Port Forward does not work..
-
@Bob-Dig
It is on the default system, I tried with NAT + Proxy activated and with Pure Nat, it doesn't work.
-
@NogBadTheBad said in Port Forward does not work..:
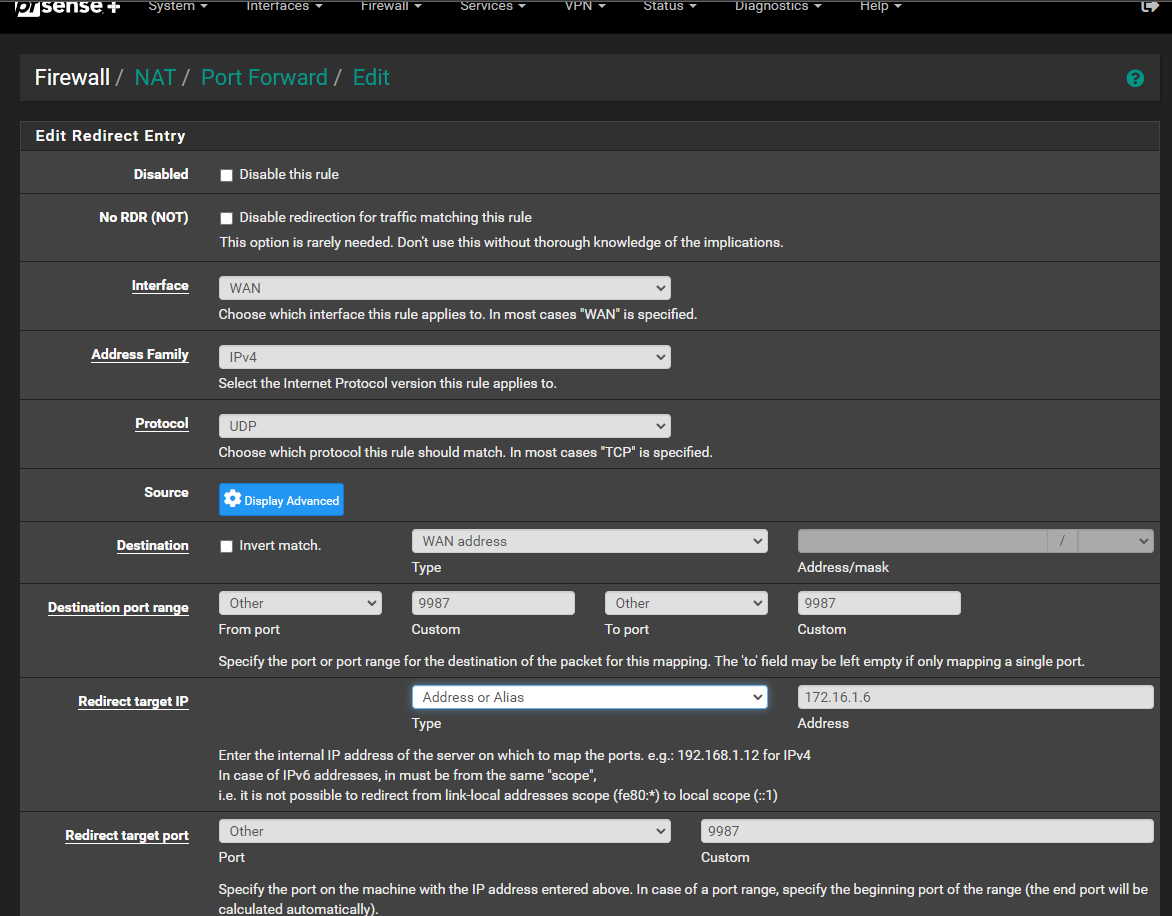
change the firewall destination rule to WAN address.
No, when forwarding traffic, the destination in the firewall rule has to be the backend host. It's also be generated automatically this way if applicable.
@root1ng
The rule doesn't show up any hits. So check out if the packets even arrive on your WAN.
