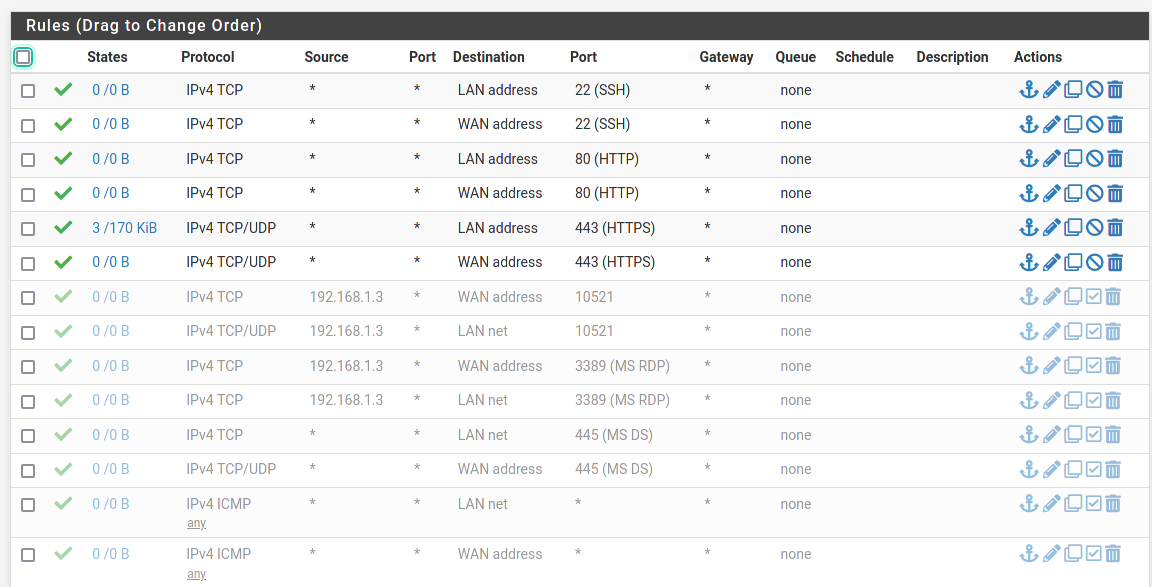
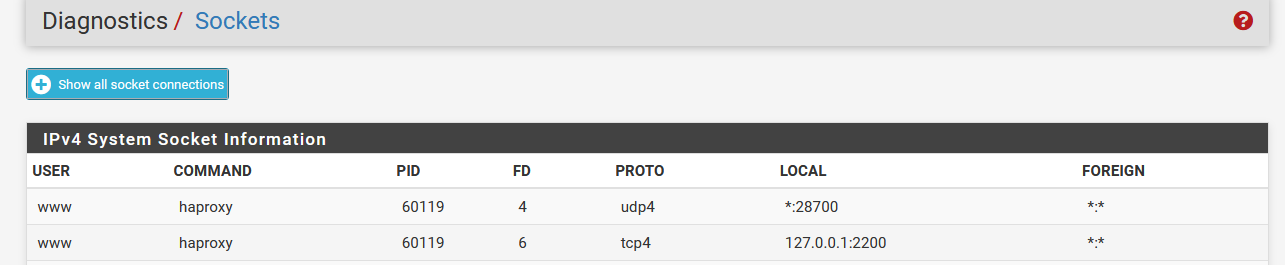
I have tired tcp mode, but still the same, slow as hell. :(
My tcp config:
