Some further explanation, for what it's worth. We have an OpenBSD 5.5 firewall in production that I would like to replace with pfSense. It connects a number of wireless clients to the internet. The existing firewall has been configured to shape traffic for each of the existing customers, however we now do the shaping on the customer premise, so we no longer need or wish to have any shaping rule on the firewall for individual customers.
The exception to this is customer A. Customer A has a wired connection to a backhaul radio, so we have no ability to shape their traffic on customer premise, and need to continue to do it in the firewall. Additionally, we need to shape all customer traffic to 290 mbps collectively, and VoIP traffic (also from the customers) to 10 mbps.
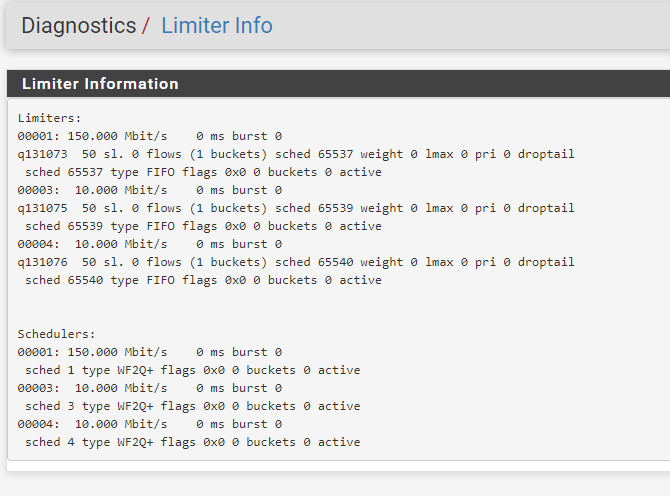
It's easy enough to create three limiters of 290, 100 and 10 mbit and apply these to 1:non-voip, 2:customer A, and 3:voip traffic respectively, but this doesn't prevent the scenario where customer A is using 100 mbps and the other customers use up to 290 mbps concurrently, for a total of 390 mbps of non-voip traffic. I need to be able to limit customer A to 100 mbps and all customers to 290 mbps in total at the same time.
Here is the existing code from the pf.conf file in production that I'm trying to port from OpenBSD.
queue rootq on { em0, em1 } bandwidth 300M max 300M
queue VoIP parent rootq bandwidth 10M max 10M
queue wispq parent rootq bandwidth 290M max 290M
queue deflt parent wispq bandwidth 100M max 100M default
queue customer_A parent wispq bandwidth 100M min 50M max 100M
queue customer_B parent wispq bandwidth 30M min 20M max 35M burst 40M for 500ms
queue customer_C parent wispq bandwidth 30M min 20M max 35M burst 40M for 500ms
As previously mentioned, I'm not trying to implement individual limits for customers B through Z in pfSense; it's the first 5 lines here that really matter. I included a couple more lines to illustrate the fact that all customers still need to fall under the 290 mbit parent queue or limiter.
Any recommendations on good/better/best ways to do this in pfSense are appreciated.