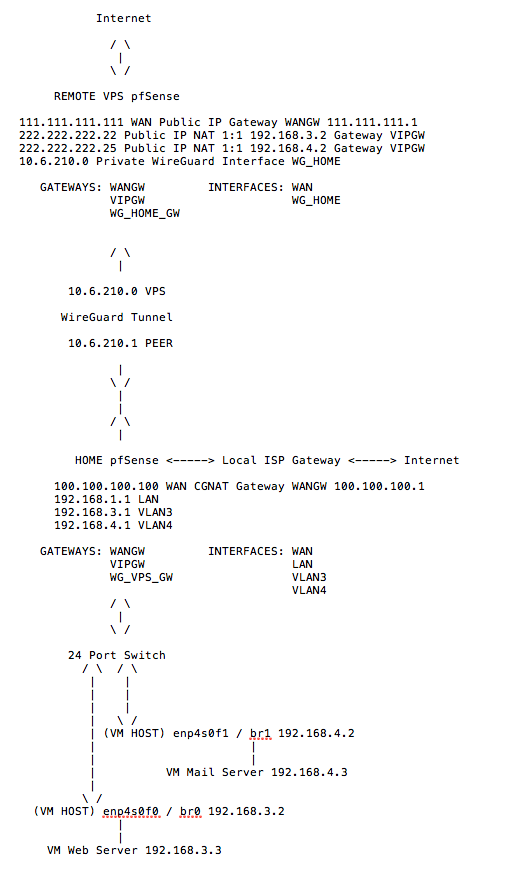
-
Hello Everyone.
My locally self hosted mail server is now sending outbound mail over the WireGuard tunnel to remote mail servers on the Internet.
Resolved the outgoing mail issue by doing the following on the VPS pfSense and the LAN pfSense:
-
Created firewall rules to send traffic out the WireGuard gateway who's source is the mail server host and the destination is port 25.
-
Set Outbound NAT Mode to Hybrid and created a NAT Mapping Rule to Do Not NAT Outbound over WireGuard Interface.
Is there anything else I should configure, tweak or test?
-
-
@Seeking-Sense said in How do I route outgoing email over WireGuard Tunnel?:
Is there anything else I should configure, tweak or test?
Yeah.
One thing to test.
( just consider it ^^)Why not using your VPS as a mail server ?
A mail server is meant to "live" on a server device connected directly to the Internet.
No firewall, not rules, not NAT, nothing .... ( nothing to maintain).Need more domains ? Add more IPv4 (and IPv6 of course) to your VPS.
It's a VPS, so "raid 10" - powered by double triple 'never going down' power lines. same thing for the Internet connection : if its down, a part of the country will be down anyway.I made the shift many years ago : I never regretted it : having full mail control. Mail always works.
And if it fails : no need to call some one : you are the admin. -
@Seeking-Sense said in How do I route outgoing email over WireGuard Tunnel?:
snip
- Set Outbound NAT Mode to Hybrid and created a NAT Mapping Rule to Do Not NAT Outbound over WireGuard Interface.
Is there anything else I should configure, tweak or test?
No, the outbound NAT rule was the only item missing that would allow it to work. But you may have consequently noticed via the logs on the receiving MX that connections will now come from that NAT'd address and NOT the actual sending MX. That is the problem with WireGuard at the moment and i have not come across a workaround myself. I switched from an OpenVPN setup which has policy based routing that allowed SMTP connections from that MX to be routed over the VPN to remove the need to NAT it out. Moving away from OpenVPN to WG has meant this feature has been lost which is a real pain in the backside for identifying spammy IPs to block them and general troubleshooting.
-
@Popolou There is no problem with WireGuard on pfSense, you maybe missing something. But then again, maybe don't run an email-server to begin with.

-
@Bob-Dig Indeed, banish all mail servers and i can actually get some work done.