# Automaticaly generated, dont edit manually.
# Generated on: 2021-07-04 04:45
global
maxconn 10000
log /var/run/log local0 debug
stats socket /tmp/haproxy.socket level admin expose-fd listeners
gid 80
nbproc 1
nbthread 4
hard-stop-after 15m
chroot /tmp/haproxy_chroot
daemon
ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-server-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-bind-options ssl-min-ver TLSv1.3 no-tls-tickets
ssl-default-server-options ssl-min-ver TLSv1.3 no-tls-tickets
tune.ssl.default-dh-param 2048
server-state-file /tmp/haproxy_server_state
listen HAProxyLocalStats
bind 127.0.0.1:2200 name localstats
mode http
stats enable
stats refresh 60
stats admin if TRUE
stats show-legends
stats uri /haproxy/haproxy_stats.php?haproxystats=1
timeout client 5000
timeout connect 5000
timeout server 5000
frontend frontend-merged
bind 81.0.126.16:443 name 81.0.126.16:443
bind 2a01:36c:1300:80d7:344b:50ff:feb7:efda:443 name 2a01:36c:1300:80d7:344b:50ff:feb7:efda:443
mode tcp
log global
option socket-stats
option tcplog
maxconn 5000
timeout client 60000
tcp-request inspect-delay 5s
tcp-request content accept if { req.ssl_hello_type 1 }
acl src_is_ipv4 src 0.0.0.0/0
acl ACL10 req.ssl_sni -i pfsense.skynet.zone
acl ACL20 req.ssl_sni -i ilo.skynet.zone
acl ACL30 req.ssl_sni -i esxi.skynet.zone
acl ACL40 req.ssl_sni -i dsm.skynet.zone
acl ACL50 req.ssl_sni -i linuxsrv.skynet.zone
acl ACL60 req.ssl_sni -i ols.skynet.zone
acl ACL70 req.ssl_sni -i phpmyadmin.skynet.zone
acl ACL80 req.ssl_sni -i p2p.skynet.zone
acl ACL90 req.ssl_sni -i plex.skynet.zone
acl ACL100 req.ssl_sni -i ipcam.skynet.zone
acl ACL110 req.ssl_sni -i photo.skynet.zone
acl ACL120 req.ssl_sni -i drive.skynet.zone
acl ACL130 req.ssl_sni -i file.skynet.zone
acl WEB10 req.ssl_sni -i skynet.zone
acl WEB20 req.ssl_sni -i tenguhse.com
acl WEB30 req.ssl_sni -i ebmas.hu
acl WEB40 req.ssl_sni -i wtwarrior.hu
acl WEB50 req.ssl_sni -i blacklotus.fit
acl WEB60 req.ssl_sni -i bvntech.hu
acl WEB70 req.ssl_sni -i evagyogytorna.hu
acl WEB80 req.ssl_sni -i retaljaegyesulet.hu
acl WEB90 req.ssl_sni -i korosliget.hu
use_backend pfsense.skynet.zone_ipvANY if ACL10
use_backend ilo.skynet.zone_ipv4 if ACL20 src_is_ipv4
use_backend ilo.skynet.zone_ipv6 if ACL20 !src_is_ipv4
use_backend esxi.skynet.zone_ipv4 if ACL30 src_is_ipv4
use_backend esxi.skynet.zone_ipv6 if ACL30 !src_is_ipv4
use_backend dsm.skynet.zone_ipv4 if ACL40 src_is_ipv4
use_backend dsm.skynet.zone_ipv6 if ACL40 !src_is_ipv4
use_backend linuxsrv.skynet.zone_ipv4 if ACL50 src_is_ipv4
use_backend linuxsrv.skynet.zone_ipv6 if ACL50 !src_is_ipv4
use_backend ols.skynet.zone_ipv4 if ACL60 src_is_ipv4
use_backend ols.skynet.zone_ipv6 if ACL60 !src_is_ipv4
use_backend phpmyadmin.skynet.zone_ipv4 if ACL70 src_is_ipv4
use_backend phpmyadmin.skynet.zone_ipv6 if ACL70 !src_is_ipv4
use_backend p2p.skynet.zone_ipv4 if ACL80 src_is_ipv4
use_backend p2p.skynet.zone_ipv6 if ACL80 !src_is_ipv4
use_backend plex.skynet.zone_ipv4 if ACL90 src_is_ipv4
use_backend plex.skynet.zone_ipv6 if ACL90 !src_is_ipv4
use_backend ipcam.skynet.zone_ipv4 if ACL100 src_is_ipv4
use_backend ipcam.skynet.zone_ipv6 if ACL100 !src_is_ipv4
use_backend photo.skynet.zone_ipv4 if ACL110 src_is_ipv4
use_backend photo.skynet.zone_ipv6 if ACL110 !src_is_ipv4
use_backend drive.skynet.zone_ipv4 if ACL120 src_is_ipv4
use_backend drive.skynet.zone_ipv6 if ACL120 !src_is_ipv4
use_backend file.skynet.zone_ipv4 if ACL130 src_is_ipv4
