@oldschoolrouterjockey
Yeah, accepting DNS is a must have. DNS is mostly UDP btw, and rarely TCP.
@oldschoolrouterjockey said in Captive portal Help:
and also 8002
Don't need to do that.
The device will do the "http" (port 80) request initially. There is no need that the portal user needs to know that "port 8002" is used on the pfSense side.
Initial user port 80 traffic gets redirected at the firewall level to port 8002. The portal user's browser will never know it was talking to the server over this port. Or port 8003 when https is used.
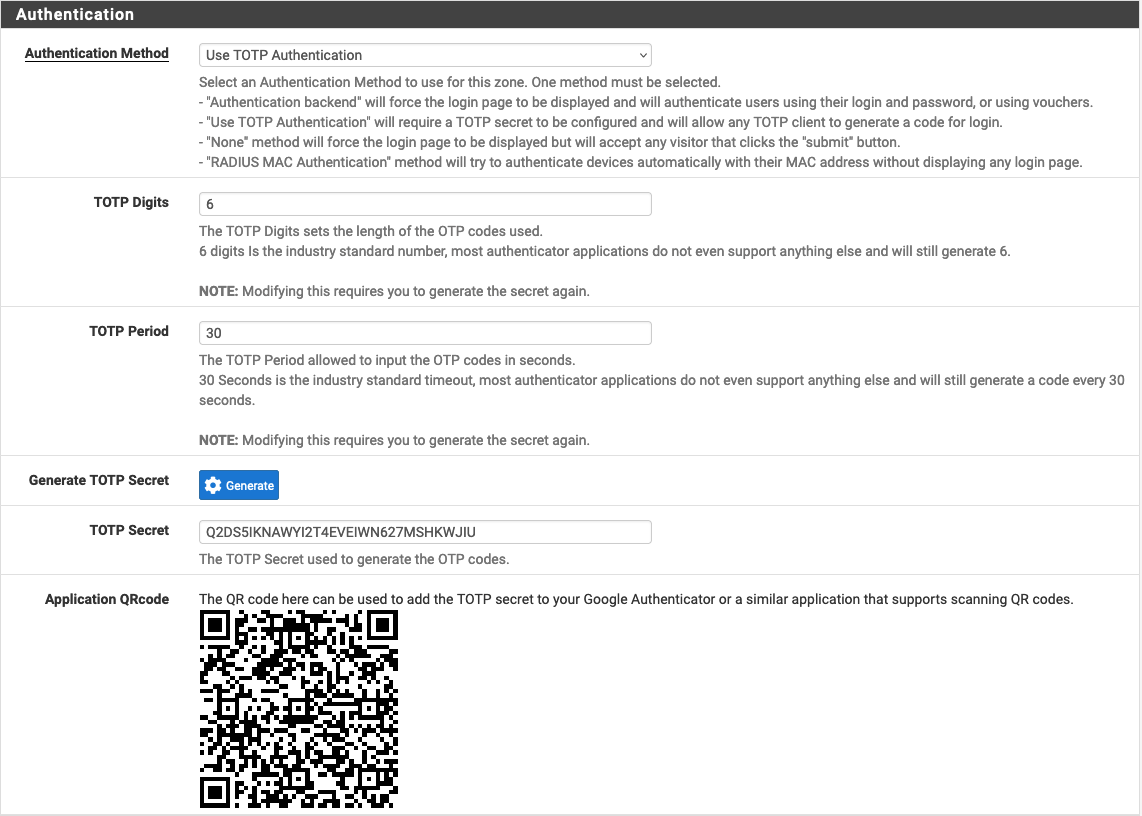
# Captive Portal
rdr on igc1 inet proto tcp from any to ! <cpzoneid_2_cpips> port 80 tagged cpzoneid_2_rdr -> 192.168.2.1 port 8002
where igc1 is the portal interface, and "cpzoneid_2" is the portal zone ID, 192.168.2.1 is the portal IPv4.
A second portal instance will use, probably, port 8004 and another ID.
http portal mode is ok to "make it work".
Go to the https version, as most browsers will bark, showing warnings that will be errors in the near future, when not-TLS is used for any http traffic.
Also, the RFC1918 Portal IP won't show up anymore, the local pfSense portal host name is now used, because that's what certificates is all about.
Ones "https portal authentication" is set up, your done done with it installation. It will work well from then on.
There is a price tag, as you will need to rent a domain name. Annual fee : less then 5$ / year ?
Before you chose a registrar, make sure that it will work with "Lets encrypt", the pfSense package that will handle the automatic certificate renewal.
Advantage is : portal login goes over https, so there is no need anymore use any SSID security, the traffic is already encrypted. As soon as the user is logged in, all subsequent traffic is also using TLS : all mail, web and whatever uses TLS these days.
And as said above : portal users that want to add their own security : that's where VPN ISPs come in handy. : even you as the pfSense admin can 'see' their traffic anymore, you will have to trust your portal user ( ! ), which is actually a strange situation because portal users are actually 'untrusted' as they can do what they want with YOUR internet connection.
edit :
Purely optional :
If you have the NTP deamon running on pfSense, have it also listening on the portal interface.
Add this :
[image: 1694757233977-a555fc6f-40df-4909-b012-516cf32552fe-image.png]
to the portal DHCP server (192.168.2.1 is my portal interface IP).
Add a rule like this :
[image: 1694757428967-2b7ce0ff-e511-460e-a7c2-805bd12a5826-image.png]
to the portal firewall so portal users can use the pfSense NTP if they want to.