You can use packets capture to do this.Is there a router in front of pfSense.
@root1ng said in Port Forward does not work..:
I still can't connect with the public IP but only with the local one.
Or do you only want local devices to use the WAN address for whatever reason?
-
@viragomann said in Port Forward does not work..:
The rule doesn't show up any hits. So check out if the packets even arrive on your WAN.
You can use packets capture to do this.Is there a router in front of pfSense.
I don't know how to use Packet Capture, and in front of pfSense there is only the ONT, but it has nothing to do with what happens after it.
It is only a fiber to RJ45 converter.@viragomann said in Port Forward does not work..:
Or do you only want local devices to use the WAN address for whatever reason?
It's a public server and that's why I need it to be accessed with the wan address.
-
@root1ng said in Port Forward does not work..:
It's a public server and that's why I need it to be accessed with the wan address.
And what's the recent issue you're on? Accessing it from outside or from inside your network?
For inside access you should rather use its local IP and a DNS host override for the public FQDN.
-
@viragomann said in Port Forward does not work..:
And what's the recent issue you're on? Accessing it from outside or from inside your network?
For inside access you should rather use its local IP and a DNS host override for the public FQDN.
I can't access it from the outside, only from the inside with a private local IP, not the public one.
-
@root1ng
So I assume, you're not sure, if the desired traffic is even forwarded to your public IP. It could be blocked by the ISP.
BTW, do you even have a real public IP? And if, is it assigned to pfSense WAN interface (ONT in bridge mode)?If yes, sniff the WAN traffic to ensure, that the traffic is even forward to pfSense.
Diagnostic > Packet Capture
Select the WAN interface
In the "untagged filter" section at port number select "all off" and enter "9987|30033". This capture both.
Hit start and try to access your server from the internet. -
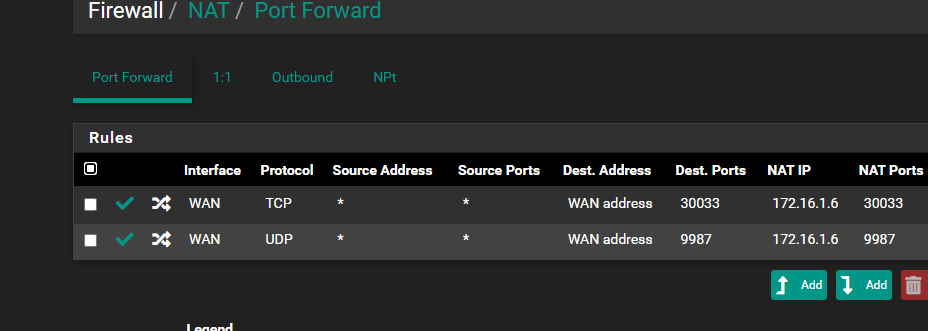
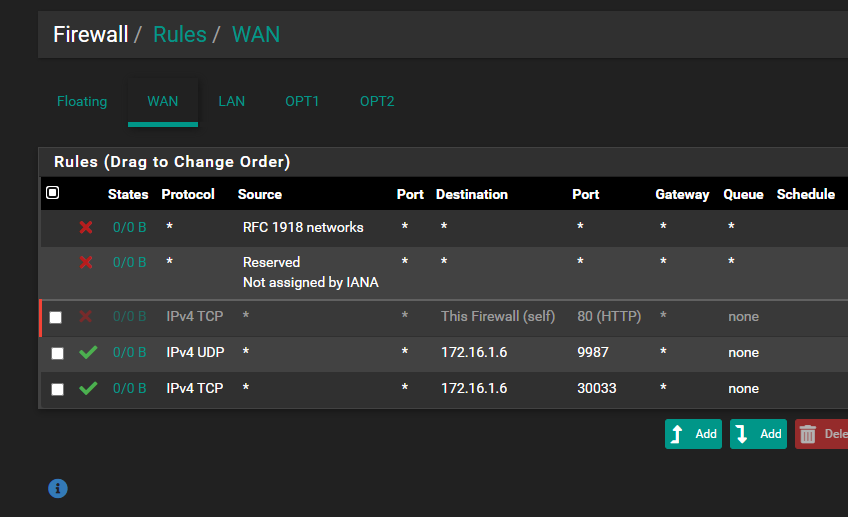
@root1ng I don't see any hits on either of those rules that allow for your port forwards to port 9987 and 30033
First step in troubleshooting a port forward or any wan side firewall rule is validate the traffic actually gets to pfsense, go to like can you see me . org and send some traffic. Be it you allow it or forward it or not.. You should see that traffic in your packet capture.
