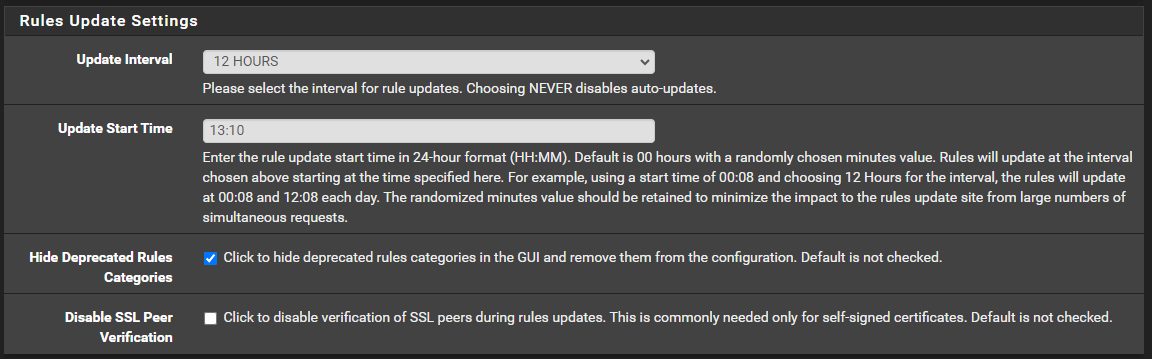
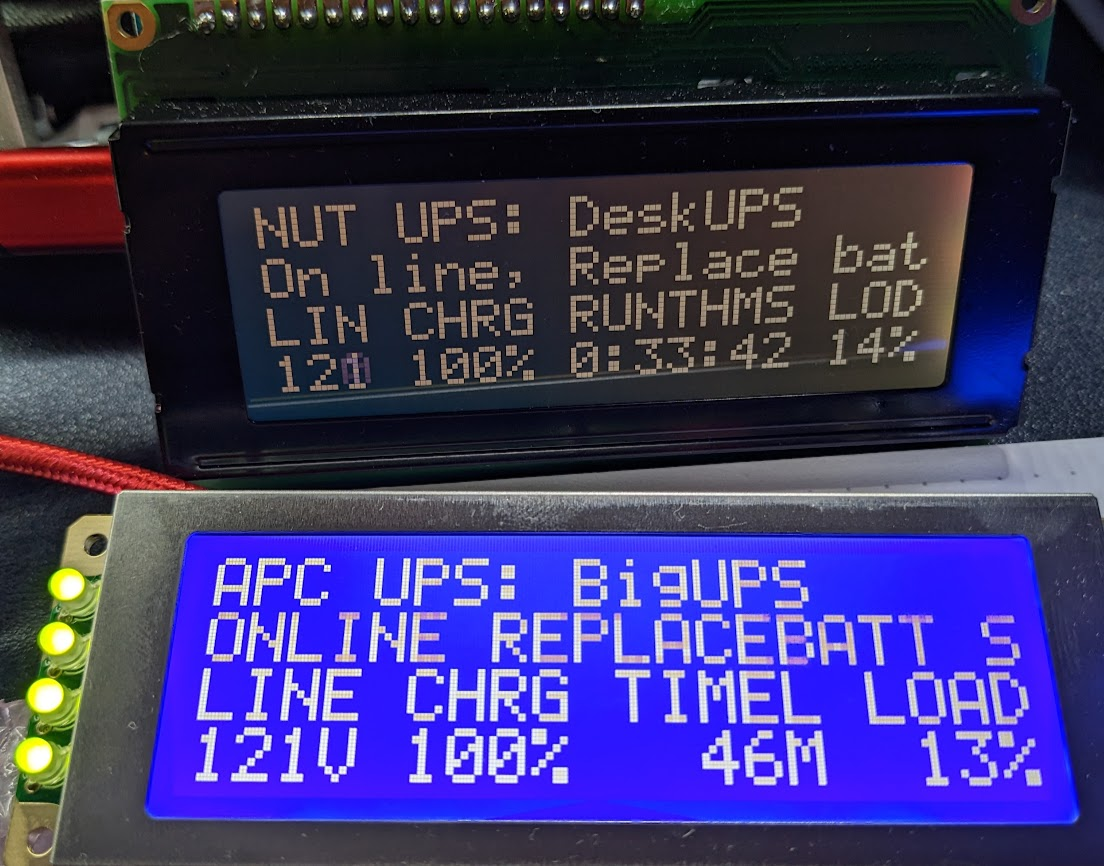
@jimp was kind enough to update the LCDProc package to include a NTP server screen georou @ GitHub originally created and we updated. Current package is 0.11.5. There is a pending update to 0.11.5_1 (screens below) that improves the display of PPS, GPS, vs GPS+PPS in certain edge cases.
https://github.com/pfsense/FreeBSD-ports/commit/b3a3a4bf28ad8a50211b6775ed20011097ceeef9
If you have a PPS source, it will display either the number of satellites (GPS) or stability value (PPS).
Otherwise, it will display the Active Peer Server IP address.
Notes: I am by no means a NTPD algorithm expert, but I noticed if a source is marked as a valid PPS Peer "o", NTPD uses that to sync and serve time to clients regardless if there a separate Active Peer "*" used for time data. If a GPS is being used for both a PPS Peer "o"and source of time data, it will be marked as PPS Peer "o" and there will be no other Active Peers "*" marked (see screen cap below). The NTP Widget seems to display the Active Peer "*" even when the PPS Peer "o" is actually being used to sync and serve time to clients. Which source is actually served to clients can be confirmed with "ntpq -c sysinfo". If you want to see the stability value when using a GPS with PPS, you can simply set the Clock ID of the GPS source to "PPS". I intentionally did not include seconds on the display since even with the LCDProc Refresh Frequency set to 1 second, time will jump multiple seconds with each screen refresh. Not sure if there is another mechanism that would improve the refresh rate of the first row to eliminate increments of multiple seconds.
Feedback welcome, subject to the limitations noted above.
I happen to be using a Garmin 16X (PPS Only) and 18X (GPS+PPS). NTPD only supports one PPS source at a time, thus marks the second as False Ticker "x"
https://github.com/elvisimprsntr/pfsense-ntp-gps. (WIP)
[image: 1691501128729-screenshot-2023-08-08-at-9.25.04-am-resized.png]
[image: 1691499425902-lcdgps.png]
[image: 1691499425822-lcdpps.png]
[image: 1691499425730-lcdip.png]