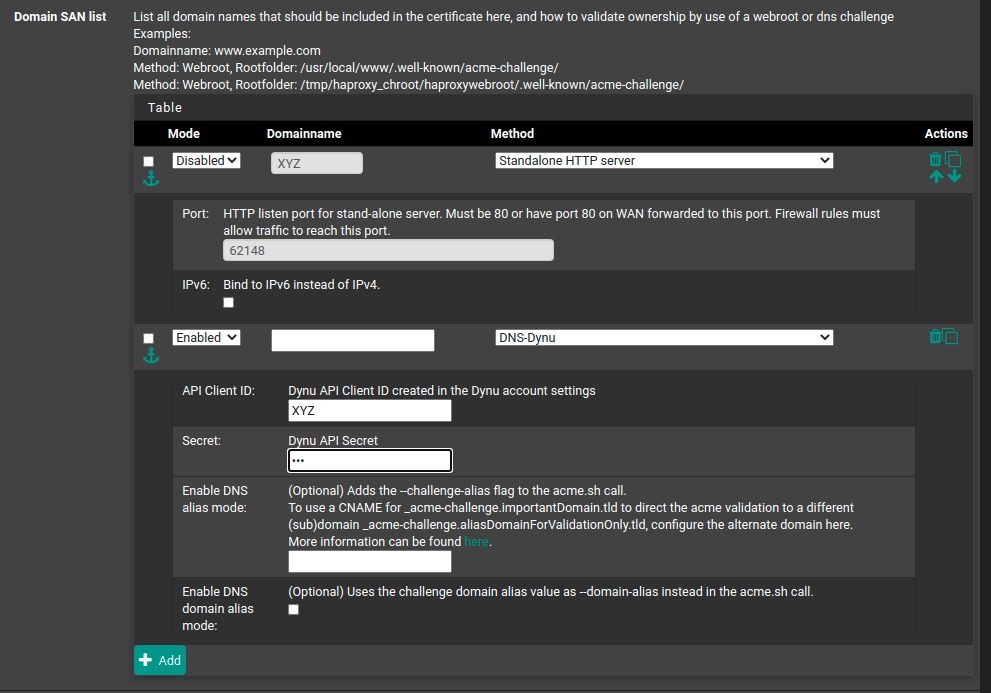
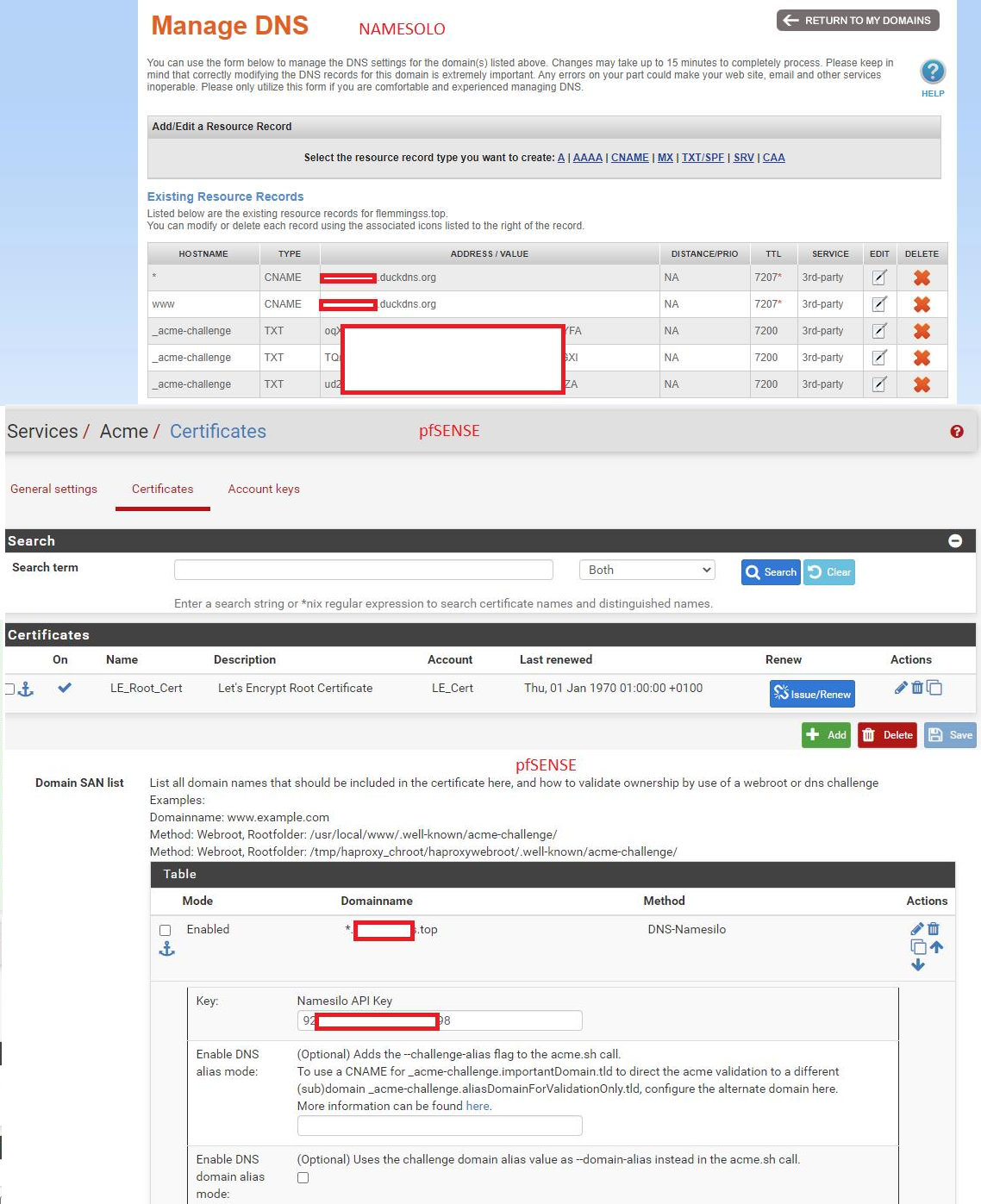
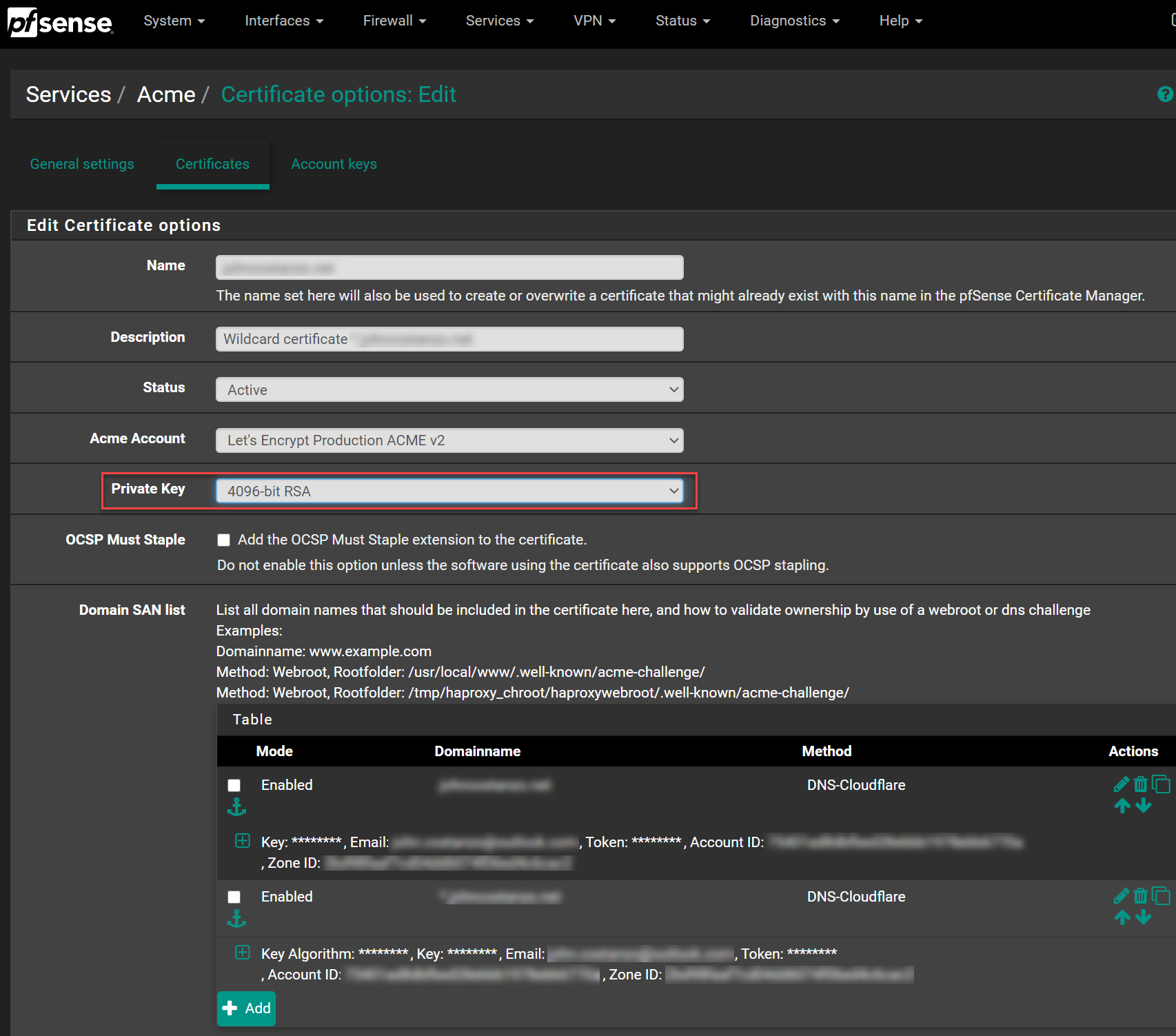
@karlisp said in Copy certificate to remote server:
but cant seem to find how to generate private and public ssh key that will be used to communication between firewall and server
Strange
Because that one is also needed to access pfSense using it's SSH access.
The ssh password method is meant to be used only ones, to be forbidden afterwards, with :
[image: 1597243965394-371e3693-64a5-4bc7-8f69-0c7905ea0b6d-image.png]
See the pfsense manual, or about a million other sources on the net about how to create them, where what to place what etc.
This info is valid for everything that is accessible with "ssh".
Use a tool of your choice to create a (the) key(s) and cut and pasted it here :
[image: 1597244940603-a751ab92-5a7a-4a3f-afcc-2002aaa12d16-image.png]
( the admin user settings of pfSense, at the bottom of the page )
About the scripts : many have already made something up, using some shell script.
So many OS's exists, like the desktop ones, and OS's for devises likes printers, NAS's etc etc etc.
It boils down as copying a file often the network - putting the file 'on the right place' - and signalling / restarting the services that uses these files == the new certs.
For myself : when acme did it's job, every 60 days, I receive a mail.
I added to the bottom of the mail :
"As an admin, do your jobs, and extract these 2 files from pfSense, to put them in the 2 NAS's et 2 network printers."
Not a bad thing, actually, as it takes 5 minutes, and I'm paid to do ^^
I have a "root" access for my Syno NAS's, but I do not have such a ssh access for the printers, so the GUI way is the only way anyway.