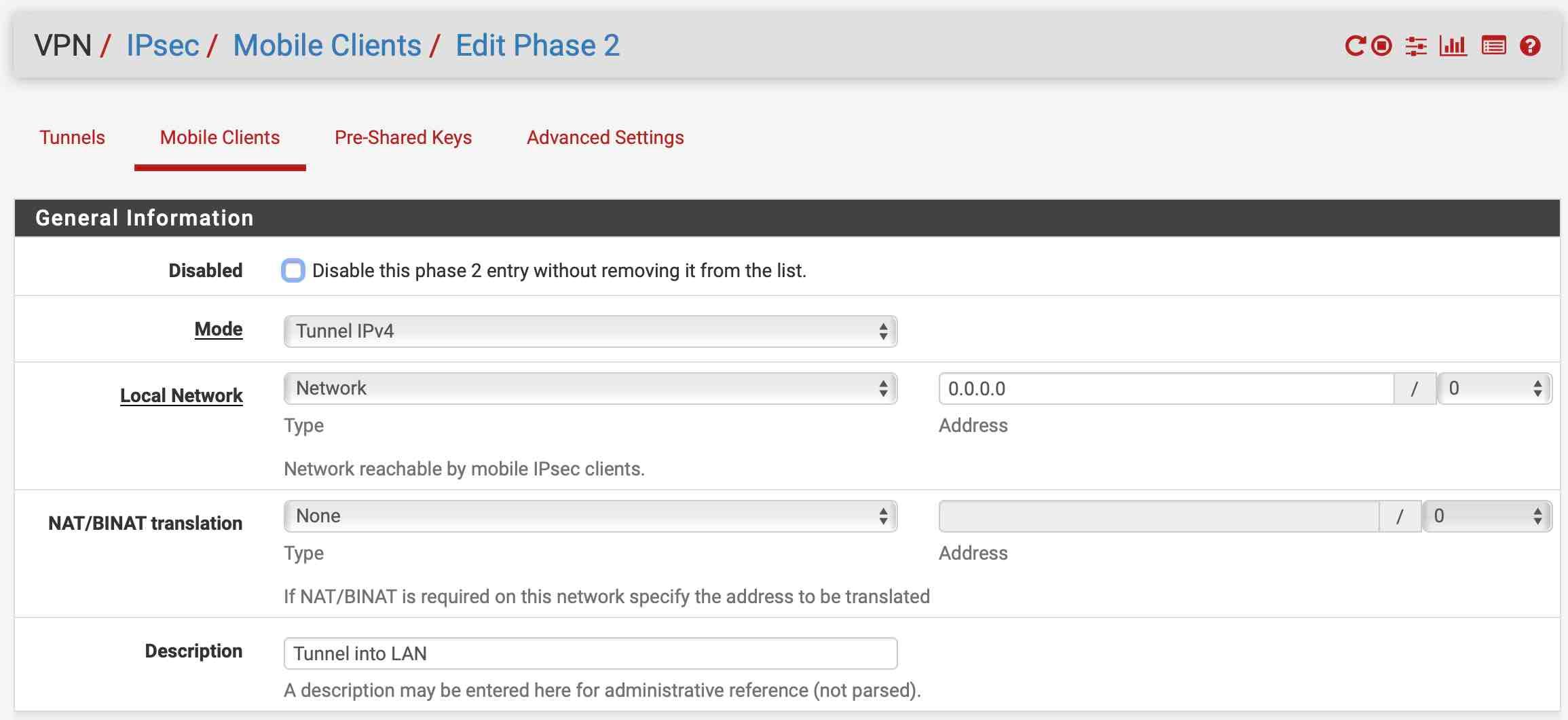
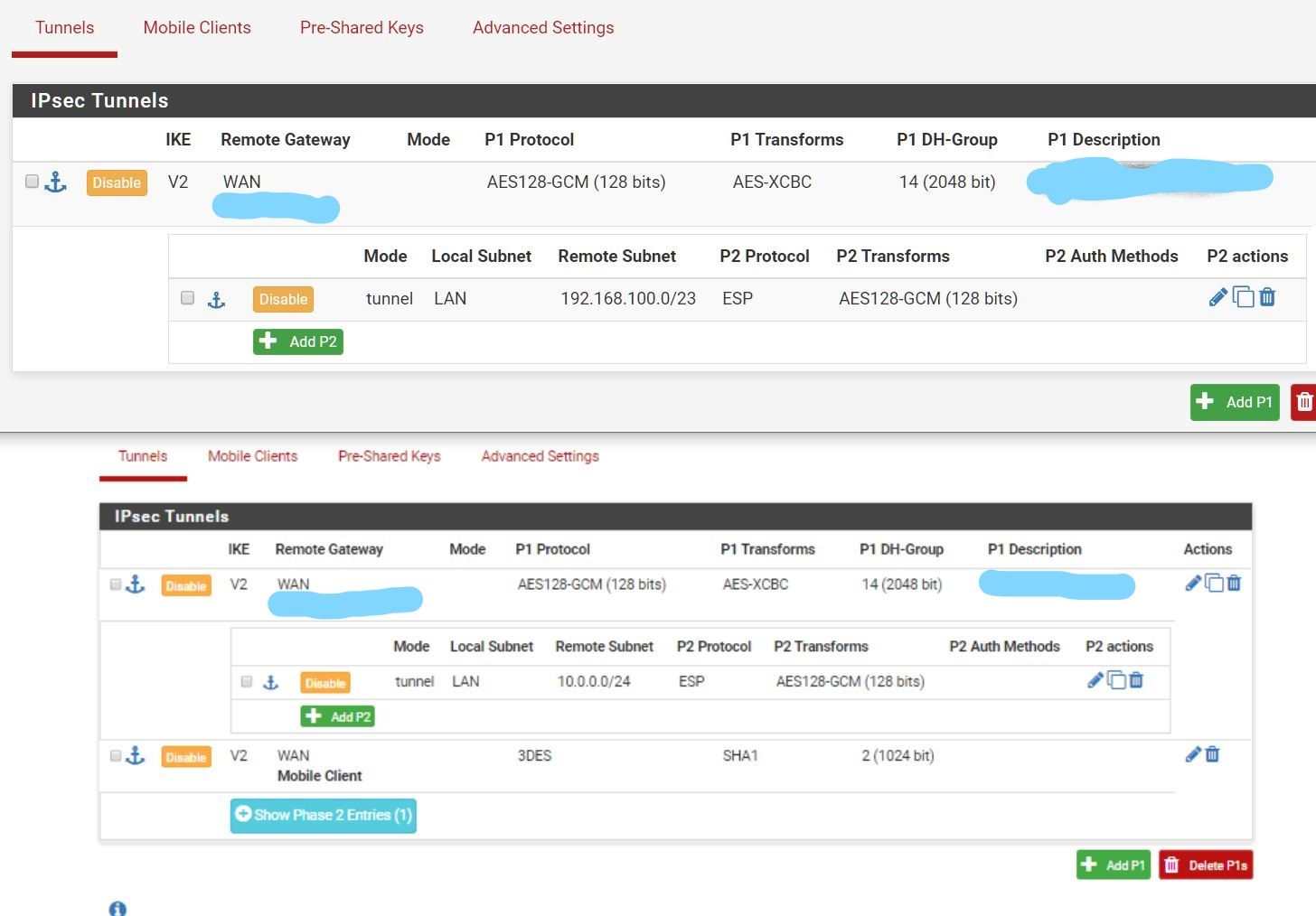
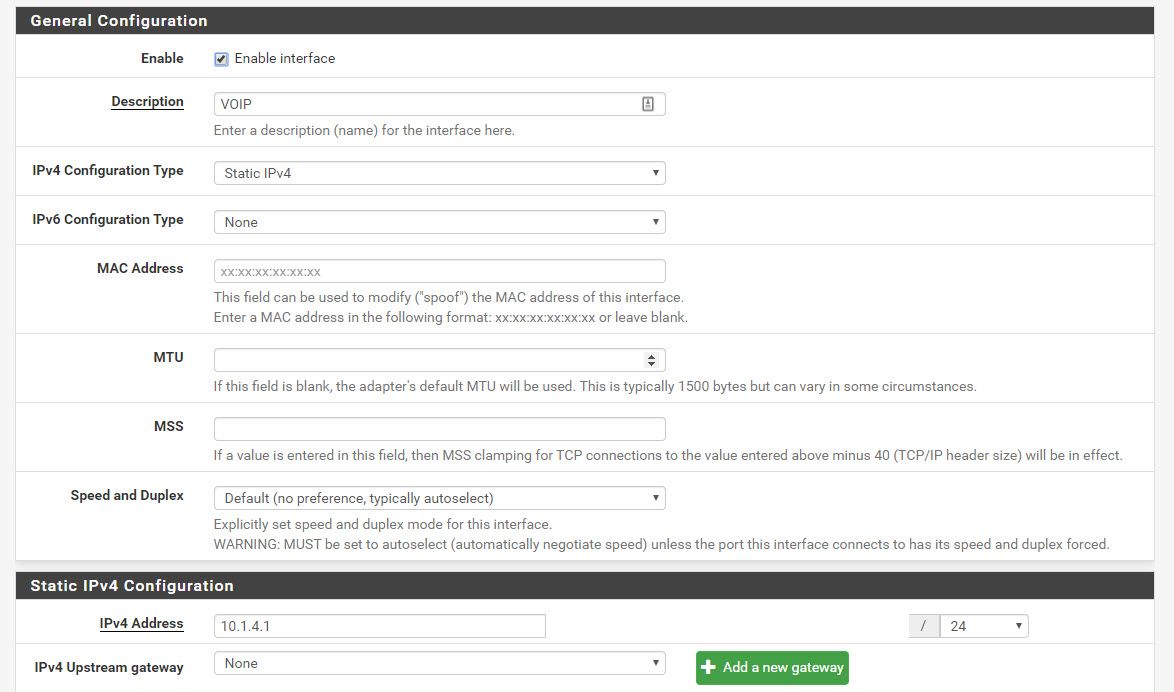
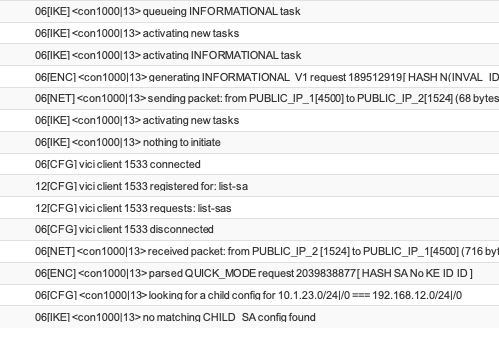
Update:
I followed this article and set up VPN: link
Now, i have a VPN that wotks with my Android phone, but my Windows 10 PC cant connect to it.
The Windows 10 log says 788 error when i try to connect to the server.
