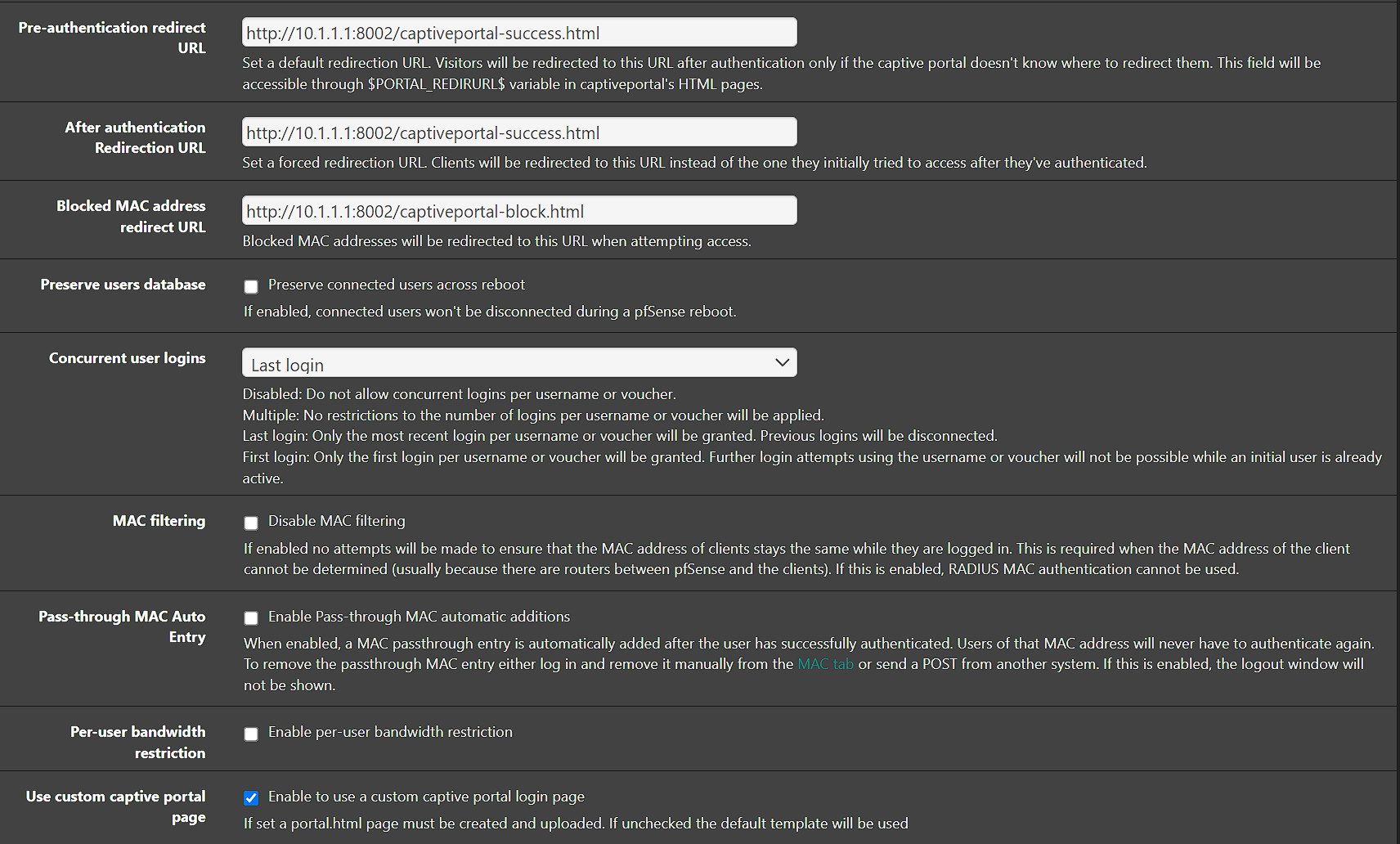
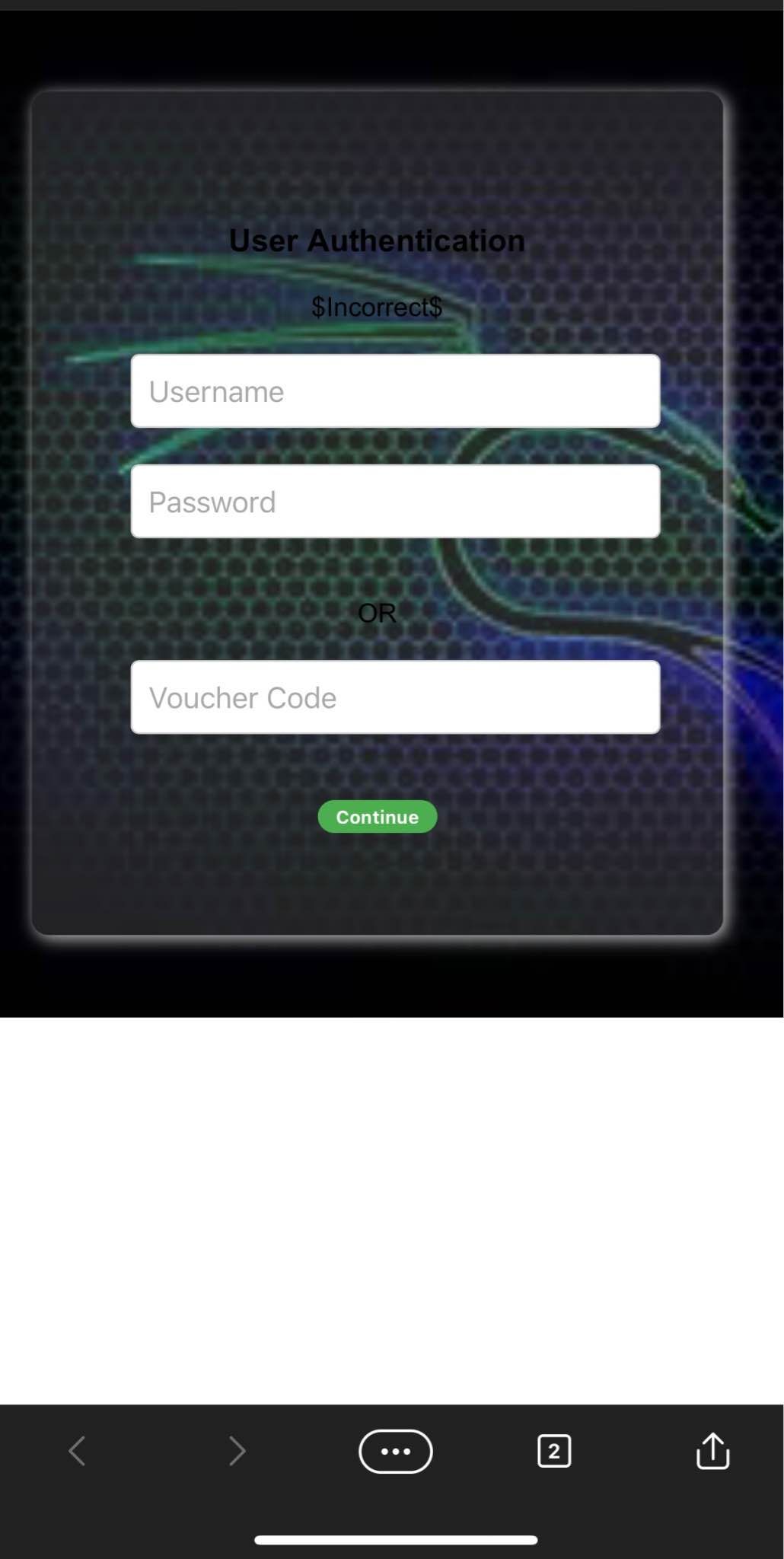
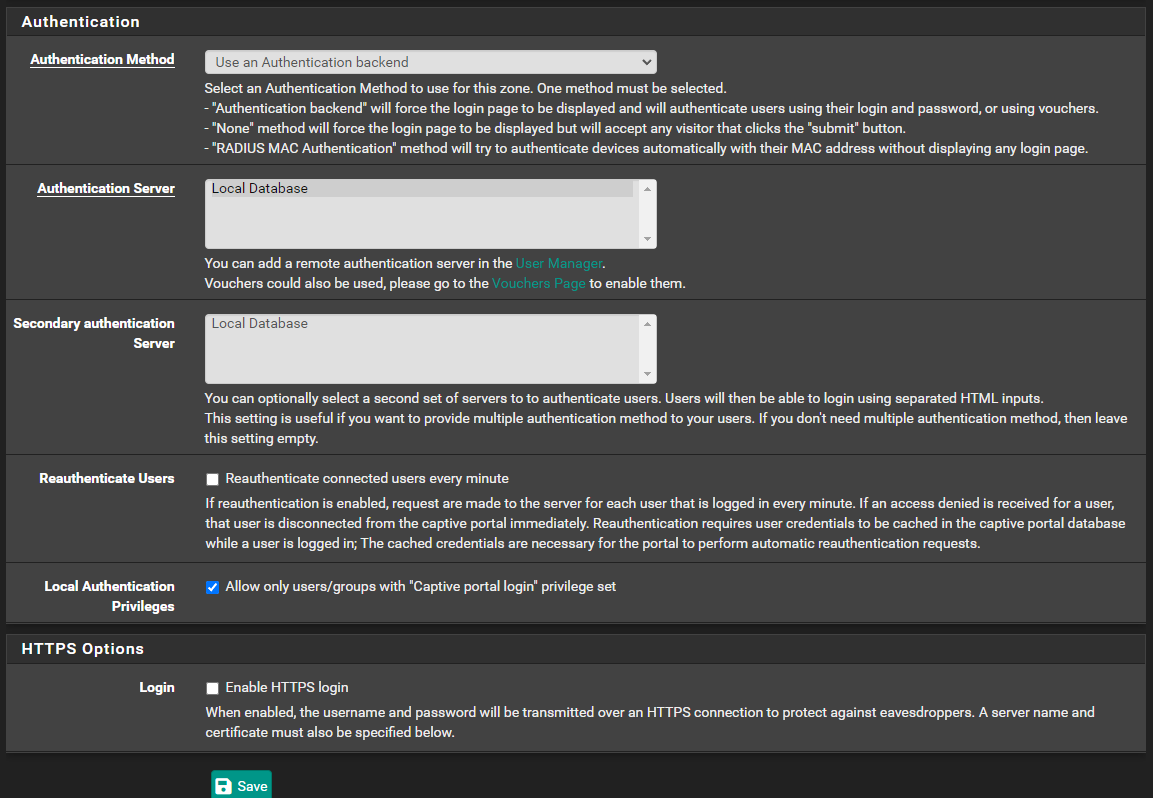
@yogi_en said in Help Needed!. Captive portal not working ( No login page ):
I didn't get any pop browser or captive portal login.
Ah, I'm curious.
What OS / what device ?
When you buy a device from here it works, and as far as I know you, as a user, can't do a thing to stop this process. As Apple checks accepting an app on their platform.
Other brands : they care less ?
Windows : I've tested 10 'home', 'pro', 11 home (burk) and 'pro'.
I even debloated them (see Youtube about that) and portals are recognized. That is, you still have to spot the tray notification message and act upon it.
I've seen people using some high end (consumer high end that is) firewalls/antivirus and they had set up : "only trust my home wifi network" so now their security was great ..... and moments later they want to use their device on my wifi network ....