For example just sent some traffic to port 9987 like your forward, as you can see from packet capture on my wan pfsense actually sees this traffic.
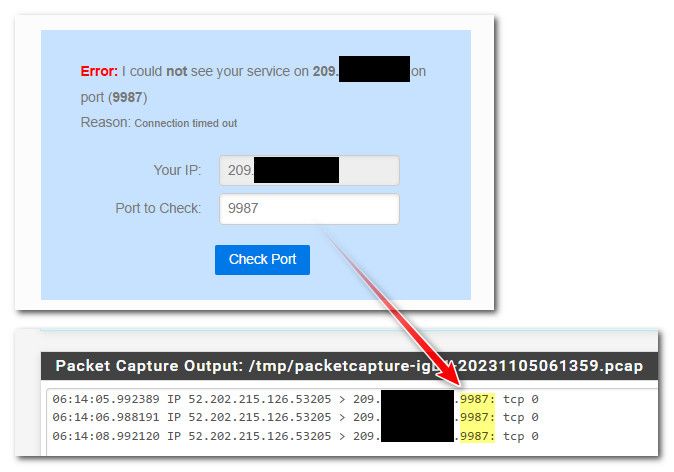
If pfsense never sees the traffic no amount of firewall rules or forwards would ever work.
-
@johnpoz said in Port Forward does not work..:
If pfsense never sees the traffic no amount of firewall rules or forwards would ever work.
For him it is UDP but right. For testing do something with TCP.
-
@Bob-Dig Oops forgot about the order

-
@Bob-Dig said in Port Forward does not work..:
For testing do something with TCP.
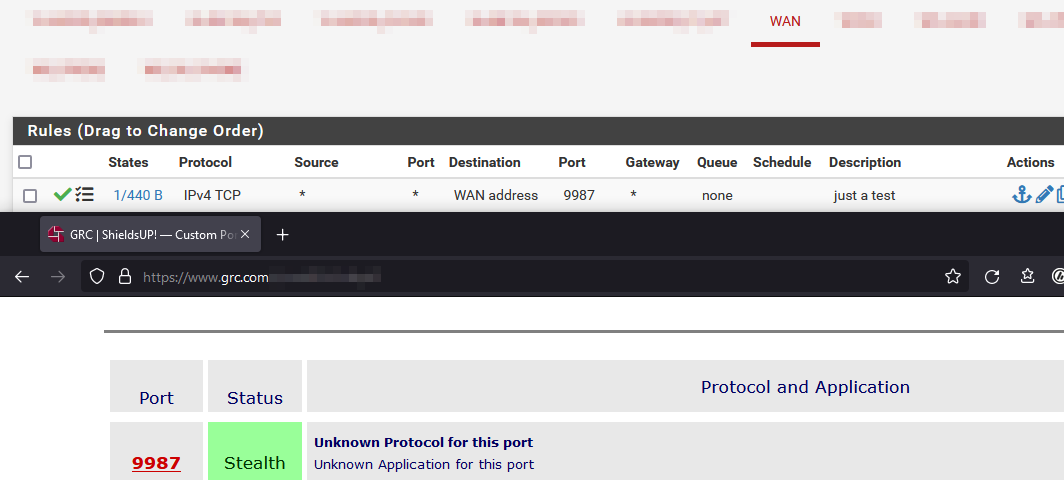
Because it is more easy I have to add.