-
-
@Popolou I am not sure that I am seeing that issue as I am NOT NATing traffic going out over the tunnel.
However it took me a minute to sort out SPF TXT records so that Google and others did not find my mail to be spammy.
-
@Seeking-Sense said in How do I route outgoing email over WireGuard Tunnel?:
sort out SPF TXT records
SPF ? Tht's just a DNS TXT records besides the A, AAA, NS, and MX.
The fun starts with DKIM.
DKIM & DMARC are not optional if you want your mails to be accepted by the biggest 5 free-mail services.
Get your mail server domain name certificate, the one you already use if you also have a web server. Go for web server. Go for the wild card version, or add you MX host name. Assign the certificate to postfix, and make postfix do TLS where ever possible.Sep 8 07:41:36 ns311465 postfix/cleanup[4024]: 3372563E1BC8: message-id=<fe03b95169c2dac3d0047cf5057c8e85.squirrel@www.my-domain.tld> Sep 8 07:41:36 ns311465 opendkim[6675]: 3372563E1BC8: DKIM-Signature field added (s=default, d=my-domain.tld) Sep 8 07:41:36 ns311465 postfix/qmgr[18342]: 3372563E1BC8: from=<gertjan@my-domain.tld>, size=762, nrcpt=1 (queue active) Sep 8 07:41:36 ns311465 return-from-amavis/smtpd[4031]: 8553F63E4DC6: client=localhost.localdomain[127.0.0.1] Sep 8 07:41:36 ns311465 postfix/cleanup[4024]: 8553F63E4DC6: message-id=<fe03b95169c2dac3d0047cf5057c8e85.squirrel@www.my-domain.tld> Sep 8 07:41:36 ns311465 postfix/qmgr[18342]: 8553F63E4DC6: from=<gertjan@my-domain.tld>, size=1619, nrcpt=1 (queue active) Sep 8 07:41:36 ns311465 postfix/smtp[4025]: 3372563E1BC8: to=<gertjan@gmail.com>, relay=127.0.0.1[127.0.0.1]:10026, delay=0.49, delays=0.2/0.03/0/0.26, dsn=2.0.0, status=sent (250 2.0.0 from MTA(smtp:[127.0.0.1]:10025): 250 2.0.0 Ok: queued as 8553F63E4DC6) Sep 8 07:41:36 ns311465 postfix/qmgr[18342]: 3372563E1BC8: removed Sep 8 07:41:36 ns311465 postfix/smtp[4032]: Trusted TLS connection established to gmail-smtp-in.l.google.com[2a00:1450:400c:c07::1b]:25: TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits) key-exchange X25519 server-signature ECDSA (P-256) server-digest SHA256 Sep 8 07:41:37 ns311465 postfix/smtp[4032]: 8553F63E4DC6: to=<gertjan@gmail.com>, relay=gmail-smtp-in.l.google.com[2a00:1450:400c:c07::1b]:25, delay=0.84, delays=0.04/0.03/0.33/0.44, dsn=2.0.0, status=sent (250 2.0.0 OK 1694151697 a18-20020a5d5712000000b00317c20ff0fbsi458053wrv.5 - gsmtp) Sep 8 07:41:37 ns311465 postfix/qmgr[18342]: 8553F63E4DC6: removedMail gets injected by my web mail (squirrel mail) running on the same server.
DKIM gets added
I'll pass it through my own anti 'whatever' filter amvis (maybe I'm sending viruses ?)
It gets back in the queue from amavis
gmail is contacted : with a "Trusted TLS connection established" over IPv6 ( your reverse PTR IPv6 has to point to your MX host name) - IPv6 makes DKIM mandatory when playing with gmail )
The mail is relayed - TLSv1.3 1.0 is now forbidden, TLv1.1 and 1.2 are fading out fast.The 'scan mail before sending' is of optional. Who sends bad stuff to others, after all ?
Note : DMARC comes into play when receiving mail.
On the gmail side :
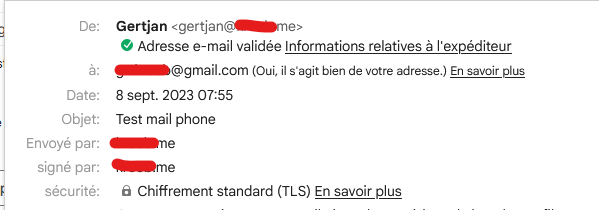
All checks are passed :
Authentication-Results: mx.google.com; dkim=pass header.i=@my-domain.tld header.s=default header.b=YDoN8SvP; spf=pass (google.com: domain of gertjan@my-domain.tld.me designates 2001:41d0:2:beef::2 as permitted sender) smtp.mailfrom=gertjan@my-domain.tld; dmarc=pass (p=REJECT sp=REJECT dis=NONE) header.from=my-domain.tld -
@Gertjan Don't forget DANE.

-
@Bob-Dig said in How do I route outgoing email over WireGuard Tunnel?:
@Gertjan Don't forget DANE.

