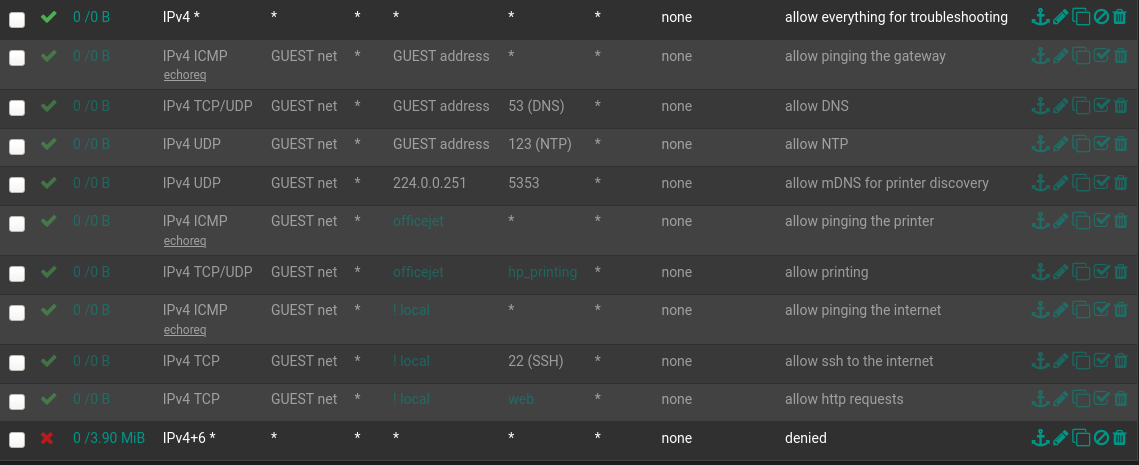
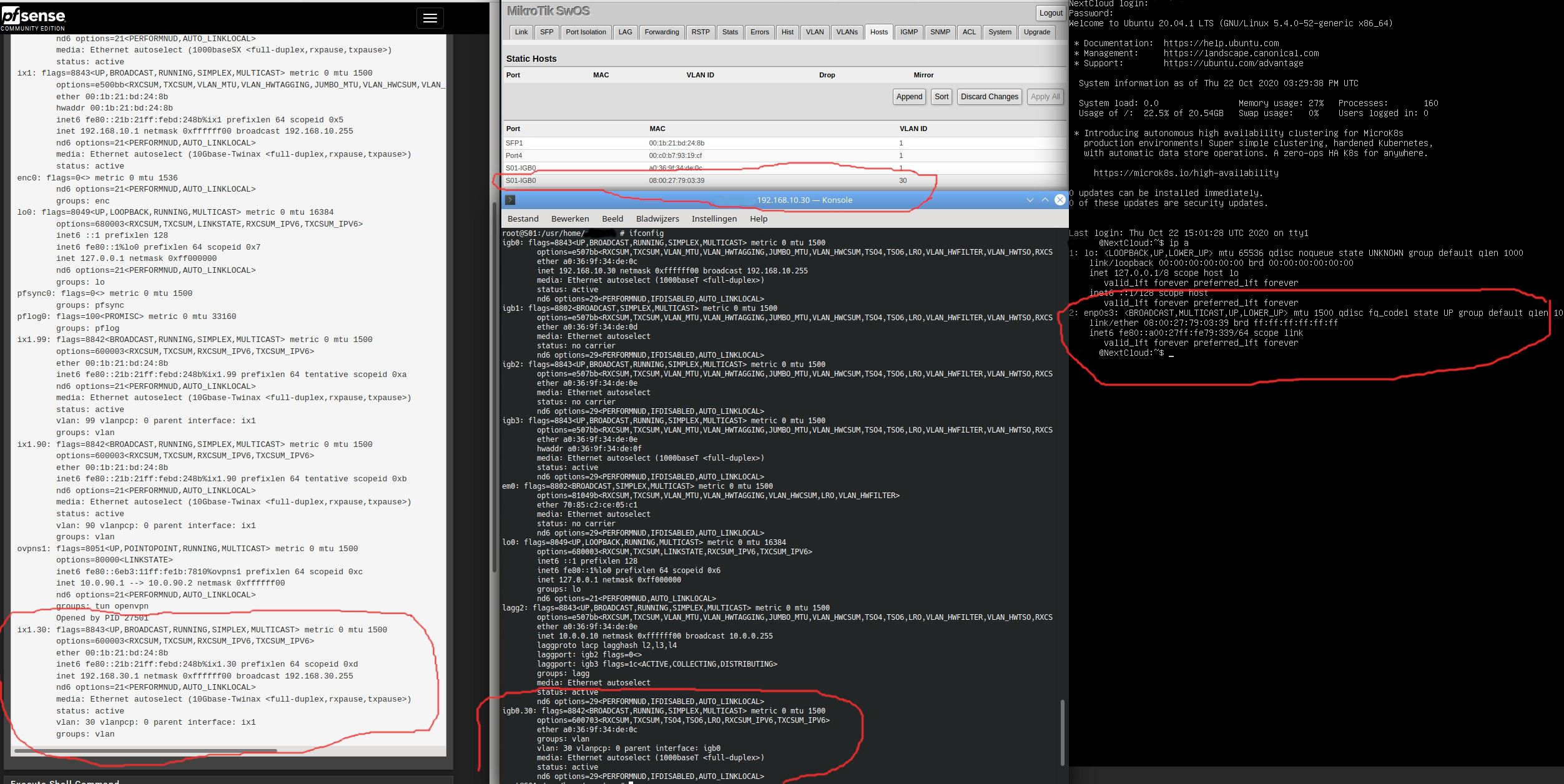
Well, no exactly, I already got noisy stuff under one subnet. I'm just curious if it can be achieved by merely using a transparent firewall technique while keeping the rest of the L2s separated. This is the first time I've thought about pfSense filtering below L3 I believe.
