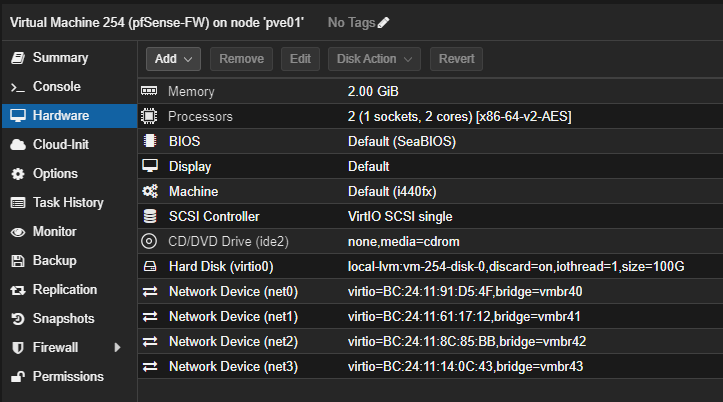
So I installed the pimd package
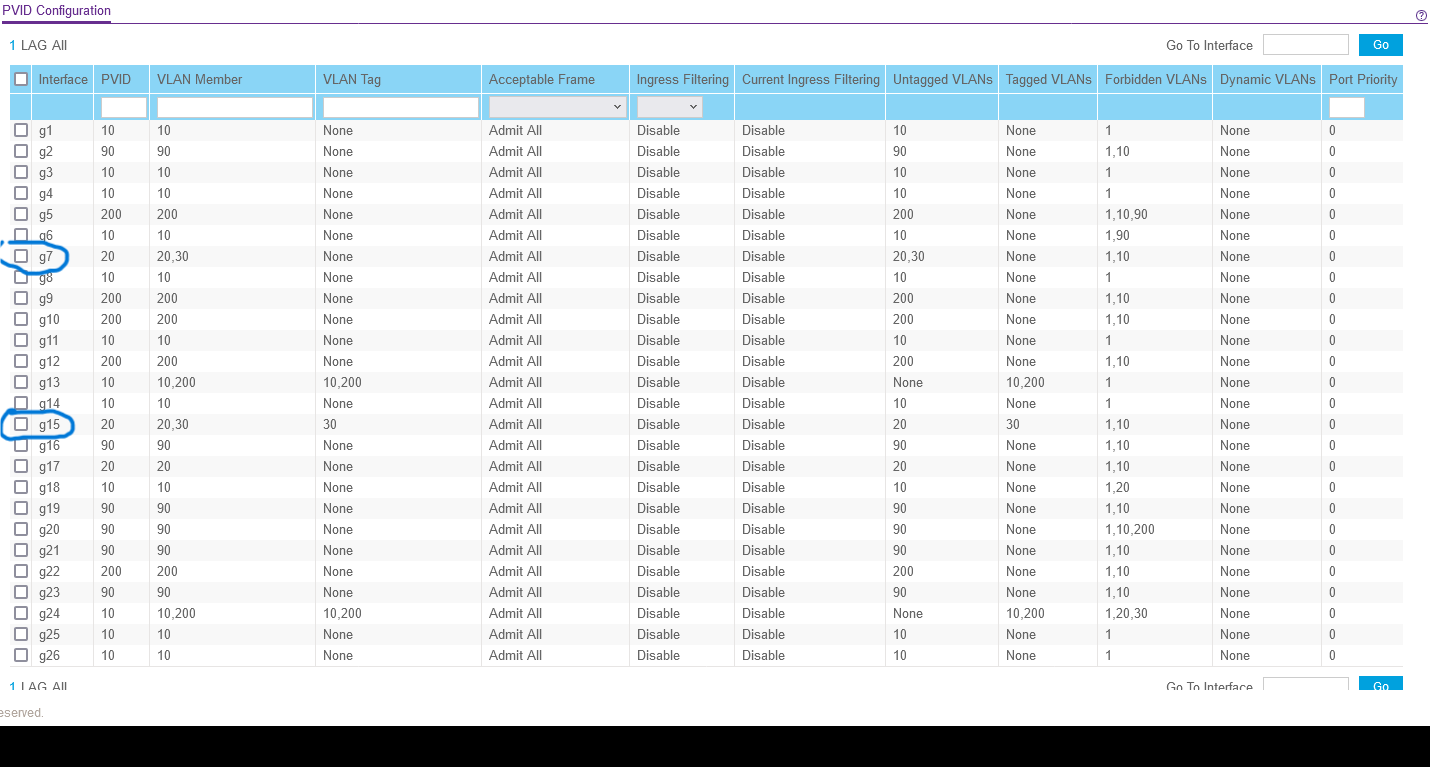
Added the two VLANs to the PIMD interfaces list and enabled them
Add one pfsense interface as RP address for PIMd (192.168.12.1)
left all other pimd configuration options at defaults
In addition, I add on each of the interfaces a firewall rule to pass everything, also checked the "Allow IP options" on those rules. Logging enabled.
