It sounds to me like you have all the nuts and bolts necessary to build a pretty decent segmented network.
There's no mention of your WiFi gear, but regardless of vendor, as long as it supports VLANs you'll good to go with that component too.
Personally, I have networks for servers, kids, media, IoT, guests, etc.
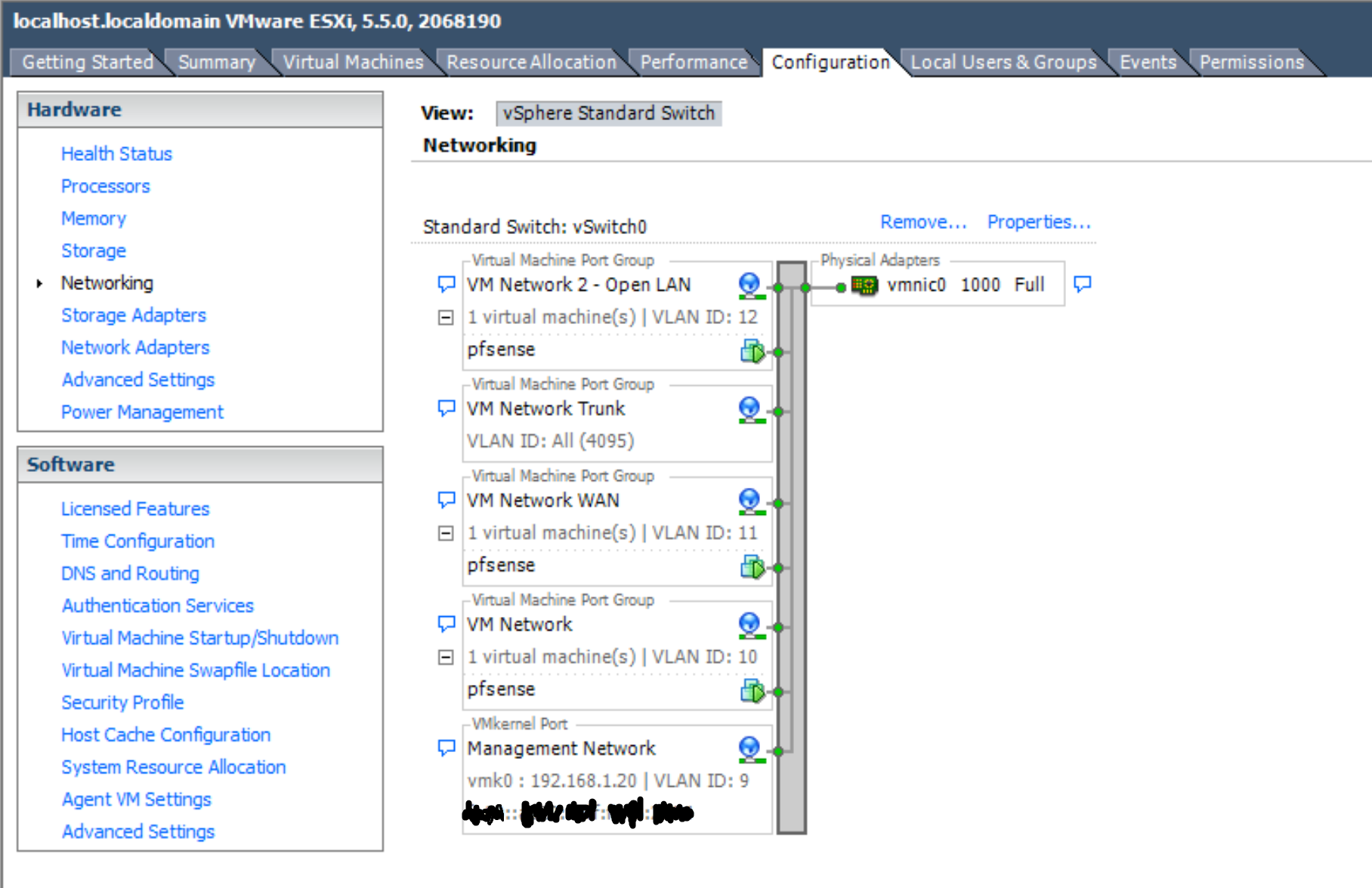
I have a fairly beefy server (16-core, 96GB RAM, 12TB RAID 5) running ESXi with everything virtualized (including pfSense).