use_backend file.skynet.zone_ipv6 if ACL130 !src_is_ipv4
use_backend skynet.zone_ipv4 if WEB10 src_is_ipv4
use_backend skynet.zone_ipv6 if WEB10 !src_is_ipv4
use_backend tenguhse.com_ipv4 if WEB20 src_is_ipv4
use_backend tenguhse.com_ipv6 if WEB20 !src_is_ipv4
use_backend ebmas.hu_ipv4 if WEB30 src_is_ipv4
use_backend ebmas.hu_ipv6 if WEB30 !src_is_ipv4
use_backend wtwarrior.hu_ipv4 if WEB40 src_is_ipv4
use_backend wtwarrior.hu_ipv6 if WEB40 !src_is_ipv4
use_backend blacklotus.fit_ipv4 if WEB50 src_is_ipv4
use_backend blacklotus.fit_ipv6 if WEB50 !src_is_ipv4
use_backend bvntech.hu_ipv4 if WEB60 src_is_ipv4
use_backend bvntech.hu_ipv6 if WEB60 !src_is_ipv4
use_backend evagyogytorna.hu_ipv4 if WEB70 src_is_ipv4
use_backend evagyogytorna.hu_ipv6 if WEB70 !src_is_ipv4
use_backend retaljaegyesulet.hu_ipv4 if WEB80 src_is_ipv4
use_backend retaljaegyesulet.hu_ipv6 if WEB80 !src_is_ipv4
use_backend korosliget.hu_ipv4 if WEB90 src_is_ipv4
use_backend korosliget.hu_ipv6 if WEB90 !src_is_ipv4
frontend http-to-https
bind 81.0.126.16:80 name 81.0.126.16:80
bind 2a01:36c:1300:80d7:344b:50ff:feb7:efda:80 name 2a01:36c:1300:80d7:344b:50ff:feb7:efda:80
mode http
log global
option socket-stats
option httplog
option http-keep-alive
option forwardfor
acl https ssl_fc
http-request set-header X-Forwarded-Proto http if !https
http-request set-header X-Forwarded-Proto https if https
maxconn 5000
timeout client 60000
http-request redirect scheme https
backend pfsense.skynet.zone_ipvANY
mode tcp
id 100
log global
timeout connect 60000
timeout server 60000
retries 3
server pfsense.skynet.zone 192.168.1.1:443 id 101
backend ilo.skynet.zone_ipv4
mode tcp
id 10102
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server ilo.skynet.zone 192.168.1.40:443 id 10103
backend ilo.skynet.zone_ipv6
mode tcp
id 20102
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend esxi.skynet.zone_ipv4
mode tcp
id 10104
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server esxi.skynet.zone 192.168.1.45:443 id 10105
backend esxi.skynet.zone_ipv6
mode tcp
id 20104
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend dsm.skynet.zone_ipv4
mode tcp
id 10106
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server dsm.skynet.zone 192.168.1.50:5001 id 10107
backend dsm.skynet.zone_ipv6
mode tcp
id 20106
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend linuxsrv.skynet.zone_ipv4
mode tcp
id 10108
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server linuxsrv.skynet.zone 192.168.1.60:10000 id 10109
backend linuxsrv.skynet.zone_ipv6
mode tcp
id 20108
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend ols.skynet.zone_ipv4
mode tcp
id 10110
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server ols.skynet.zone 192.168.1.60:7443 id 10111
backend ols.skynet.zone_ipv6
mode tcp
id 20110
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend phpmyadmin.skynet.zone_ipv4
mode tcp
id 10112
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server phpmyadmin.skynet.zone 192.168.1.60:8443 id 10113
backend phpmyadmin.skynet.zone_ipv6
mode tcp
id 20112
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend p2p.skynet.zone_ipv4
mode tcp
id 10114
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server p2p.skynet.zone 192.168.1.60:5100 id 10115
backend p2p.skynet.zone_ipv6
mode tcp
id 20114
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend plex.skynet.zone_ipv4
mode tcp
id 10116
