@unreal516 said in CP and DHCPD Issue 2.6.0:
I have tried rebooting the CP service
The captive portal isn't a 'service'.
A web server, a copy of nginx, is started and listens on port 'localhost' (127.0.0.1) using port 800x and 800x+ (if you are also using https).
Because you want the DHCP server to work for your clients (static IP setup for not network aware clients) won't work ;) you have set up a DHCP server for your captive portal network.
Normally, your "vmx1" should be your LAN.
The captive portal interface should be ... vmx2, some "OPT1" second LAN type interface. As I advice you strongly to put your trusted devices on a LAN and the not trusted devices on another, OPTx network, dedicated for portal users, who are nontrusted by default.
Otherwise : if you trust them, why bother : put an AP on your LAN network, give them your SSID password and you're done.
Btw "vmx1" means : you are using a VM ?
My advise : great ! But first make the portal work on a bare bone, and when it all works out very well, go add another layer of complexity.
"dhcp.c:4164: Failed to send 300 byte long packet over vmx1 interface." means : there is an issue with the vmx1 interface itself. Not some firewall issue.
Btw: the captive portal "ipfw" firewall rules, used by the captive portal, pass all DHCP (and DNS) traffic by default. You don't need to add "DHCP" type firewall rules on your vmx1 "pf" firewall
rule tab.
Also, firewall rules, pf and ipfw, filter incoming traffic. That is : traffic oming INTO the interface.
Your error shows an issue with outgoing traffic, traffic generated by the dhcd (with a "d") server deamon.
Your "dhcp" : is this an error from the dhcp client, typically running on the WAN interface ?
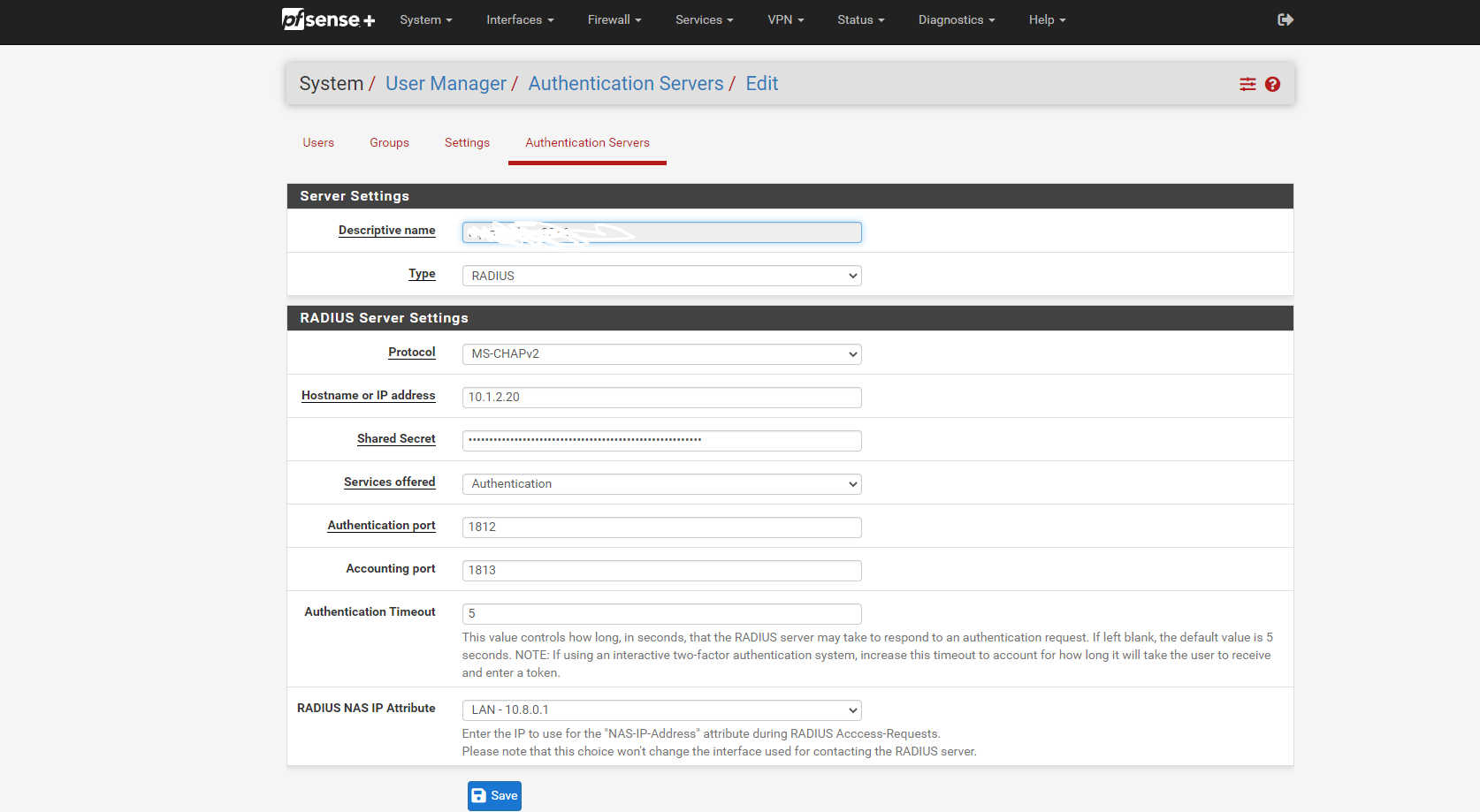
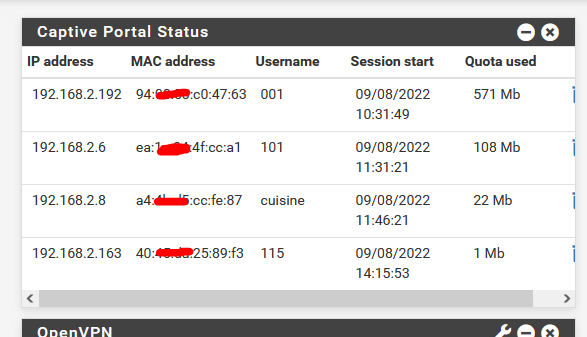
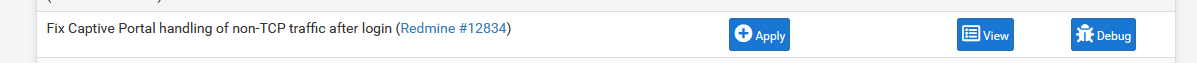
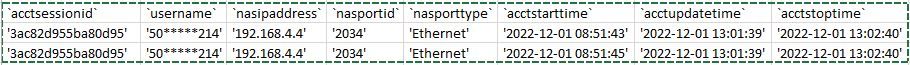
Also : can't remember any more, wasn't there an issue (bug) 2.6.0. with "captive portal only accepts TCP" (and not UDP and ICMP) ? This would explain DHCP == UDP issues.
What are your patches ?
Using the pfSense System patches packages is not optional anymore ;)