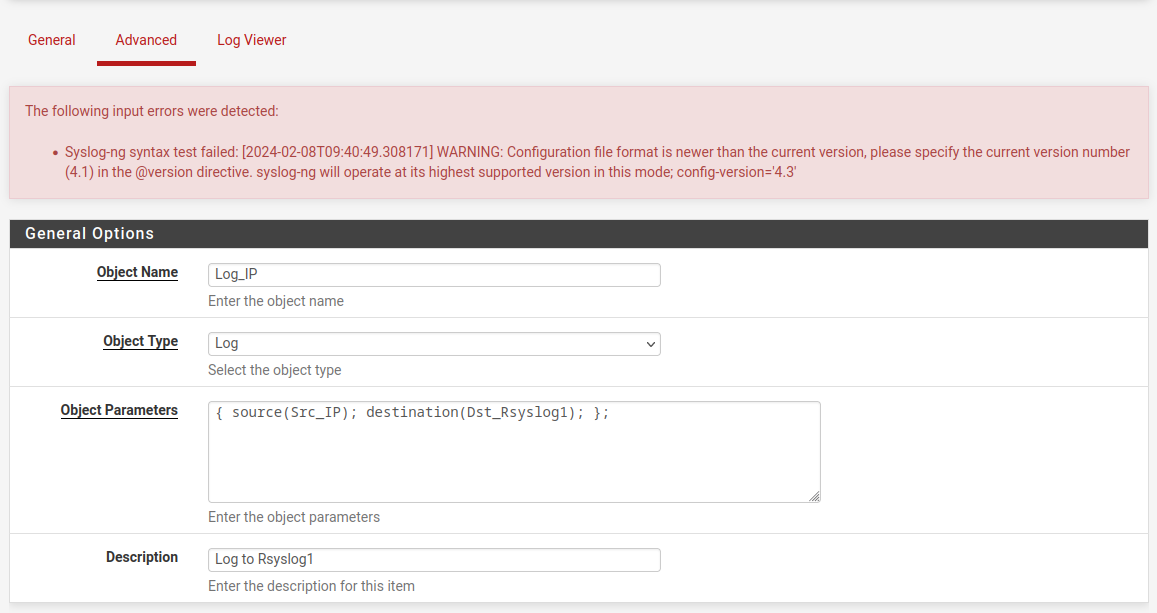
This is in Diagnostics → Crash Reporter:
Crash report begins. Anonymous machine information:
arm64
14.0-CURRENT
FreeBSD 14.0-CURRENT aarch64 1400094 #1 plus-RELENG_23_09_1-n256200-3de1e293f3a: Wed Dec 6 20:59:18 UTC 2023 root@freebsd:/var/jenkins/workspace/pfSense-Plus-snapshots-23_09_1-main/obj/aarch64/8ra4gn87/var/jenkins/workspace/pfSense-Plus-snapshots-23_
Crash report details:
PHP Errors:
[14-Feb-2024 23:41:45 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('Netgate pfSense...')
#3 /etc/inc/notices.inc(151): notify_all_remote('Netgate pfSense...')
#4 /etc/inc/config.lib.inc(239): file_notice('config.xml', 'Netgate pfSense...', 'pfSenseConfigur...', '')
#5 /etc/inc/config.lib.inc(695): restore_backup('/cf/conf/backup...')
#6 /usr/local/www/pkg_edit.php(233): write_config('[notes] Success...')
#7 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:41:45 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('PHP ERROR: Type...')
#3 /etc/inc/notices.inc(151): notify_all_remote('PHP ERROR: Type...')
#4 /etc/inc/config.lib.inc(1168): file_notice('phperror', 'PHP ERROR: Type...', 'PHP errors')
#5 [internal function]: pfSense_clear_globals()
#6 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:42:24 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('Netgate pfSense...')
#3 /etc/inc/notices.inc(151): notify_all_remote('Netgate pfSense...')