Adding/mentioning DANE would be counter productive in the motivation process

DANE was invented for those who thought they were DONE.
It is reserved for those who want to be who they say they are in "mail-land" (and https land, and more).
It uses DNSSEC of course - well, I had that up and running already as I went down to low in the DNS rabbit hole.DANE, at the end, will render any CA useless. That's an entire ($$$) business model going down to the drain. Not sure if it simplifies things.
Of course I use have DANE available and set up :
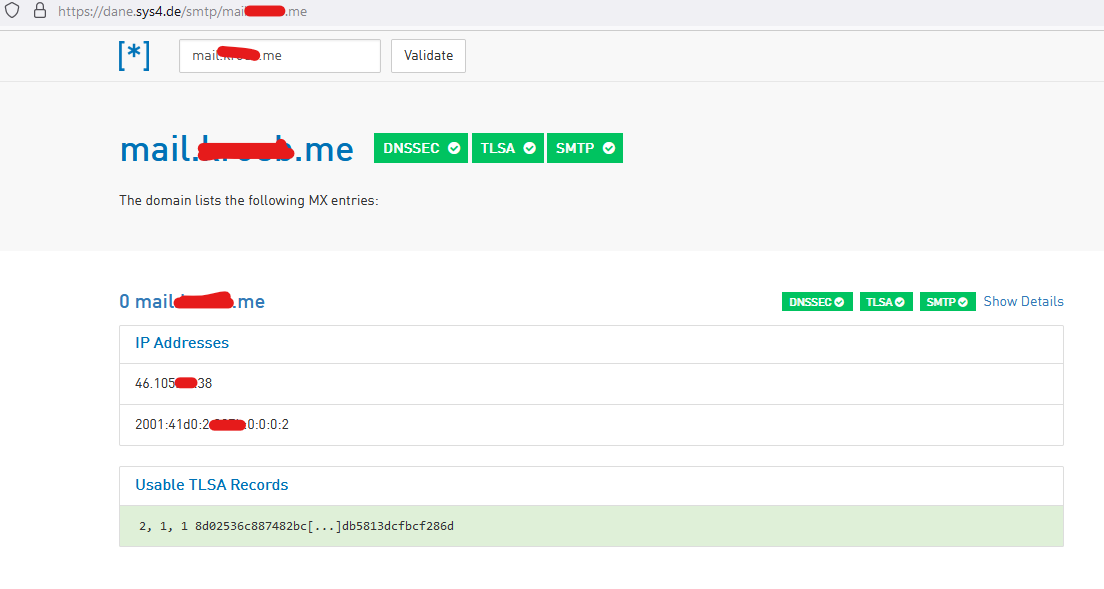
-
@Gertjan I am partly failing this test-site because I have my TLSA-record only on the domain which "carries" the actual mail-server and not on every domain with a mx-record...
-
@Gertjan the bad actors have created a lot of work for the rest of us. I guess for some this is job security.
@Gertjan said in How do I route outgoing email over WireGuard Tunnel?:
Get your mail server domain name certificate
Just to clarify is this for the mail server host that postfix is running and not the individual mail domains?
Can this be self signed and if not is Let's Encrypt adequate?
-
@Seeking-Sense said in How do I route outgoing email over WireGuard Tunnel?:
I guess for some this is job security.
You kidding ? I'm an financial accountant in a mid size hotel some where in France. I do change light bulbs, do reservations, and fool around with pfSense.
And yes, there are moment I have that feeling that I need to do something. Like understanding what this is, see subjects above, all about. I try to do things by doing them my selves. I've the Internet as documentation. Nothing you do isn't already done by some ine else.
So, go, and trial and error and learn and then you "do".@Seeking-Sense said in How do I route outgoing email over WireGuard Tunnel?:
Just to clarify is this for the mail server host that postfix is running and not the individual mail domains?
Example : I've a dedicated server, some where in a big data centre.
Added a dozen or so IPv4 (back then they were close to free, now these cost a fortune), and a zillion IPv6.
10 or so domain names. Some are used professionally, others are just for me to play with.
Every domain names has it's own wild card certificate from LE.
Every domain name uses its own IPv4 and own Ipv6 /64. (so if one mail box / domain gets bad, it will not hurt other domains / boxes )I use the certs for the web server of course (http is pretty dead these days)
But also for postfix, as postfix traffic is TLS these days (mail in the clear ois like http : that's not done anymore).
And why used self signed - self generated certs if you have the real ones for free, already on your server ? I have them, so I use them.And yes : my main.cf and master.cf is pretty big, and still I use a MySQL database full with tables for all the domain names, mail boxes etc.
All this works pretty well for the last ... 20 years or so.
-
@Bob-Dig said in How do I route outgoing email over WireGuard Tunnel?:
@Gertjan I am partly failing this test-site
Looked at it again, it is just buggy. First mx succeed, second fails. Makes no sense.
@Gertjan said in How do I route outgoing email over WireGuard Tunnel?:
big data centre.
Impressive.
What is a data centre?