How to detect a cyber attack
-
PfSense 2.4.4
Antivirus installed (Clama)In the last days I notice my WAN´s are strange. I did not detect a cause.
I suspect that i am sufferring an cyber attack.
Is there some "sign" in pfSense that can help me knowing if it is really an attack?When I reset "states" everything go okay again during some hours.
-
Not enough info. Define 'strange'. And no, there is no magic "YOU'RE UNDER ATTACK!!" alert or anything. Do you have any port forwards that might be external targets?
-
@KOM said in How to detect a cyber attack:
Not enough info. Define 'strange'. And no, there is no magic "YOU'RE UNDER ATTACK!!" alert or anything. Do you have any port forwards that might be external targets?
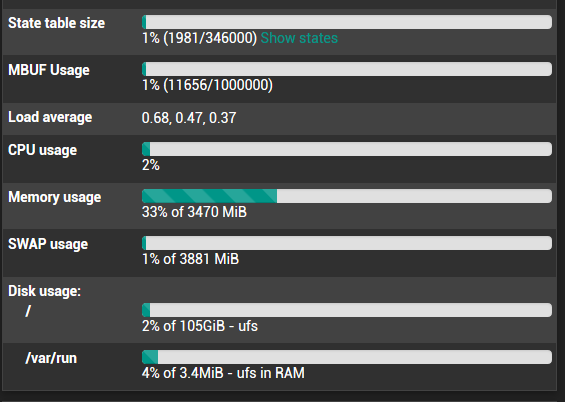
Strange: Memory Usage up to 80%
Traffic Very slow
Sometimes it seems DNS does not work
When I reset States everything starts working again for some minutesPort forwards: yes.
- Some ports are allowed WTS and are blocked by a rule to non known external IP
- Some ports are allowed UltraVNC and are open to any external IP, but only when I am exceuting UltraVNC.
I was not suposed to be a magic "YOU'RE UNDER ATTACK!!". I supose there is some "hint/tip" or evidence as log´s or something like that.
-
What does the traffic graph show while this effect is happening? Is your WAN being pounded with a ton of traffic aka a DoS attack?
What packages are you running? Snort & Suricata can cause problems on your LAN if you aren't careful, for instance.
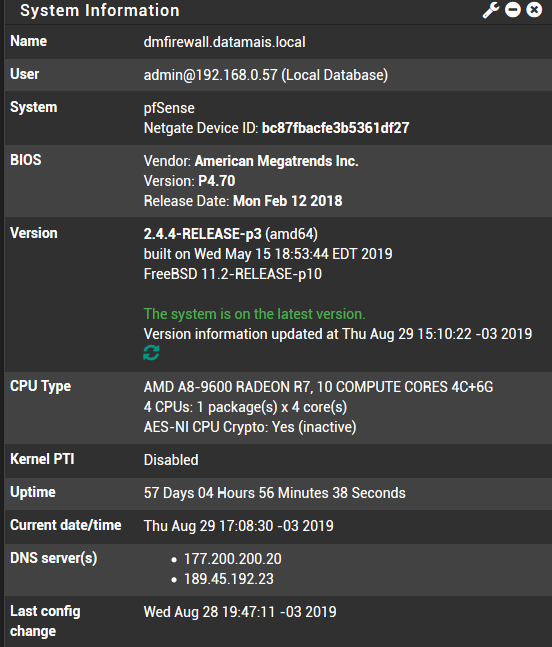
On the dashboard, in the System Info widget, what do you have for State table size?
-
@KOM said in How to detect a cyber attack:
What does the traffic graph show while this effect is happening? Is your WAN being pounded with a ton of traffic aka a DoS attack?
What packages are you running? Snort & Suricata can cause problems on your LAN if you aren't careful, for instance.
On the dashboard, in the System Info widget, what do you have for State table size?- Traffic graph semms normal
3)
-
Hmmm, nothing unusual there. Squid can easily suck up a ton of RAM, and your other problem might be related to your ISP and their network. If you look at Status - Monitoring, do you have any significant packet loss?
-
@KOM I was not monitoring.
Now I will use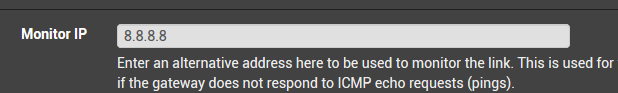
And I will wait to see what happens.
-
@hugoeyng said in How to detect a cyber attack:
@KOM I was not monitoring.
Now I will use
And I will wait to see what happens.
You may want to use something other than 8.8.8.8. You will get false positives using Google's DNS servers. They will drop your traffic.
-
I believe it's recommended to use the gateway provided by your ISP as the monitor IP, since it's the first router/hop before your traffic hits the actual internet. If that's down, it truly means your connection is DOWN.
Jeff
-
It depends. Sometimes you want to know that the WAN can actually reach the internet, not just the ISP gateway.
-
@Derelict Instead Google DNS or ISP DNS what IP could I use to monitor? Any suggestion?
-
Perhaps one of your ISPs core routers. Do a traceroute somewhere and see what the second or third hop is.
-
I've never seen an issue using 8.8.8.8 personally.
The fact that you have some SWAP usage shown in that screenshot shows that at some point you exhausted the RAM. That can make things go waaaay slower.
Check the Status > Monitoring graphs for memory usage. Does it peak when you see these incidents?Steve
-
@stephenw10 said in How to detect a cyber attack:
I've never seen an issue using 8.8.8.8 personally.
Yeah I like to use 8.8.8.8, 8.8.4.4 and 1.1.1.1 for monitoring too.
-Rico
-
@KOM Great!
-
-
I never heard of Google deliberately dropping ICMP traffic to their DNS Servers and personally I never had any issues with it.
WANGW is using 8.8.8.8 atm.-Rico
-
Monitoring any ISP router does not really show a reliable route to the Internet.
Your ISP could have any routing/peering issue, even if their (core) router is perfectly reachable from your side.-Rico
-
It shows you if there is a problem between you and your ISP. Anything past that is out of your control. The whole point of the thing is to be a gateway monitor, not a 5-hops-away monitor. The farther away you monitor, the more likely you will get a false positive of some sort, and I wouldn't want my gateway going down because there is a routing problem many hops away from me.
-
On the monitor IP topic, I agree with @Rico and @stephenw10. I have not had issue so far with google DNS. In fact I switched to Google DNS because I suddenly had issues with my ISP's (third hop router). After months of working fine, we had power failures in the area which I suspect also caused issues with that route on the ISP's network. My gateway was marked as down when it wasn't. Switched to 8.8.8.8 and it's been good since then. Is it a perfect solution? No. Will this happen to you? Probably not, but using a device IP on a specific route on the ISP's network to me seems like trouble. If that route goes down like in my case, the traffic will get rerouted and still reach where it needs to go on the web. But that can't happen if my gateway is marked as down and monitoring action is enabled. Ideally, I would like to be able to put in multiple monitor IPs, so if one is not responding another one could.