#4 /etc/inc/config.lib.inc(239): file_notice('config.xml', 'Netgate pfSense...', 'pfSenseConfigur...', '')
#5 /etc/inc/config.lib.inc(695): restore_backup('/cf/conf/backup...')
#6 /usr/local/www/pkg_edit.php(233): write_config('[notes] Success...')
#7 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:42:24 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('PHP ERROR: Type...')
#3 /etc/inc/notices.inc(151): notify_all_remote('PHP ERROR: Type...')
#4 /etc/inc/config.lib.inc(1168): file_notice('phperror', 'PHP ERROR: Type...', 'PHP errors')
#5 [internal function]: pfSense_clear_globals()
#6 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:43:03 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('Netgate pfSense...')
#3 /etc/inc/notices.inc(151): notify_all_remote('Netgate pfSense...')
#4 /etc/inc/config.lib.inc(239): file_notice('config.xml', 'Netgate pfSense...', 'pfSenseConfigur...', '')
#5 /etc/inc/config.lib.inc(695): restore_backup('/cf/conf/backup...')
#6 /usr/local/www/pkg_edit.php(233): write_config('[notes] Success...')
#7 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:43:03 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('PHP ERROR: Type...')
#3 /etc/inc/notices.inc(151): notify_all_remote('PHP ERROR: Type...')
#4 /etc/inc/config.lib.inc(1168): file_notice('phperror', 'PHP ERROR: Type...', 'PHP errors')
#5 [internal function]: pfSense_clear_globals()
#6 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:43:59 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('Netgate pfSense...')
#3 /etc/inc/notices.inc(151): notify_all_remote('Netgate pfSense...')
#4 /etc/inc/config.lib.inc(239): file_notice('config.xml', 'Netgate pfSense...', 'pfSenseConfigur...', '')
#5 /etc/inc/config.lib.inc(695): restore_backup('/cf/conf/backup...')
#6 /usr/local/www/pkg_edit.php(233): write_config('[notes] Success...')
#7 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:43:59 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('PHP ERROR: Type...')
#3 /etc/inc/notices.inc(151): notify_all_remote('PHP ERROR: Type...')
#4 /etc/inc/config.lib.inc(1168): file_notice('phperror', 'PHP ERROR: Type...', 'PHP errors')
#5 [internal function]: pfSense_clear_globals()
#6 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:52:39 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('Netgate pfSense...')
#3 /etc/inc/notices.inc(151): notify_all_remote('Netgate pfSense...')
#4 /etc/inc/config.lib.inc(239): file_notice('config.xml', 'Netgate pfSense...', 'pfSenseConfigur...', '')
#5 /etc/inc/config.lib.inc(695): restore_backup('/cf/conf/backup...')
#6 /usr/local/www/pkg_edit.php(233): write_config('[notes] Success...')
#7 {main}
thrown in /etc/inc/util.inc on line 3748
[14-Feb-2024 23:52:39 US/East-Indiana] PHP Fatal error: Uncaught TypeError: array_path_enabled(): Argument #1 ($arr) must be of type array, int given, called in /etc/inc/config.lib.inc on line 1264 and defined in /etc/inc/util.inc:3748
Stack trace:
#0 /etc/inc/config.lib.inc(1264): array_path_enabled(-1, 'notifications/s...', 'disable')
#1 /etc/inc/notices.inc(379): config_path_enabled('notifications/s...', 'disable')
#2 /etc/inc/notices.inc(662): notify_via_smtp('PHP ERROR: Type...')
#3 /etc/inc/notices.inc(151): notify_all_remote('PHP ERROR: Type...')
#4 /etc/inc/config.lib.inc(1168): file_notice('phperror', 'PHP ERROR: Type...', 'PHP errors')
#5 [internal function]: pfSense_clear_globals()
#6 {main}
thrown in /etc/inc/util.inc on line 3748
No FreeBSD crash data found.