@mvbif Yes, you're right, port forwarding is a DNAT, actually, I was wrong. The thing is, this port forwarding is SNAT-ing too.
Nat lonely should not allow anyway traffic not allowed from a security rules.
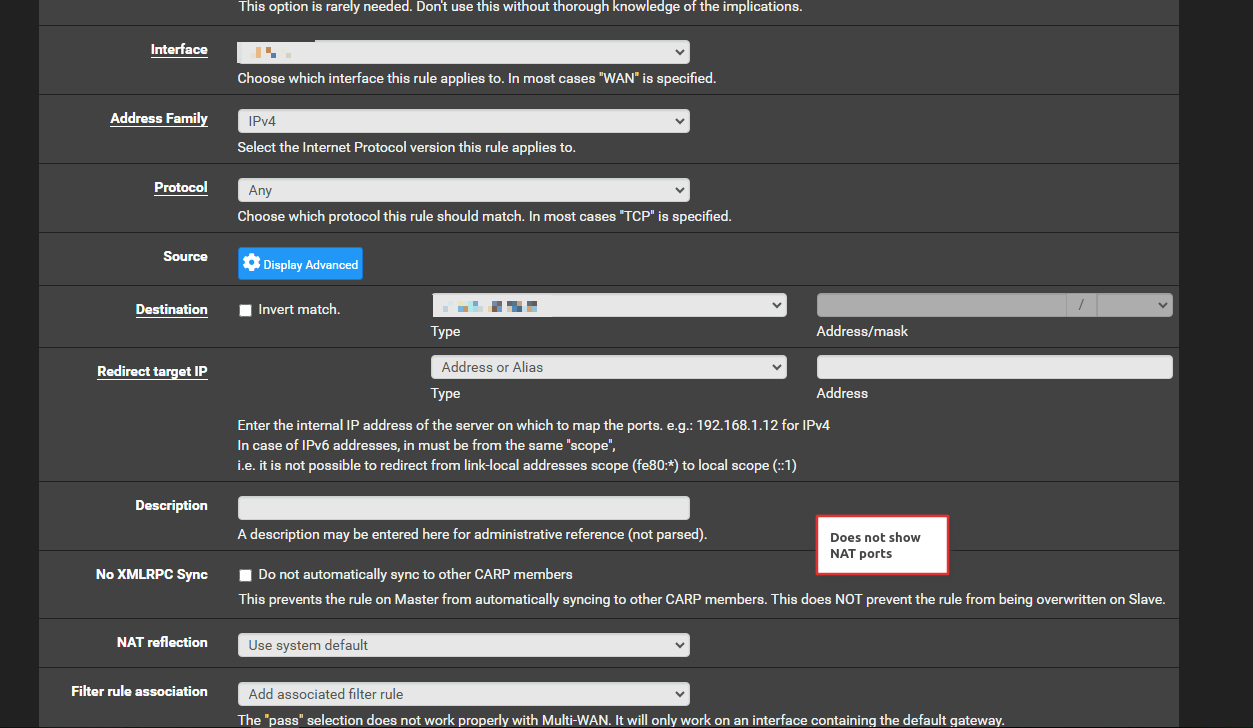
The port forwarding was done and a rule has been added to allow the traffic. Also, the IPSec traffic is allowed via a different rule, so the traffic is allowed.
So now i will check but, i feel to say that yes that nat rule will apply only on traffic coming from openvpn and has that destination.
Well, this is what should happen. Only traffic coming in via the OpenVPN interface should match. But it doesn't.
About the ipsec traffic, are you saying that with nat on, your ipsec host can ping 172.x.x.x , with nat off can't anymore?
Yes, that's what I mean. If I exclude the IPSec connected subnet (10.41.13.0/24) from the NAT rule OR I disable the NAT rule, the IPSec traffic cannot go to 172.31.254.100.
Btw ipsec should have rules permitting traffic to 10.41.99.65 isn't it?
Yes.
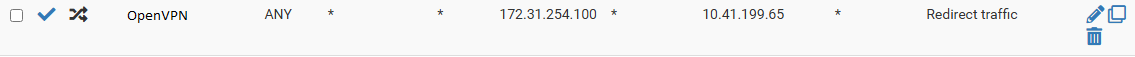
Also, the thing is, the rule's SNATing too: With the rule in place, 10.41.13.225 for example, can curl 172.31.254.100 and get a reply. On the 10.41.199.65 (the actual IP that the port forwarding rule is set on) I see the traffic coming from 10.41.199.2 (PFSense).
Test scenario: Via the IPSec, I'm sending, from 10.41.13.225 a curl 172.31.254.100:2345 (port was chosen so no traffic is going to disturb the test). With the port forwarding rule enabled, I can see traffic on 10.41.199.65, coming from 10.41.199.2 (PFSense IP address) dst port 2345. This clearly matches the traffic. Checking the firewall logs I can see the traffic being allowed from 10.41.13.225 to 10.41.199.65 (translated IP address). This means that PFSense matched the traffic and DNATed via the above rule, but it also SNATed (why?).
Disabling the above rule and running the same scenario: curl 172.31.254.100:2345 in the firewall logs I can see the traffic as being allowed from 10.41.13.225 to 172.31.254.100 (not translated) but the traffic doesn't reach the 10.41.199.65 VM (normal, since it was not translated).
What's going on?!
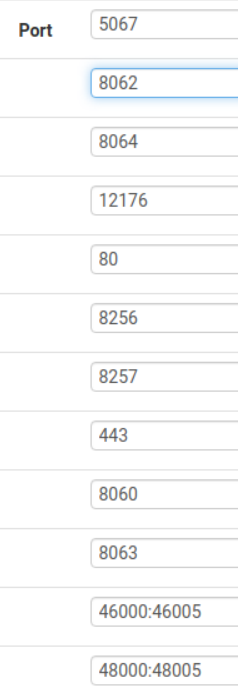
Also, check this out: states tables filtered by 2345 (dst port):
[image: 1740546197177-8710e90a-870d-4772-8d91-8056ab5d502a-image.png]
So it sees the traffic as coming from the IPSec interface, but it's SNATing it and then delivering it to 10.41.199.65.
I have NO NAT RULES to match this traffic (outgoing on VLAN199 interface) so there should be no SNAT done, from what I can say. There's no NAT rule matching 10.41.13.225 or 10.41.13.0/24 or 10.41.0.0/16.
Can't I somehow see what NAT rule is this traffic matching?