The switches I have, come with lots of stuff for multicast, fancy is actually a fitting word for it's a lot, from multicast filtering to routing to something in the middle (MVR) Plenty more features than for the other L2/L3 areas. But playing with these can easily lead to trouble, nothing too serious yet not far off--I traced a painfully slow network to the Avahi plugin when 2.4.5p1 was first released. It's been switched off since then.
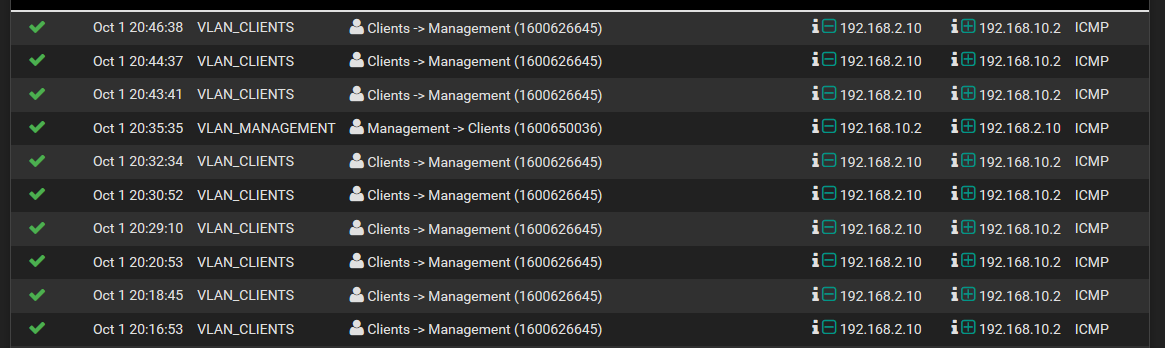
There is one multicast feature that I though seemed like a good compromise, in Ubiquiti-branded stuff it's called MVR, everywhere else is just Multicast VLAN, in Cisco it's probably named by its RFC # and then their licensed next to it. MVR is supposed to drop all multicast traffic regardless of source VLAN into a dedicated VLAN so traffic traffic won't bother other operations, setting up the ports' mode for it is contradictory in all documentation even it's got not router/source/whatever port designations. I tried so hard to make it work but I kept missing the almost-never-mentioned point: it only goes one-way, same as all other multicast protocols, they're designed to work in this waterfall-like fashion, as if source always were an IPTV operator for instances; remote from the Internet, doesn't care what you have to say. It's never a mesh or at least one-ways-for-all situation. The naming doesn't make it easier either, I know VLANs inside and out now, but when I go through these docs that aren't even for VLANs it makes me question how much do I really know about VLANs, ADHD kicks in and I've lost all day when I eventually l land in the document that triggered the spiral.
Not that useful for something like a remote app, or Spotify Connect/AirPlay, all relying heavily on multicast, treated like broadcast but even less smart. Some just assume your wireless network is the same as the wired one or the most infuriating are those incompatible Enterprise WPAs that expects the other device setting it up to connect to the same SSID otherwise it won't take it. It drives me insane this Harmony Hub I use for domo losses connectivity I have to go get a step ladder to pair it over Bluetooth, to then failing its "tests" to give you an IP input field only at the very end while you wait balancing on the ladder. 🤬
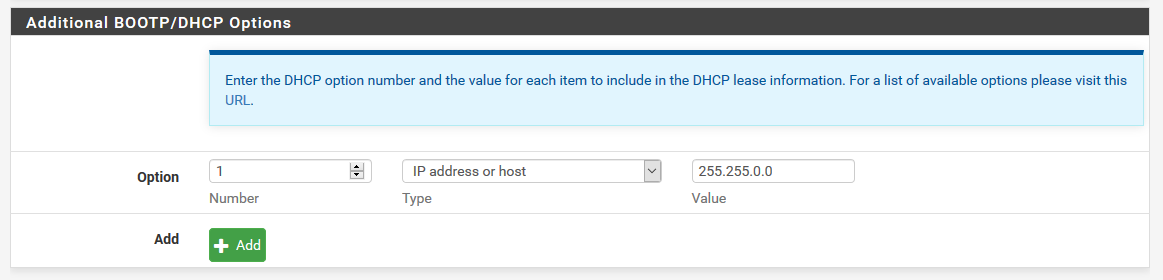
Got sidetracked there, sorry. Avahi and mDNS Repeater seem to be the only tools available for this but they're not really protocols, are they? They're included everywhere, well, Avahi is, but it's banned from switches it seems. They only router appliance I've seen that dealt with this type is in the Ubiquiti USG line, Ubiquiti as a brand sort of constantly readjusts its priorities (or has no direction), so it doesn't really count. So I'm exploring option to see what could be done if I didn't have or didn't know how to setup a RADIUS server (and pfSense didn't have one right in there). There's a lot more happening at L2 beyond ethenet so I'm curious.
I'd love to get my hands on one of those old ATM cards though I woulnd't know what to do with it 5 seconds later. I think my ISP is still using ATM despite delivering fiber I have this hunch. All of their naming still hints to ATM stuff. :)
I don't think you know how much I appreciate those little bits about Plex and preemptive filtering 'cause it's the first kind of thing that pops in my mind when I run into trouble. Thanks for the help!