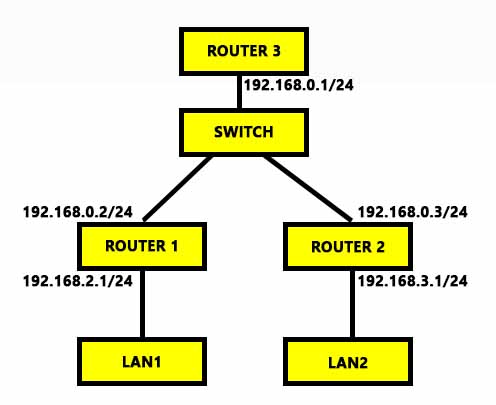
@kpa Here is parts of my configs:
Client
[image: 1530578082042-5d158d98-e6c7-4eb1-ae50-31fef1ec71e6-%D0%B8%D0%B7%D0%BE%D0%B1%D1%80%D0%B0%D0%B6%D0%B5%D0%BD%D0%B8%D0%B5-resized.png]
Server ccd
[image: 1530578172008-e3ed8f4c-afaf-4e63-808a-c1c90d55680d-%D0%B8%D0%B7%D0%BE%D0%B1%D1%80%D0%B0%D0%B6%D0%B5%D0%BD%D0%B8%D0%B5.png]
Server server.conf
[image: 1530578205194-a56d5260-f8e8-45d2-9835-f8f3b837f919-%D0%B8%D0%B7%D0%BE%D0%B1%D1%80%D0%B0%D0%B6%D0%B5%D0%BD%D0%B8%D0%B5.png]
Server log before client connected
[image: 1530578284083-ced1dbe8-b9e6-48de-ac6f-f855f726f04c-%D0%B8%D0%B7%D0%BE%D0%B1%D1%80%D0%B0%D0%B6%D0%B5%D0%BD%D0%B8%D0%B5-resized.png]
Server log after client connected
[image: 1530578685871-c9afca24-742f-47a6-a23e-ca8501004b07-%D0%B8%D0%B7%D0%BE%D0%B1%D1%80%D0%B0%D0%B6%D0%B5%D0%BD%D0%B8%D0%B5-resized.png]
Client log
Jul 3 07:45:33 openvpn 60153 Initialization Sequence Completed
Jul 3 07:45:33 openvpn 60153 /usr/local/sbin/ovpn-linkup ovpnc2 1500 1570 10.10.0.2 255.255.255.0 init
Jul 3 07:45:33 openvpn 60153 /sbin/route add -net 10.10.0.0 10.10.0.1 255.255.255.0
Jul 3 07:45:33 openvpn 60153 /sbin/ifconfig ovpnc2 10.10.0.2 10.10.0.1 mtu 1500 netmask 255.255.255.0 up
Jul 3 07:45:33 openvpn 60153 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Jul 3 07:45:33 openvpn 60153 TUN/TAP device /dev/tun2 opened
Jul 3 07:45:33 openvpn 60153 TUN/TAP device ovpnc2 exists previously, keep at program end
Jul 3 07:45:33 openvpn 60153 ROUTE_GATEWAY CLIENT_EX_IP/255.255.255.192 IFACE=em0 HWADDR=00:0c:29:6c:7e:79
Jul 3 07:45:33 openvpn 60153 Incoming Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication
Jul 3 07:45:33 openvpn 60153 Incoming Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key
Jul 3 07:45:33 openvpn 60153 Outgoing Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication
Jul 3 07:45:33 openvpn 60153 Outgoing Data Channel: Cipher 'AES-128-CBC' initialized with 128 bit key
Jul 3 07:45:33 openvpn 60153 OPTIONS IMPORT: route-related options modified
Jul 3 07:45:33 openvpn 60153 OPTIONS IMPORT: --ifconfig/up options modified
Jul 3 07:45:33 openvpn 60153 OPTIONS IMPORT: timers and/or timeouts modified
Jul 3 07:45:33 openvpn 60153 PUSH: Received control message: 'PUSH_REPLY,route-gateway 10.10.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.10.0.2 255.255.255.0'
Jul 3 07:45:33 openvpn 60153 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Jul 3 07:45:32 openvpn 60153 [server] Peer Connection Initiated with [AF_INET]VPN_SERVER_EXT_IP:PORT
