@modesty said in Client export - no configurations available:
This "help text" I dont understand what to do...
It says :
If a client is missing from the list it is likely due to a CA mismatch between the OpenVPN server instance and the client certificate, the client certificate does not exist on this firewall, or a user certificate is not associated with a user when local database authentication is enabled.
which means ... what it says.
When a 'client' uses a VPN connection, it should 'authenticate' against the pfSense OpenVPN server, at the connection needs to be secured.
And you have a choice :
A user name and password.
A certificate st, assigned for that user.
Or a combination of both.
You've set up a OpenVPN server, you can see the "access mode" :
[image: 1639726821841-b2b463b7-c6ed-4354-9f17-389cf62b20e7-image.png]
You have made a choice here :
[image: 1639726871161-93502a9d-2fd9-4634-af96-291a397d0474-image.png]
If could create a user + password here :
[image: 1639726910738-5cc6ee04-8442-4c4e-8520-2a8cbf577233-image.png]
and - important, assigned it to the OpenVPN user group, the OpenVPN client export utility can't find a user to include in the export files.
Or create a 'CA' certificate here :
[image: 1639728519102-e87f5c2a-ba0f-437c-893a-b88034d5fc47-image.png]
I called it "CA-openvpn". As you can see,, it's in use by my OpenVPN server right now.
This CA cert is only created ones.
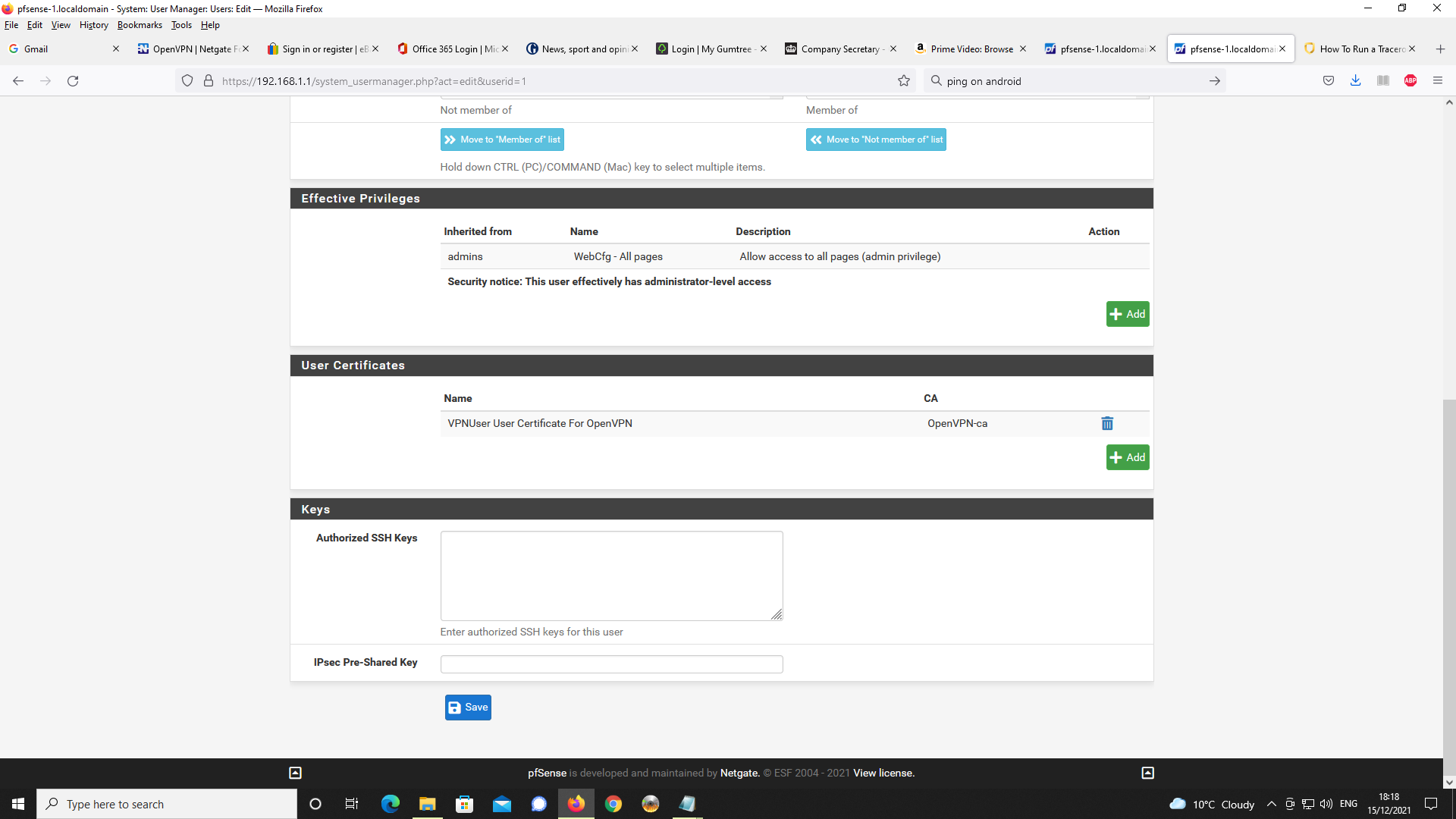
After that, for each user (do not share certificates among users !!) you create Certificates :
[image: 1639728823425-11ba180a-74b8-45c8-be64-5f8c8bee5f53-image.png]
This one is for me, for my iPhone. I also created one for my pad, one or two for the PC's I use to remotely access this pfSense OpenVPN server.
Again, this certificate is in use right now by the OpenVPN pfsense server.
Note that this CA certificate is assigned to the OpenVP server :
[image: 1639729087843-e5b7de2b-c61b-4ce3-aa04-dcaa31afcb53-image.png]
Because I chose :
[image: 1639728938281-0104ea83-044d-4ebe-851b-5b723f41fcff-image.png]
which means 'only certificates' (and no user or password), I now have this listed on the OpenVPN client export list :
[image: 1639729003496-ceaadc91-b136-4008-85d4-afce76204731-image.png]
Now, read again :
If a client is missing from the list it is likely due to a CA mismatch between the OpenVPN server instance and the client certificate, the client certificate does not exist on this firewall, or a user certificate is not associated with a user when local database authentication is enabled.
and I'll bet that all is clear now.
and
If you have Youtube installed, go here Youtube > Netgate > Configuring OpenVPN Remote Access in pfSense Software - it's a bare minimum 'need to know' video, but it explains the steps.
Several other, far more detailed OpenVPN videos are also a viable. They are old, but do still apply.
A couple of thousand other pfSense OpenVPN video's also exist.
An there is the manual, in the top right corner, right in front of you, one click away.
 23
0 Votes5 Posts1k Views
23
0 Votes5 Posts1k Views