Servers and printers share the same network.
Parents devices have their own VLAN with DHCP (responds only to named reservations) and rules allowing access to pretty much anything.
Each kids has their own VLAN with DHCP (responds only to named reservations) and rules controlling what they can access, and schedules to ensure they get some sleep! - The WiFi has one SSID to rule them all, it is integrated with AD and does per user RADIUS VLAN assignment, but that's just icing on the cake.
Media devices, Roku, PS4, etc have a media VLAN again with DHCP, rules and schedules.
IoT devides, fridge, thermostat, cameras, etc have their own VLAN with DHCP and rules (generally allow to Internet only)
Guests have a VLAN (accessed via the WiFi) with DHCP and captive portal, and rules. (I also added a MAC filter to the WiFi to prevent the kid's devices from using the Guest WiFi and bypassing the above controls).
Several LAB VLANs where I can spin up VMs to test various things
Some planning will certainly be required:
Figure out how many VLANs you will need. Keep in mind that while you can make it super complicated, managing it also becomes complicated as does troubleshooting.
Each VLAN will need a separate non-overlapping subnet.
pfSense will be the default gateway for each subnet.
Each subnet will need rules to indicate what it is allowed to access (keep in mind that any other interfaces besides LAN have no default rules, so you'll need to create some).
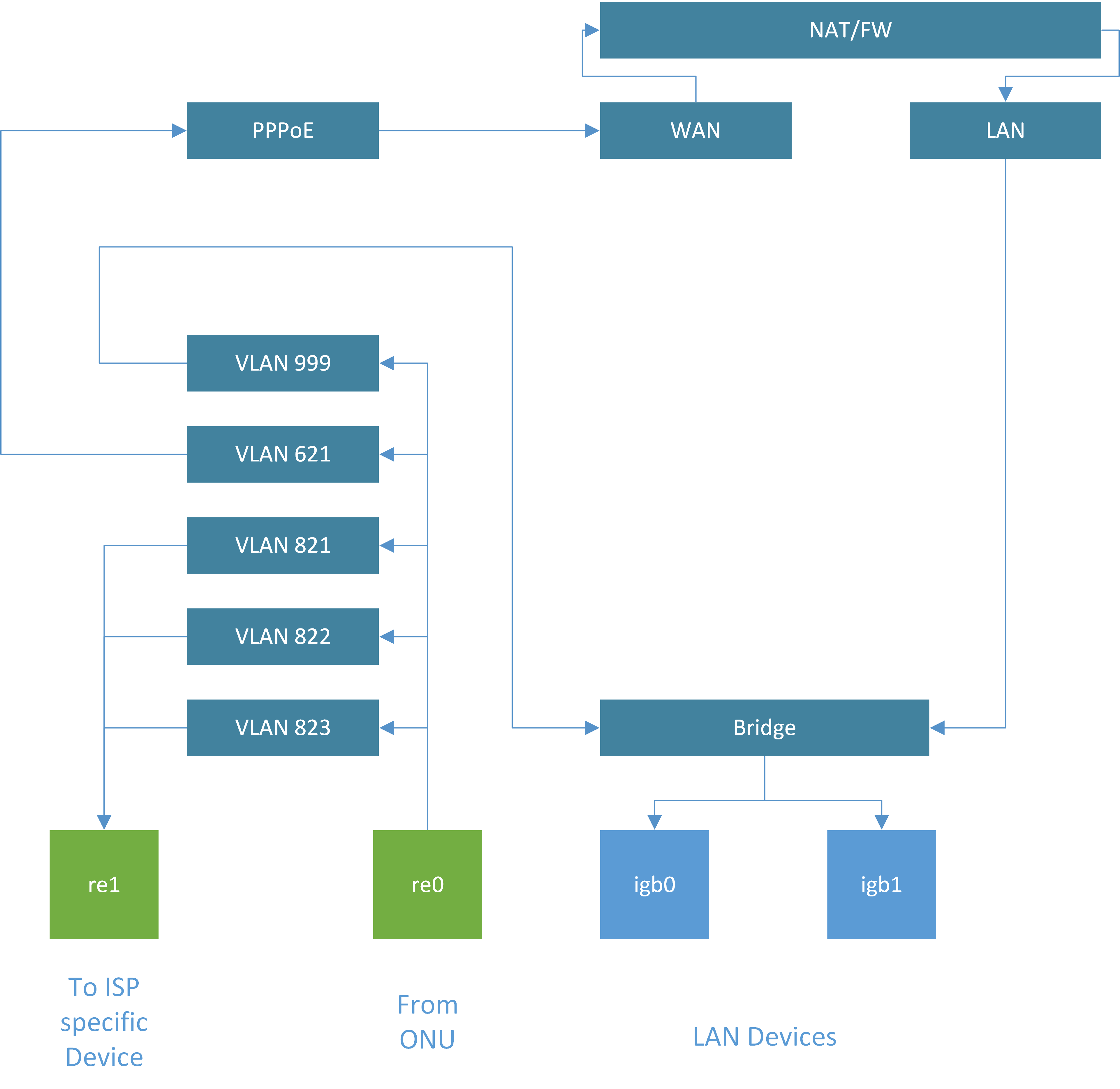
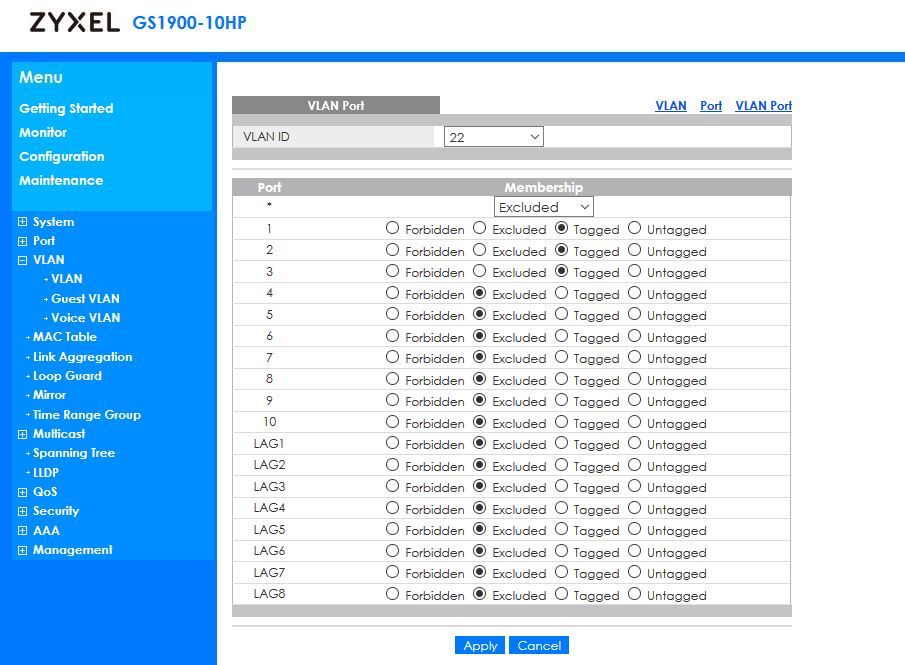
You could add VLANs to the LAN interface, or natively to the other interfaces, it makes no difference unless you are passing a lot of traffic between two different VLANs, in which case it might make sense to have them on separate ports. Configure the managed switch with the VLANs and assign them to the port(s) facing pfSense.
From there move your devices into the desired VLANs (IP renumbering will be required), and create rules as needed.
Lastly, test and test some more.