Jul 3 07:45:32 openvpn 60153 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Jul 3 07:45:32 openvpn 60153 VERIFY OK: depth=0, C=RU, ST=TO, L=Tomsk, O=Kireva, OU=IT_dept, CN=server, name=oneandoneserver, emailAddress=winmasta@kireva.com
Jul 3 07:45:32 openvpn 60153 VERIFY EKU OK
Jul 3 07:45:32 openvpn 60153 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Jul 3 07:45:32 openvpn 60153 Validating certificate extended key usage
Jul 3 07:45:32 openvpn 60153 VERIFY KU OK
Jul 3 07:45:32 openvpn 60153 VERIFY OK: depth=1, C=RU, ST=TO, L=Tomsk, O=Kireva, OU=IT_dept, CN=Kireva CA, name=oneandoneserver, emailAddress=winmasta@kireva.com
Jul 3 07:45:31 openvpn 60153 TLS: Initial packet from [AF_INET]VPN_SERVER_EXT_IP:PORT, sid=446f96a7 9c4b7ab0
Jul 3 07:45:31 openvpn 60153 UDPv4 link remote: [AF_INET]VPN_SERVER_EXT_IP:PORT
Jul 3 07:45:31 openvpn 60153 UDPv4 link local (bound): [AF_INET]CLIENT_EXT_IP:0
Jul 3 07:45:31 openvpn 60153 Socket Buffers: R=[42080->42080] S=[57344->57344]
Jul 3 07:45:31 openvpn 60153 TCP/UDP: Preserving recently used remote address: [AF_INET]VPN_SERVER_EXT_IP:PORT
Jul 3 07:45:31 openvpn 60153 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Jul 3 07:45:31 openvpn 60153 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Jul 3 07:45:31 openvpn 60153 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jul 3 07:45:31 openvpn 60153 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client2.sock
Jul 3 07:45:31 openvpn 60082 library versions: OpenSSL 1.0.2m-freebsd 2 Nov 2017, LZO 2.10
Jul 3 07:45:31 openvpn 60082 OpenVPN 2.4.4 amd64-portbld-freebsd11.1 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Oct 8 2017
Jul 3 07:45:31 openvpn 60825 SIGTERM[hard,] received, process exiting
Jul 3 07:45:31 openvpn 60825 /usr/local/sbin/ovpn-linkdown ovpnc2 1500 1570 10.10.0.2 255.255.255.0 init
Jul 3 07:45:31 openvpn 60825 Closing TUN/TAP interface
Jul 3 07:45:31 openvpn 60825 event_wait : Interrupted system call (code=4)
Jul 3 07:45:29 openvpn 60825 MANAGEMENT: Client disconnected
Jul 3 07:45:29 openvpn 60825 MANAGEMENT: CMD 'status 2'
Jul 3 07:45:29 openvpn 60825 MANAGEMENT: CMD 'state 1'
Jul 3 07:45:29 openvpn 7621 MANAGEMENT: Client disconnected
Jul 3 07:45:29 openvpn 60825 MANAGEMENT: Client connected from /var/etc/openvpn/client2.sock
Jul 3 07:45:29 openvpn 7621 MANAGEMENT: CMD 'status 2'
Jul 3 07:45:29 openvpn 7621 MANAGEMENT: CMD 'state 1'
Jul 3 07:45:29 openvpn 7621 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock
111
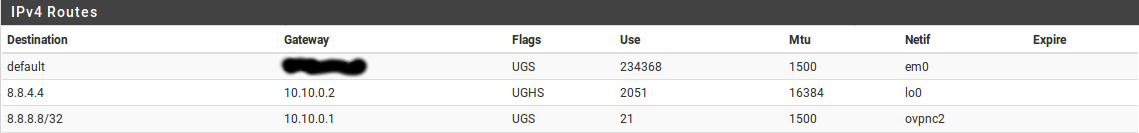 2
0 Votes9 Posts1k Views
2
0 Votes9 Posts1k Views