The ipsec log:
Dec 23 18:34:38 charon 07[NET] <5> received packet: from 2a01:36d:1000:2bbe::1003[500] to 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79[500] (368 bytes)
Dec 23 18:34:38 charon 07[ENC] <5> parsed ID_PROT request 0 [ SA V V V V V V ]
Dec 23 18:34:38 charon 07[CFG] <5> looking for an IKEv1 config for 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79...2a01:36d:1000:2bbe::1003
Dec 23 18:34:38 charon 07[CFG] <5> candidate: %any...%any, prio 24
Dec 23 18:34:38 charon 07[CFG] <5> found matching ike config: %any...%any with prio 24
Dec 23 18:34:38 charon 07[ENC] <5> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:01
Dec 23 18:34:38 charon 07[IKE] <5> received MS NT5 ISAKMPOAKLEY vendor ID
Dec 23 18:34:38 charon 07[IKE] <5> received FRAGMENTATION vendor ID
Dec 23 18:34:38 charon 07[ENC] <5> received unknown vendor ID: fb:1d:e3f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
Dec 23 18:34:38 charon 07[ENC] <5> received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
Dec 23 18:34:38 charon 07[ENC] <5> received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
Dec 23 18:34:38 charon 07[IKE] <5> 2a01:36d:1000:2bbe::1003 is initiating a Main Mode IKE_SA
Dec 23 18:34:38 charon 07[IKE] <5> IKE_SA (unnamed)[5] state change: CREATED => CONNECTING
Dec 23 18:34:38 charon 07[CFG] <5> selecting proposal:
Dec 23 18:34:38 charon 07[CFG] <5> proposal matches
Dec 23 18:34:38 charon 07[CFG] <5> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_256, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Dec 23 18:34:38 charon 07[CFG] <5> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Dec 23 18:34:38 charon 07[CFG] <5> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/ECP_384
Dec 23 18:34:38 charon 07[IKE] <5> sending XAuth vendor ID
Dec 23 18:34:38 charon 07[IKE] <5> sending DPD vendor ID
Dec 23 18:34:38 charon 07[IKE] <5> sending FRAGMENTATION vendor ID
Dec 23 18:34:38 charon 07[ENC] <5> generating ID_PROT response 0 [ SA V V V ]
Dec 23 18:34:38 charon 07[NET] <5> sending packet: from 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79[500] to 2a01:36d:1000:2bbe::1003[500] (140 bytes)
Dec 23 18:34:38 charon 07[NET] <5> received packet: from 2a01:36d:1000:2bbe::1003[500] to 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79[500] (180 bytes)
Dec 23 18:34:38 charon 07[ENC] <5> parsed ID_PROT request 0 [ KE No ]
Dec 23 18:34:38 charon 07[CFG] <5> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Dec 23 18:34:38 charon 07[ENC] <5> generating ID_PROT response 0 [ KE No ]
Dec 23 18:34:38 charon 07[NET] <5> sending packet: from 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79[500] to 2a01:36d:1000:2bbe::1003[500] (164 bytes)
Dec 23 18:34:38 charon 07[NET] <5> received packet: from 2a01:36d:1000:2bbe::1003[500] to 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79[500] (92 bytes)
Dec 23 18:34:38 charon 07[ENC] <5> parsed ID_PROT request 0 [ ID HASH ]
Dec 23 18:34:38 charon 07[CFG] <5> looking for pre-shared key peer configs matching 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79...2a01:36d:1000:2bbe::1003[2a01:36d:1000:2bbe::1003]
Dec 23 18:34:38 charon 07[CFG] <5> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Dec 23 18:34:38 charon 07[IKE] <5> found 1 matching config, but none allows pre-shared key authentication using Main Mode
Dec 23 18:34:38 charon 07[IKE] <5> queueing INFORMATIONAL task
Dec 23 18:34:38 charon 07[IKE] <5> activating new tasks
Dec 23 18:34:38 charon 07[IKE] <5> activating INFORMATIONAL task
Dec 23 18:34:38 charon 07[ENC] <5> generating INFORMATIONAL_V1 request 3049540974 [ HASH N(AUTH_FAILED) ]
Dec 23 18:34:38 charon 07[NET] <5> sending packet: from 2a01:36c:1000:2bbe:6e3b:e5ff:fe0a:4d79[500] to 2a01:36d:1000:2bbe::1003[500] (92 bytes)
Dec 23 18:34:38 charon 07[IKE] <5> IKE_SA (unnamed)[5] state change: CONNECTING => DESTROYING