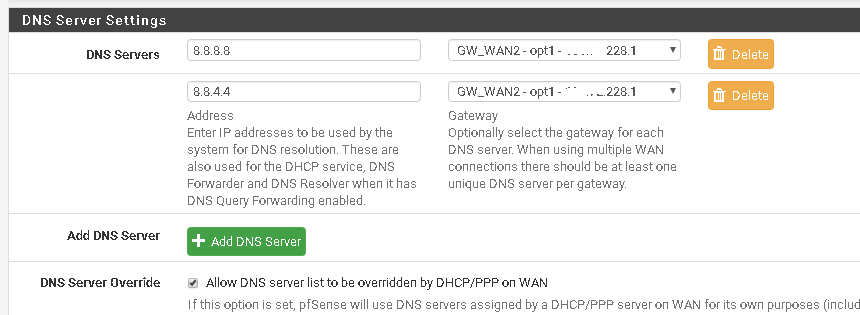
[image: 1540328106153-dns-resolver-advanced-settings-resized.png]
Last 190 DNS Resolver Log Entries. (Maximum 190)
Oct 23 21:57:20 unbound 41539:2 notice: remote address is 10.200.3.17 port 46382
Oct 23 21:57:20 unbound 41539:2 notice: sendto failed: Invalid argument
Oct 23 21:57:17 unbound 41539:1 notice: remote address is 10.200.3.17 port 35019
Oct 23 21:57:17 unbound 41539:1 notice: sendto failed: Invalid argument
Oct 23 21:50:47 unbound 41539:0 info: generate keytag query _ta-4a5c-4f66. NULL IN
Oct 23 21:50:47 unbound 41539:2 info: generate keytag query _ta-4a5c-4f66. NULL IN
Oct 23 21:50:44 unbound 41539:0 info: start of service (unbound 1.7.3).
Oct 23 21:50:44 unbound 41539:0 notice: init module 1: iterator
Oct 23 21:50:44 unbound 41539:0 notice: init module 0: validator
Oct 23 21:50:41 unbound 71806:0 info: 32.000000 64.000000 4
Oct 23 21:50:41 unbound 71806:0 info: 16.000000 32.000000 2
Oct 23 21:50:41 unbound 71806:0 info: 8.000000 16.000000 3
Oct 23 21:50:41 unbound 71806:0 info: 2.000000 4.000000 1
Oct 23 21:50:41 unbound 71806:0 info: 0.131072 0.262144 2
Oct 23 21:50:41 unbound 71806:0 info: 0.065536 0.131072 1
Oct 23 21:50:41 unbound 71806:0 info: 0.032768 0.065536 7
Oct 23 21:50:41 unbound 71806:0 info: lower(secs) upper(secs) recursions
Oct 23 21:50:41 unbound 71806:0 info: [25%]=0.0561737 median[50%]=0.262144 [75%]=24
Oct 23 21:50:41 unbound 71806:0 info: histogram of recursion processing times
Oct 23 21:50:41 unbound 71806:0 info: average recursion processing time 11.680555 sec
Oct 23 21:50:41 unbound 71806:0 info: server stats for thread 3: requestlist max 4 avg 1.75 exceeded 0 jostled 0
Oct 23 21:50:41 unbound 71806:0 info: server stats for thread 3: 27 queries, 7 answers from cache, 20 recursions, 0 prefetch, 0 rejected by ip ratelimiting
Oct 23 21:50:41 unbound 71806:0 info: 32.000000 64.000000 1
Oct 23 21:50:41 unbound 71806:0 info: 16.000000 32.000000 8
Oct 23 21:50:41 unbound 71806:0 info: 8.000000 16.000000 5
Oct 23 21:50:41 unbound 71806:0 info: 4.000000 8.000000 3
Oct 23 21:50:41 unbound 71806:0 info: 1.000000 2.000000 1
Oct 23 21:50:41 unbound 71806:0 info: 0.524288 1.000000 1
Oct 23 21:50:41 unbound 71806:0 info: 0.262144 0.524288 2
Oct 23 21:50:41 unbound 71806:0 info: 0.131072 0.262144 5
Oct 23 21:50:41 unbound 71806:0 info: 0.065536 0.131072 4
Oct 23 21:50:41 unbound 71806:0 info: 0.032768 0.065536 3
Oct 23 21:50:41 unbound 71806:0 info: lower(secs) upper(secs) recursions
Oct 23 21:50:41 unbound 71806:0 info: [25%]=0.16384 median[50%]=4.66667 [75%]=17.5
Oct 23 21:50:41 unbound 71806:0 info: histogram of recursion processing times
Oct 23 21:50:41 unbound 71806:0 info: average recursion processing time 8.791496 sec
Oct 23 21:50:41 unbound 71806:0 info: server stats for thread 2: requestlist max 4 avg 2.0303 exceeded 0 jostled 0
Oct 23 21:50:41 unbound 71806:0 info: server stats for thread 2: 50 queries, 17 answers from cache, 33 recursions, 0 prefetch, 0 rejected by ip ratelimiting
Oct 23 21:50:41 unbound 71806:0 info: 16.000000 32.000000 2
Oct 23 21:50:41 unbound 71806:0 info: 8.000000 16.000000 3
Oct 23 21:50:41 unbound 71806:0 info: 4.000000 8.000000 1
Oct 23 21:50:41 unbound 71806:0 info: 2.000000 4.000000 1
Oct 23 21:50:41 unbound 71806:0 info: 0.262144 0.524288 1
Oct 23 21:50:41 unbound 71806:0 info: 0.131072 0.262144 3
Oct 23 21:50:41 unbound 71806:0 info: 0.065536 0.131072 5