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server plex.skynet.zone 192.168.1.60:32400 id 10117
backend plex.skynet.zone_ipv6
mode tcp
id 20116
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend ipcam.skynet.zone_ipv4
mode tcp
id 10118
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server ipcam.skynet.zone 192.168.1.50:9901 id 10119
backend ipcam.skynet.zone_ipv6
mode tcp
id 20118
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend photo.skynet.zone_ipv4
mode tcp
id 10120
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server photo.skynet.zone 192.168.1.50:10005 id 10121
backend photo.skynet.zone_ipv6
mode tcp
id 20120
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend drive.skynet.zone_ipv4
mode tcp
id 10122
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server drive.skynet.zone 192.168.1.50:10003 id 10123
backend drive.skynet.zone_ipv6
mode tcp
id 20122
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend file.skynet.zone_ipv4
mode tcp
id 10124
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server file.skynet.zone 192.168.1.50:7001 id 10125
backend file.skynet.zone_ipv6
mode tcp
id 20124
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend skynet.zone_ipv4
mode tcp
id 10126
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server skynet.zone 192.168.1.60:8443 id 10127
backend skynet.zone_ipv6
mode tcp
id 20126
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend tenguhse.com_ipv4
mode tcp
id 10128
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server tenguhse.com 192.168.1.60:8443 id 10129
backend tenguhse.com_ipv6
mode tcp
id 20128
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend ebmas.hu_ipv4
mode tcp
id 10130
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server ebmas.hu 192.168.1.60:8443 id 10131
backend ebmas.hu_ipv6
mode tcp
id 20130
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend wtwarrior.hu_ipv4
mode tcp
id 10132
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server wtwarrior.hu 192.168.1.60:8443 id 10133
backend wtwarrior.hu_ipv6
mode tcp
id 20132
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend blacklotus.fit_ipv4
mode tcp
id 10134
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server blacklotus.fit 192.168.1.60:8443 id 10135
backend blacklotus.fit_ipv6
mode tcp
id 20134
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend bvntech.hu_ipv4
mode tcp
id 10136
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server bvntech.hu 192.168.1.60:8443 id 10137
backend bvntech.hu_ipv6
mode tcp
id 20136
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend evagyogytorna.hu_ipv4
mode tcp
id 10138
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server evagyogytorna.hu 192.168.1.60:8443 id 10139
backend evagyogytorna.hu_ipv6
mode tcp
id 20138
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend retaljaegyesulet.hu_ipv4
mode tcp
id 10140
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server retaljaegyesulet.hu 192.168.1.60:8443 id 10141
backend retaljaegyesulet.hu_ipv6
mode tcp
id 20140
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
backend korosliget.hu_ipv4
mode tcp
id 10142
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv4@ usesrc clientip
server korosliget.hu 192.168.1.60:8443 id 10143
backend korosliget.hu_ipv6
mode tcp
id 20142
log global
timeout connect 60000
timeout server 60000
retries 3
source ipv6@ usesrc clientip
Hope somebody know what should i do..