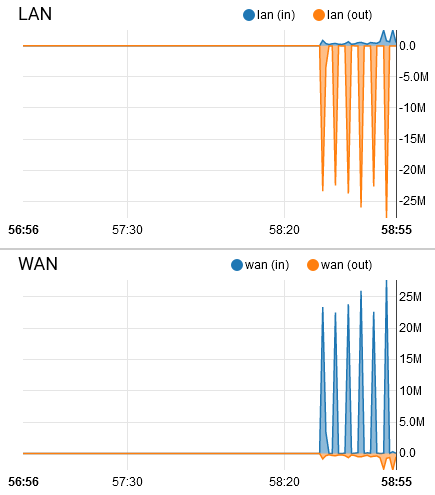
I have no idea whos causing this traffic....
-
@DaddyGo said in I have no idea whos causing this traffic....:
(even on a smaller network, it’s worth just keeping one in your desktop drawer for testing)
See my post Creating a "data tap". I also use a TP-Link TL-SG105E switch. I carry it in my computer bag and have also used it as a plain switch on occasion. Since I use a port based VLAN on it, instead of tags, it works fine.
-
@JKnott said in I have no idea whos causing this traffic....:
I also use a TP-Link TL-SG105E switch
Well, then we think on the same way

-
One crude option is watching the traffic graph live (Status -> Traffic Graph) and changing the interface to LAN. Depending on your network design, if you're not seeing any data, you may also have to change the filer to "Remote".
Another option is to install the ntopng package. In the ntopng settings menu, make sure that all of your LAN interfaces are tagged. Once in the ntopng webgui, click on the "Flows" menu across the top and you will see details (protocol, source, destination, throughput, etc) about each connection. From there I would sort by the "Actual Thpt" column so the connections generating the most bandwidth are at the top of the list.
Yet another option is installing the softflowd package and pointing it at a netflow collector like PRTG.
I would use ntopng. You should be able to find the offending device in a few min.
-
I think I saw similar forum thread from Belgian op not long ago. I am not sure if he already found the solution.
Wireshark is a great tool but if I may suggest, use QRadar CE (FREE) to analyze your live Pfsense logs.


Like today, I found a lot offensive IP addresses.
-
@AKEGEC said in I have no idea whos causing this traffic....:
QRadar CE
Thanks for the mention - I found something to play with this weekend ;)
But a SIEM is completely different animal than protocol analyzer like wireshark ;)
Normally your SIEM doesn't even accept flows, so you can't really see say your top talkers or who is talking to who, unless you logging allowed rules, etc.. And just seeing something was allowed doesn't show you how much data they are moving, etc.
But it does look interesting - so think will fire up the CE.. 50 events a second should be pretty reasonable.. for what your home setup would see.
-
You can do remote tcpdump on pfSense , and ssh tunnel it to wireshark , using these steps.
Assumptions: ----------------- pfSense vers : 2.4.5-p1 Username on both linux & pfSense : pfuser Firewall hostname : pf-fw-01 Interface to sniff on : igb1.100Install / Prepare Steps: ------------------------------ As admin on pfSense install pkg install security/sudo As admin on pfSense (syyshhh) ------------------------------- 1: visudo , add : %admins ALL=(ALL) NOPASSWD: ALL 2: vi /etc/groups , make sure your user is member of admins.As root on local linux (Wireshark display machine) --------------------------------------------------- 3: ssh-keygen 4: ssh-copy-id pfuser@pf-fw-01Use wireshark as frontend for pfSense tcpdump ... aka. Start a sniff ---------------------------------------------------------------------- As root on local linux machine (to begin wireshark "remote" snif and tunnel data via ssh) - 'not port 22' (don't match ssh, used for tunneling data) ssh pfuser@pf-fw-01 sudo tcpdump -iigb1.100 -U -s0 -w - 'not port 22' | wireshark -k -i -These are some notes I took like 2 years back , on 2.4-RC
I'm not sure if the "ssh keygen" steps (3-4) in the linux machine, makes sense to do as root. I might have done that as pfuser
But i just tried a remote wireshark , and it still works in 2.4.5-p1
if-name had to be changed from -iigb1_vlan100 to -iigb1.100Edit:
Watch out .. This will load your ssh connection hard
Don't sniff a loaded 1Gb if , via a remote 20Mb ssh
Use a pfSense local pcap dump instead , or make a more specific tcp dump match on the pfSense
/Bingo -
@AKEGEC said in I have no idea whos causing this traffic....:
Wireshark is a great tool but if I may suggest, use QRadar CE (FREE) to analyze your live Pfsense logs.
@AKEGEC - I haven't met this stuff yet, thanks

I agree with @johnpoz, but it seems like a really good little tool for logging for home setup.
This is not a protocol analyzer, currently Wireshark + Nmap I think meets the needs of every administrator.
I will mention, who might be interested in the theme,.... the new Nmap 7.91 and the big star Npcap 1.00 available. A good Npcap 1.00 was already needed.
https://seclists.org/nmap-announce/2020/0In any case, it is much better than the PRTG, ........- mentioned by @marvosa, which as we know is free for only up to 100 sensors, nor is it a protocol analyzer.
We prefer this rather........:
https://securityonionsolutions.com/software
(for loging and static PCAP analysis) -
I love these statements ;)
"QRadar that is low memory, low EPS"
But then
Minimum System Requirements: 8 GB RAM (10 GB is recommended) 250 GB free disk space 2 CPU cores (6 cores is recommended)Thought I might throw this up on my nas.. Not with those requirements..
-
@johnpoz said in I have no idea whos causing this traffic....:
"QRadar that is low memory, low EPS"
Yes, you need a separate power machine for the end - or we misunderstand the concept of low.
I can’t even download it yet, I want to play with it a bit.BUT

IBM, did not say this when I provided my email address when registering
it's good to have a gmail address used for this purpose, hahahaha
for I would be in their net....++edit:
what a junk attempt

-
@johnpoz said in I have no idea whos causing this traffic....:
I love these statements ;)
"QRadar that is low memory, low EPS"
But then
Minimum System Requirements: 8 GB RAM (10 GB is recommended) 250 GB free disk space 2 CPU cores (6 cores is recommended)Thought I might throw this up on my nas.. Not with those requirements..
If you don't have a power server then you could use AWS or Azure to install your Qradar and send your pfsense log there. ;)
-
@AKEGEC do you have a content extension that works with 7.3.3 CE version? I have installed the Netgate pfSense DSM but I am experiencing problems while installing Polo's pfSense content extension.