For instance, while it is showing as stealth because there is no service running on that port, I still see that the rule was triggered.
-
@johnpoz said in Port Forward does not work..:
@root1ng I don't see any hits on either of those rules that allow for your port forwards to port 9987 and 30033
First step in troubleshooting a port forward or any wan side firewall rule is validate the traffic actually gets to pfsense, go to like can you see me . org and send some traffic. Be it you allow it or forward it or not.. You should see that traffic in your packet capture.
For example just sent some traffic to port 9987 like your forward, as you can see from packet capture on my wan pfsense actually sees this traffic.
If pfsense never sees the traffic no amount of firewall rules or forwards would ever work.
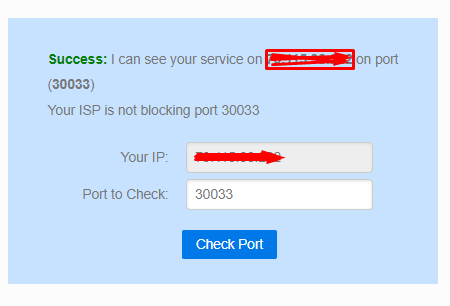
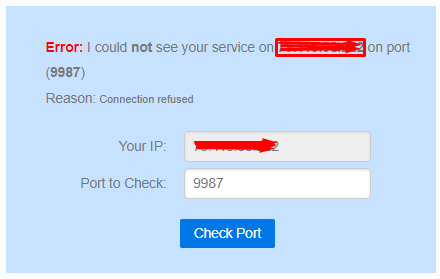
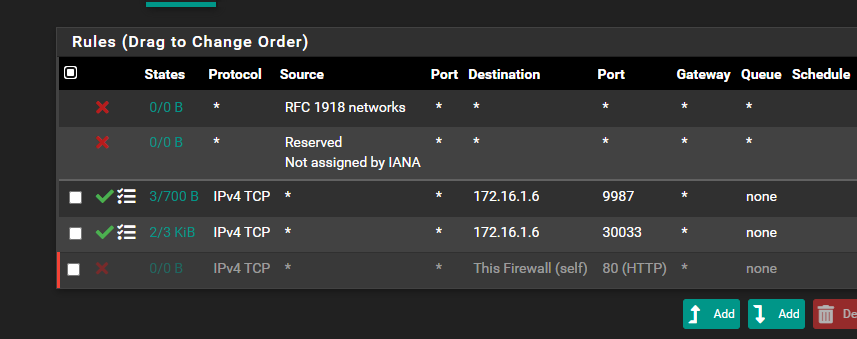
30033 TCP seems to work, 9987 UDP doesn't and I don't understand why, all ports are open from ISP
-
@root1ng
The port checker might only be able to do TCP checks. -
-
@Bob-Dig said in Port Forward does not work..:
That does look good
Yes, but the main one is 9987 .. and for now it still doesn't work.
-
@root1ng said in Port Forward does not work..:
Yes, but the main one is 9987 .. and for now it still doesn't work.
Maybe your proxmox Firewall is blocking UDP?
-
@Bob-Dig said in Port Forward does not work..:
Maybe your proxmox Firewall is blocking UDP?
All firewalls are disabled.. tell me where to check and I'll come back
-
@root1ng said in Port Forward does not work..:
Yes, but the main one is 9987 .. and for now it still doesn't work.
As long as there is no service listening on this port at TCP, the access won't succeed naturally.
Your backend is listening at UDP 9987 and UDP probably cannot be probed with the port checker. -
@viragomann said in Port Forward does not work..:
As long as there is no service listening on this port at TCP, the access won't succeed naturally.
Your backend is listening at UDP 9987 and UDP probably cannot be probed with the port checker.I changed from UDP to TCP and I still can't access it with the port checker, I still get a timeout.
-
@root1ng
On the backend? And does it work from inside with TCP? -
@viragomann said in Port Forward does not work..:
@root1ng
On the backend? And does it work from inside with TCP?Not working ..