In addition, I add on each interface at the very end a "catch all" blocking rule, also with logging enabled. This is so that I can see if my "pass" rule misses anything.
Then I started VLC multicast streaming server on 192.168.12.101 (vlan12):
cvlc BigBuckBunny_320x180.mp4 --sout "#rtp{dst=239.255.1.2,port=5004,ttl=10,mux=ts,sap,name=Bunny}" --no-sout-all --sout-keep --loop
PIMD status shows the server in its routing table:
Virtual Interface Table ======================================================
Vif Local Address Subnet Thresh Flags Neighbors
--- --------------- ------------------ ------ --------- -----------------
0 192.168.1.1 192.168.1 1 DR NO-NBR
1 192.168.2.1 192.168.2 1 DR NO-NBR
2 192.168.10.1 192.168.10 1 DISABLED
3 192.168.12.1 192.168.12 1 DR NO-NBR
4 79.239.182.225 79.239.182.225/32 1 DISABLED
5 192.168.1.1 register_vif0 1
Vif SSM Group Sources
Multicast Routing Table ======================================================
----------------------------------- (S,G) ------------------------------------
Source Group RP Address Flags
--------------- --------------- --------------- ---------------------------
192.168.12.101 239.255.1.2 192.168.12.1 CACHE SG
Joined oifs: .....j
Pruned oifs: ......
Leaves oifs: ......
Asserted oifs: ......
Outgoing oifs: .....o
Incoming : ...I..
TIMERS: Entry JP RS Assert VIFS: 0 1 2 3 4 5
205 60 0 0 0 0 0 0 0 0
----------------------------------- (S,G) ------------------------------------
Source Group RP Address Flags
--------------- --------------- --------------- ---------------------------
192.168.12.101 239.255.255.255 192.168.12.1 CACHE SG
Joined oifs: .....j
Pruned oifs: ......
Leaves oifs: ......
Asserted oifs: ......
Outgoing oifs: .....o
Incoming : ...I..
TIMERS: Entry JP RS Assert VIFS: 0 1 2 3 4 5
205 60 0 0 0 0 0 0 0 0
--------------------------------- (*,*,G) ------------------------------------
Number of Groups: 4
Number of Cache MIRRORs: 8
------------------------------------------------------------------------------
Then I start client on 192.168.1.196 (vlan1):
vlc rtp://239.255.1.2:5004
but dont get a video. This works fine, if client and server are on the same VLAN.
Packet capture on pfsense vlan1 interface shows that the client is trying to join the group:
22:31:55.963481 IP (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 40, options (RA))
192.168.1.196 > 224.0.0.22: igmp v3 report, 1 group record(s) [gaddr 239.255.1.2 to_in { }]
22:31:56.735594 IP (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 40, options (RA))
192.168.1.196 > 224.0.0.22: igmp v3 report, 1 group record(s) [gaddr 239.255.1.2 to_in { }]
22:31:57.327523 IP (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 40, options (RA))
192.168.1.196 > 224.0.0.22: igmp v3 report, 1 group record(s) [gaddr 239.255.1.2 to_ex { }]
22:31:57.827784 IP (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 48, options (RA))
192.168.1.196 > 224.0.0.22: igmp v3 report, 2 group record(s) [gaddr 239.255.1.2 is_ex { }] [gaddr 224.0.0.251 is_ex { }]
22:31:57.955683 IP (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 40, options (RA))
192.168.1.196 > 224.0.0.22: igmp v3 report, 1 group record(s) [gaddr 239.255.1.2 to_ex { }]
22:32:11.647572 IP (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 48, options (RA))
192.168.1.196 > 224.0.0.22: igmp v3 report, 2 group record(s) [gaddr 239.255.1.2 is_ex { }] [gaddr 224.0.0.251 is_ex { }]
But I can't see anything in the firewall logs, though logging is enabled (see above).
Any ideas how to further debug this problem?