Yeah, that was a fail .... as the device was following the original instruction : do not trust / use 'other' networks. So they went for the Hall 200 problem : do not give automates conflict instructions, as they will bite (the example : kill) you.
@yogi_en said in Help Needed!. Captive portal not working ( No login page ):
I even tried a local url http://192.168.5.25:5000
Portal firewall rules will redirect port '80' and port 443 if you use https.
So port "5000" : you hit the wall.
Use these :
[image: 1677654510615-6cc8be0f-9940-4ffe-bfd8-17e55af044a9-image.png]
to test the portal web server.
Or, when connected to the captive portal network, as soon as you received an IP (DNS, gateway, network) : use http://192.168.10.1:8002/index.php?zone=ZONE
where ZONE is your zone ID.
Btw : http://captive.apple.com/hotspot-detect.html should also work as this is a http thus port '80' TCP request.
@yogi_en said in Help Needed!. Captive portal not working ( No login page ):
DNS server is my router 192.168.1.1 ( which I cannot ping when CP is enabled ).
I have to shave-up your definition of a captive portal.
A captive portal allows minimal interaction with itself.
If 19.168.10.1 is your captive portal pfSense interface, you can :
Do DHCP
Do DNS requests on port 53, UDP and TCP.
Port 80 (http) listens to you.
Port 443 (443) listens to you - if you've activated that
Ping the captive portal pfSense IP
You can NOT go to some other network, and that includes your local networks like 192.168.5.x
So, right, the portal works : no ping or whatever to 192.168.5.x
I just tested :
I've connected my phone to the captive portal (as the stupid thing does not accept the wifi connection without a login first).
With an phone app I launched a 100 times ping to the portal interface, that was 192.168.2.1 for me.
It replies constantly.
Then, in the pfSense dashboard GUI, I removed my phone's connection.
The ping app in my phone continued to send pings to 192.168.2.1, and 192.168.2.1 continues to reply. Or, at that moment, from a captive portal firewall point of view, my phone was disconnected.